.Net Core 2: Managing Secrets in Web Apps
Introduction
As more and more applications moving into the cloud, the more and more securities that need to be handled carefully. Normally for WebApps whether it's a .NetFramework (or) .NetCore all the configuration and secrets were kept in `web.config` (or) `appsettings.json` all the connection string/ApplicationId/ApplicationSecrets/Passwords were stored in those configurations. But this should not be kept as directly in the configuration which is less secure.
Now, in this article, I'll explain how to manage secrets in your WebApps that is built on .Net Core 2.1. I'll majorly talk about 2 ways to achieve this.
- User Secrets
- Azure KeyVault Secrets
Ok, Let's Jump into the article
Prerequisites
- Visual Studio 2017 **Version 15.8.x **
- Microsoft Azure Subscription
If you look onto the 1st Pre-requisites.I've mentioned the version as bold, because of Microsoft released support for the secrets from the Version 15.8.
Appsetting.json (Storing Secrets in appsetting.json)
I've created a WebApp project called DemoSecrets, as a typical way all the configuration will get from appsetting.json
appsetting.json
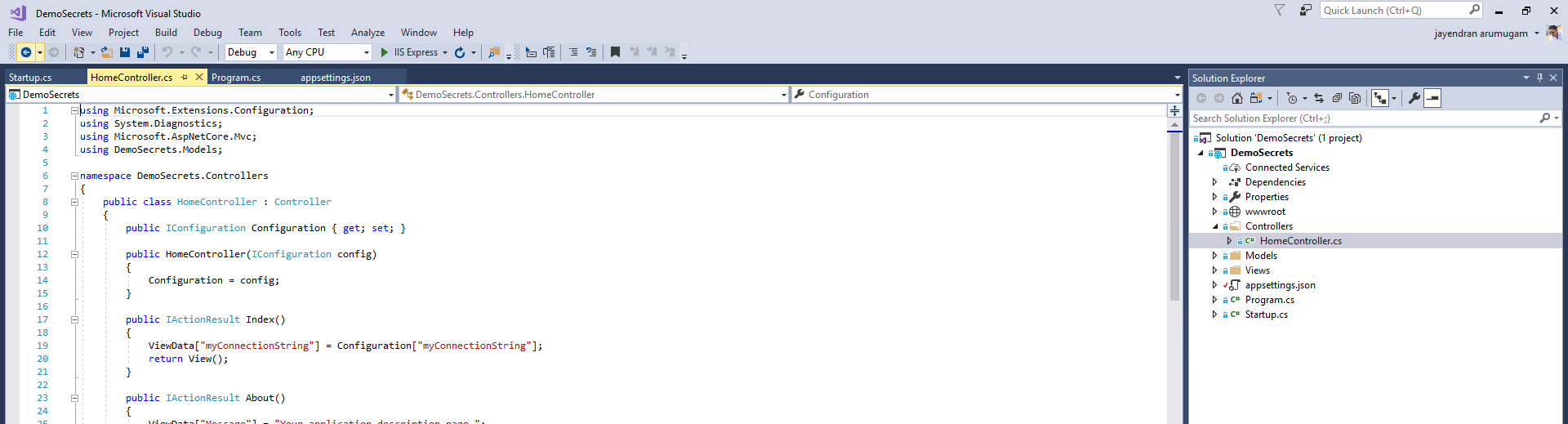
HomeController.cs
Slightly modified the homecontroller as below
1.using Microsoft.Extensions.Configuration;
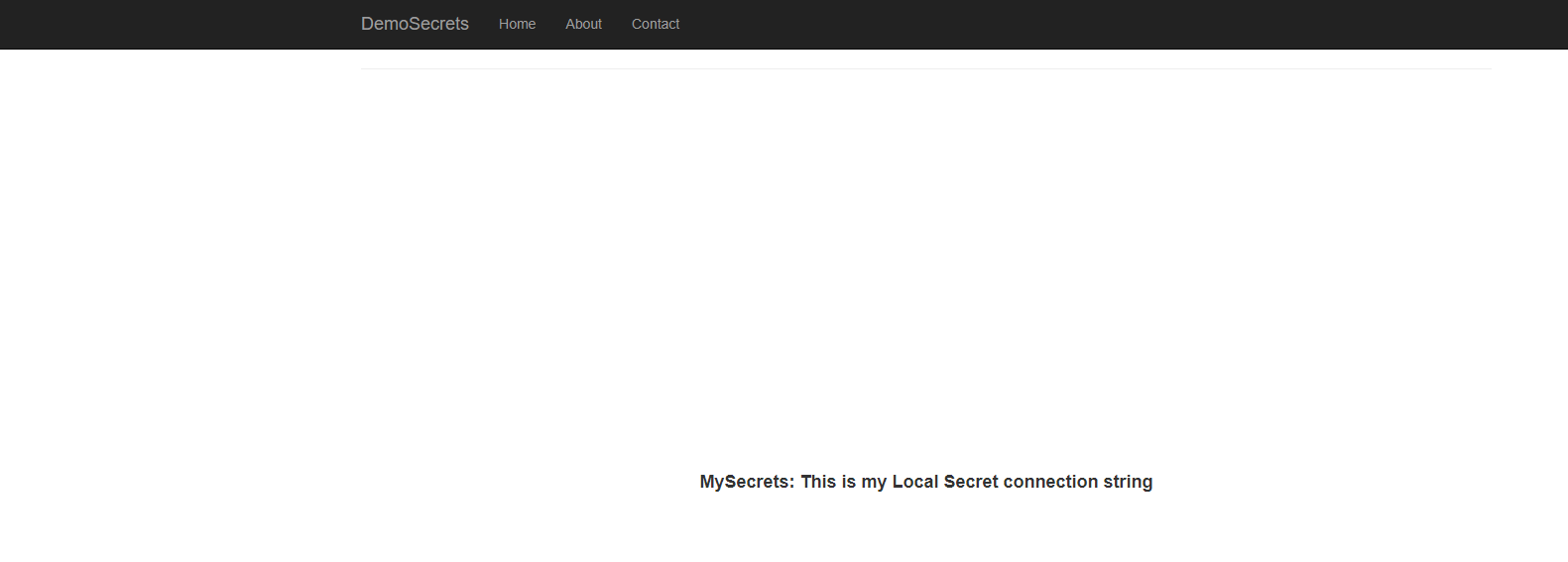
Finally the output
User Secrets( Storing secrets in secrets.json-local Machine)
This will be more useful for developers, the secrets that can be stored in their local machine as (secrets.json)
Make sure you have the latest VS Version(15.8.1) else the below menu will not available to you
Secrets.json
Store your the connection string here (for local development/debugging)
This secrets.json can be found at %APPDATA%\microsoft\UserSecrets\userSecretsId>\secrets.jsons
Now, this value will override your existing value of myconnectionstring in the appsetting.json
Finally output like
AzureKeyVault Secrets(Storing Secrets in AzureKeyVault)
In this step, we are going to store our secrets in AzureKeyVault(Which is the more secure way)
Install the below nugetPackage
1.Install-Package Microsoft.Extensions.Configuration.AzureKeyVault -Version 2.1.1
Then modify your Program.cs as below
- Create a new Azure KeyVault in Azure
- Create a new Application Registration in your Azure Active directory
- Register the Application into the KeyValut (AccessPolicies)
You can follow this tutorial on how to register your application to Azure key vault
Note the Client Id and Client Secret from the above steps ( We need to pass those from our application)
Create a new secret called myConnectionString in the AzureKeyVault
Add 3 new variables(below) in appsetting.json for accessing the AzureKeyVault (like below)
- Vault
- ClientId
- ClientSecret
Finally, the magic comes here, the output will be
Great! We did it. So all the secrets were stored/access securely from AzureKeyVault.
This way the value fo myConnectionString from azureKeyVault is overriding the local user secrets.json
So what will be the priority order of Overriding the config values?
- AzureKeyVault
- secrets.json
- appsetting.json
You can find the full source code of my DemoSecrets here