How to Publish a non-claims Aware Web Applications using Microsoft UAG 2010.
This blog is about how to publish a non-claims aware application through UAG and take benefit of SSO functionality of UAG. We will be publishing ADFS server and Application through UAG server. To take benefit of “Single Sign On” feature of UAG we will use KCD, I have configured Kerberos authentication for the web server and we will transform the incoming claims to “Lead User Value = Name” to perform KCD.
End Goal: - The users of the federated domain “Contoso.com” should be able to access the non-claims aware application published through UAG server using Kerberos constrained delegation. We will need a shadow account for the user from the “contoso.com”. The only drawback for this approach is that we need to create/maintain the shadow accounts in Active Directory “Mslab.com” domain for the users of “Contoso.com” domain.
Summary: We have a UAG 2010 server which is publishing ADFS server and we consume the ADFS claims to achieve SSO using Kerberos constrained delegation. Before we configure the ADFS trunk on UAG server we need to ensure that we have a federation trust with the partners ADFS server. Assuming all the configurations related to ADFS are in place, in this blog, I will be more focusing on the configuration of UAG trunk and prerequisites related to UAG server.
In this example, we have 2 separate domains, “MSLAB.Com” and “CONTOSO.Com”. The UAG 2010 server and Non-claims aware application (IIS Server) is part of Mslab.com domain. The intention is to access the non-claims aware application from internet using the user account “contoso/fs” of Contoso.com domain.
To accomplish the above goal, we will be publishing ADFS and non-claims aware application on the same UAG server trunk. Configurations required on UAG and ADFS server consists of: -
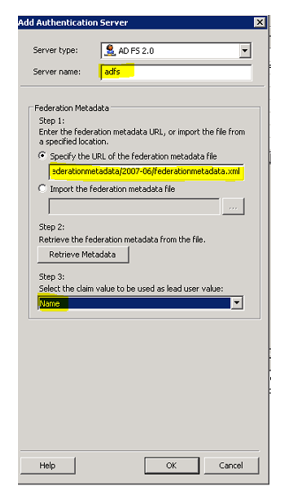
- Creating ADFS authentication repository on UAG server.
- Creating ADFS trunk on UAG server.
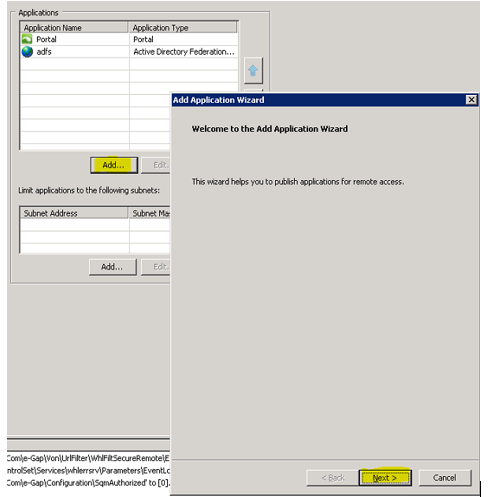
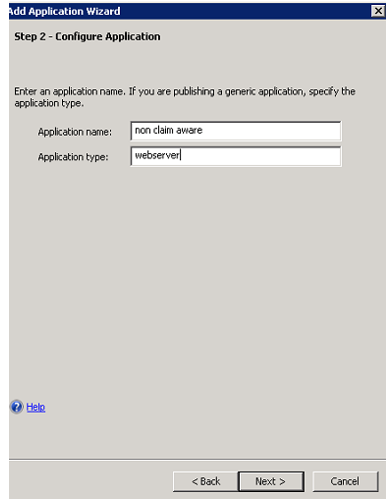
- Publishing non claims aware application on UAG server.
- Adding UAG as relying party trust in ADFS.
** A. Creating ADFS authentication repository on UAG server: -**
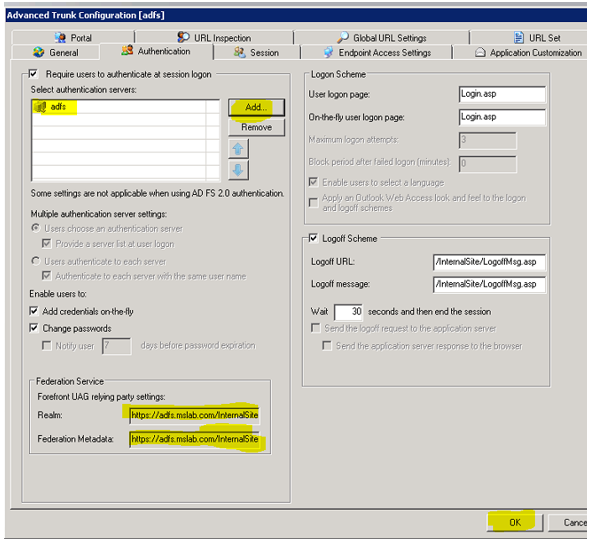
B. Creating ADFS trunk on UAG Server: - Creating ADFS trunk is a quick task, please refer the screenshots below. I have skipped few steps to reduce the content.
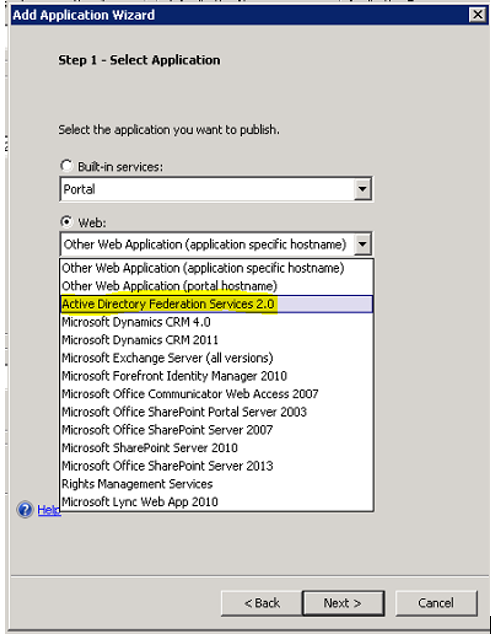
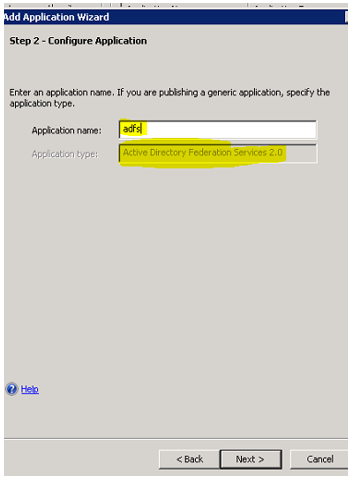
C. Publishing non claims aware application on UAG: - You may either use portal specific or application specific type to publish the application. Again, I have skipped few steps to reduce blog content. For this application we need to make sure we define Application SPN as “http/*” and choose value for “use the value for this claim type as the shadow account user name for KCD when using the federated authentication” by specifying on the authentication tab of application.
D. Adding UAG as relying party trust in ADFS: -
To add UAG as relying party, we will need to copy “FederationMetadata.xml” file from UAG server to the ADFS server.
Location: - The file will be created during Forefront UAG activation and is located in the following folder: ...\Microsoft Forefront Unified Access Gateway\von\InternalSite\ADFSv2Sites\trunk_name>\FederationMetadata\2007-06
See this link for more information http://technet.microsoft.com/en-us/library/gg274305.aspx





Logs from UAG Web Monitor: UAG web monitor becomes a handy tool to track the logs and it clearly shows us process of authentication and application access, at the same time in logs we can clearly observe the ADFS security token creation, validation and received.
Information 07/01/2016 17:32:02 5 Application Accessed Application adfs (S) UAG01 The application non claim aware was accessed on trunk adfs; Secure=1 with user name CONTOSO\fs and session ID EB911C5E-F3D5-45B3-B4EF-0F12AAA9193B.
* Information 07/01/2016 17:32:00 5 Application Accessed Application adfs (S) UAG01 The Application Portal was accessed on trunk adfs; Secure=1 with user name CONTOSO\fs and session ID EB911C5E-F3D5-45B3-B4EF-0F12AAA9193B.*
* Information 07/01/2016 17:31:59 153 WS-FAM Security Token Received Security adfs UAG01 WS-FAM: The security token was received. Session ID: EB911C5E-F3D5-45B3-B4EF-0F12AAA9193B, Trunk name: adfs.*
* Information 07/01/2016 17:31:59 154 WS-FAM Security Token Validated Security adfs UAG01 WS-FAM: The security token was validated. Session ID: EB911C5E-F3D5-45B3-B4EF-0F12AAA9193B, Trunk name: adfs, Number of identities: 1.*
* Information 07/01/2016 17:31:59 148 WS-FAM Security Token Created Security adfs UAG01 WS-FAM: Security token successfully created for user with lead user claim value CONTOSO\fs. Session ID: EB911C5E-F3D5-45B3-B4EF-0F12AAA9193B, Trunk name: adfs. *
* Information 07/01/2016 17:31:59 1 User Added To Session Session adfs (S) UAG01 The user CONTOSO\fs with source IP address 39.1.1.2 was added to session EB911C5E-F3D5-45B3-B4EF-0F12AAA9193B on trunk adfs (secure=1).*
* Information 07/01/2016 17:31:59 156 WS-FAM User Signed In Security adfs UAG01 WS-FAM: User with lead user claim value fs successfully signed in. Session ID: EB911C5E-F3D5-45B3-B4EF-0F12AAA9193B, Trunk name: adfs.*
* Information 07/01/2016 17:30:00 150 WS-FAM User Authentication Not Started Security adfs UAG01 WS-FAM: User authentication has not started. Session ID: EB911C5E-F3D5-45B3-B4EF-0F12AAA9193B, Trunk name: adfs.*
* Information 07/01/2016 17:30:00 147 WS-FAM Redirection To Identity Provider Security adfs UAG01 WS-FAM: Redirecting the request to the AD FS 2.0 server. The request might be redirected to a single server or to a load-balanced server farm. Session ID: EB911C5E-F3D5-45B3-B4EF-0F12AAA9193B, Trunk name: adfs.*
* Information 07/01/2016 17:29:34 60 Session Started Session adfs (S) UAG01 Session EB911C5E-F3D5-45B3-B4EF-0F12AAA9193B was started on trunk adfs (secure=1). The source IP address is 1.1.1.x.*
Reference articles: -
- Configuring single sign-on with Kerberos constrained delegation to non-claims-aware applications https://technet.microsoft.com/en-in/library/gg274291.aspx
- Setting up a trunk: - https://technet.microsoft.com/en-us/library/dd861407.aspx
- Steps to configure ADFS 2.0 and UAG for ADFS 2.0 Authentication and Authorization https://blogs.technet.microsoft.com/germany/2012/06/20/steps-to-configure-adfs-2-0-and-uag-for-adfs-2-0-authentication-and-authorization-teil-1/
- Why deploy Forefront UAG with AD FS 2.0? https://technet.microsoft.com/en-in/library/gg470575.aspx
- UAG and AD FS are Better Together – UAG as AD FS Proxy https://blogs.technet.microsoft.com/dmitrii/2011/09/01/uag-and-ad-fs-are-better-together-uag-as-ad-fs-proxy/
* *