ASP.NET MVC Web Application With Federated Authentication
Back to [[Windows Azure Active Directory Solutions For Developers]]
Scenario
In this scenario you are developing ASP.NET MVC web application and you need to implement authentication using either Internet identities such as Live ID, Google, Facebook, Yahoo!, or OpenID 2.0 or enterprise identities managed by corporate Active Directory.

- Web Application is developed using ASP.NET MVC.
- Internet identities such as Live ID, Facebook, Google, Yahoo!, OpenID 2.0
- Enterprise identities managed by corporate Active Directory (AD)
Solution Approach
Windows Azure AppFabrice Access Control Service (ACS) is used to solve this scenario.
- ACS provides federation with Internet identities such as Live ID, Google, Facebook, Yahoo!, OpenID 2.0
- ACS provides federation with enterprise Active Directory (AD) via AD FS 2.0
- WIF is used to parse and validate the incoming tokens at the application.
Analysis
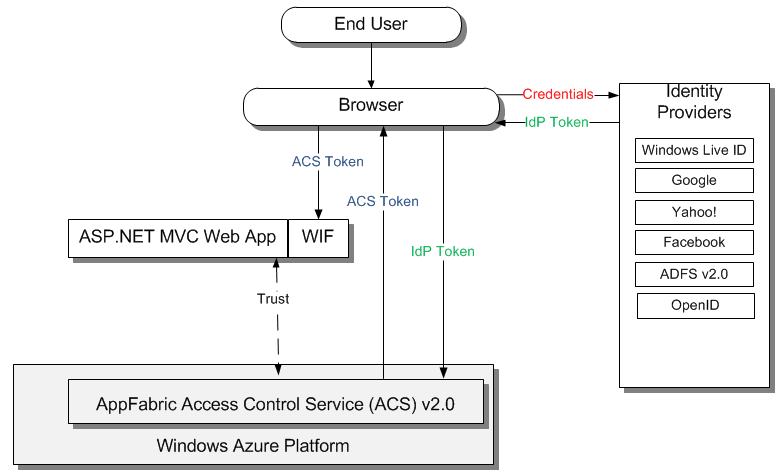
An end user tries to access the web application and the request is denied since WIF identifies no token. WIF redirects to the configured ACS namespace. ACS redirects the end user to the configured identity provider (IdP) where he submits his credentials. Upon successful authentication IdP issues a token and the end user seamlessly redirected to ACS where IdP's token is transformed into ACS token which is sent back to the end user. Then it is redirected back to the web application where the ACS' token validated by WIF. All that occurs seamlessly to the end user.
How-To's
- How To: Create My First Claims-Aware ASP.NET Application Using ACS
- How To: Host Login Pages in Your ASP.NET Web Application
- How To: Implement Claims Authorization in a Claims-Aware ASP.NET Application Using WIF and ACS
- How To: Implement Role Based Access Control (RBAC) in a Claims-Aware ASP.NET Application Using WIF and ACS
- How To: Configure Trust Between ACS and ASP.NET Web Applications Using X.509 Certificates
Code Samples
Resources
- Windows Azure AppFabric Access Control Service (ACS) Academy Videos
- Securing Web Applications with ACS
See Also
Other Languages
This article is also available in the following languages: