Intune Integration with Cisco ISE
Intune Integration with Cisco ISE
Step 1: Configuring Microsoft Intune as an MDM server for ISE
Configuring Microsoft Intune as an MDM server for ISE is slightly differently from configuring other MDM servers. Use the following steps to configure ISE's connection to Azure and Azure's connection to ISE.
1. Get the public certificate from the Intune/Azure Active Directory tenant, and import it into ISE to support SSL handshake.
a. 1. Log on to the Intune Admin Console or Azure Admin console, whichever site has your tenant.
b. Use the browser to get the certificate details. For, example, with Internet Explorer:
1. Click on the lock symbol in the browers toolbar, then click View Certficates.
2. In the Certificate window, select the tab Certification Path.
3. Find Baltimore Cyber Trust root, and export the root cert.
c. In ISE, choose Administration > System > Certificates > Trusted Certificates, and import the root certificate that you just saved. Give the certificate a meaningful name, such as Azure MDM.
Step 2: Export the ISE system certificate
In the ISE console, go to Administration > Certificates > System Certificates > Generate Self Signed Certificate.
Export the self-signed certificate.
In a text editor, edit the exported certificate:
Delete ** -----BEGIN CERTIFICATE-----**
Delete ** -----END CERTIFICATE-----**
+ Ensure all of the text is a single line
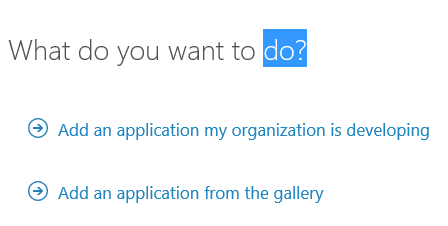
Step 3: Create an ISE App in your classic Azure AD Tenant
- Choose Add an application my organization is developing
2. Choose Web Application And/OR API
3. Fill the App properties information
SIGN-ON URL. The URL where users can sign in and use your app. You can change this later as needed.
APP ID URI. The URI used as a unique logical identifier for your app. The URI must be in a verified custom domain for an external user to grant your app access to their data in Windows Azure AD. For example, if your Microsoft tenant is contoso.onmicrosoft.com, the APP ID URI could be https://app.contoso.onmicrosoft.com.
4. Upload the ISE certificate into ISE
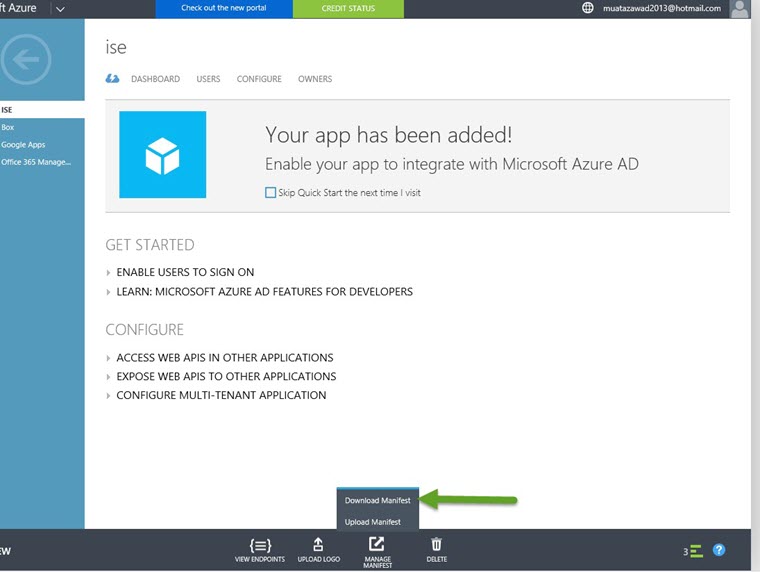
Download the manifest
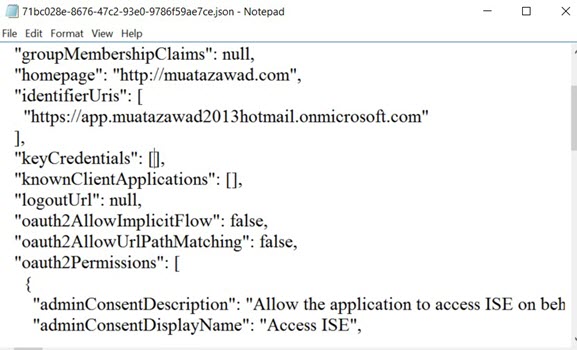
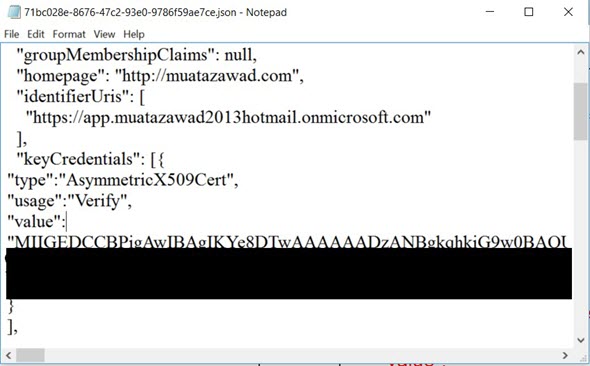
Insert text from step 2.3 to the manifest keycredentials”:[] field
Save file – Do Not change manifest name
Step 5: Upload the modified Json file to Azure App manifest
Step 6: Add Graph API and Intune API
For Microsoft Graph, choose the following:
- Application permissions: Read directory data
- Delegated permissions:
- Access user’s data anytime
- Sign users in
For the Microsoft Intune API, in Application permissions, choose Get device state and compliance from Intune.
Step 7: Add Azure MDM to ISE
Choose View Endpoints and copy the following values for use in configuring ISE settings:
+ Value in Azure AD portal
Corresponding field in ISE portal
Microsoft Azure AD Graph API endpoint
Auto Discovery URL
Oauth 2.0 Token endpoint
Token Issuing URL
Update your code with your Client ID
Client ID
*Token Audience is prepopulated