Azure: How to create a Conditional Access Policy
Creating a Conditional Access Policy is a pretty straight forward task on Azure. All what it takes it to proceed as follows :
Step 1 : Connect to Azure and go to Conditional Access – Policies then click on + New policy
Step 2 : Provide the name of the policy under Name
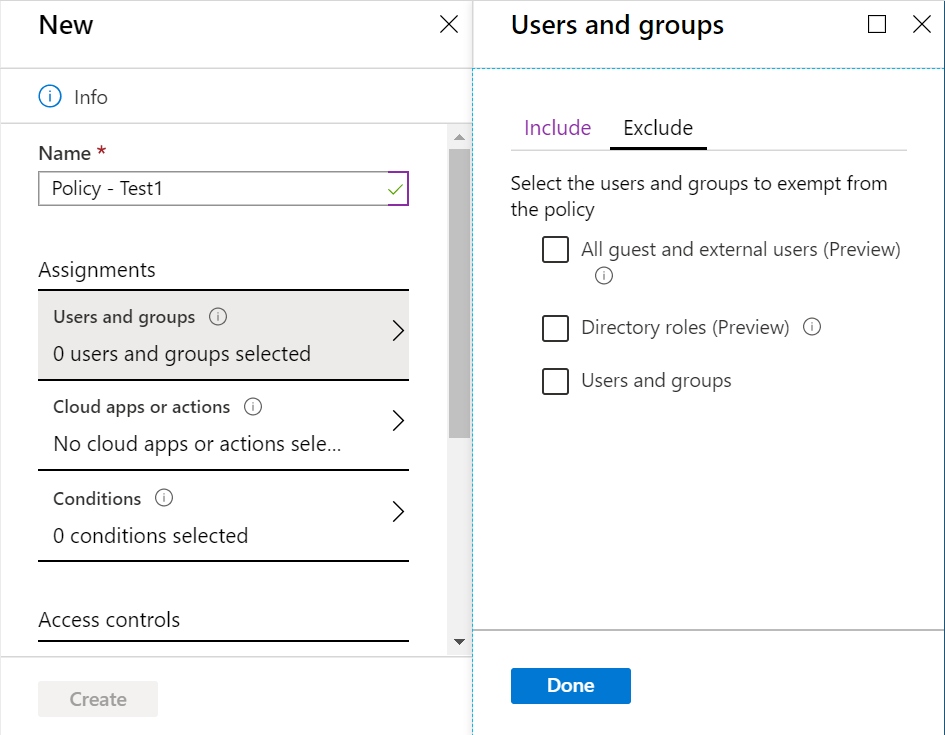
Step 3 : Click on Users and groups. The default section Include is about the users and groups who shall be included within the scope of the policy application. Here, you can choose between all users and specific users and groups which include :
- All guest and external users you have included in Azure AD
- Filtering based on specific roles in your directory
- Specific users and/or groups
As well, you can setup an exclusion, which excludes a set of users and groups, from the inclusion you have just setup. In a similar logic as above, you can select users and groups to exclude.
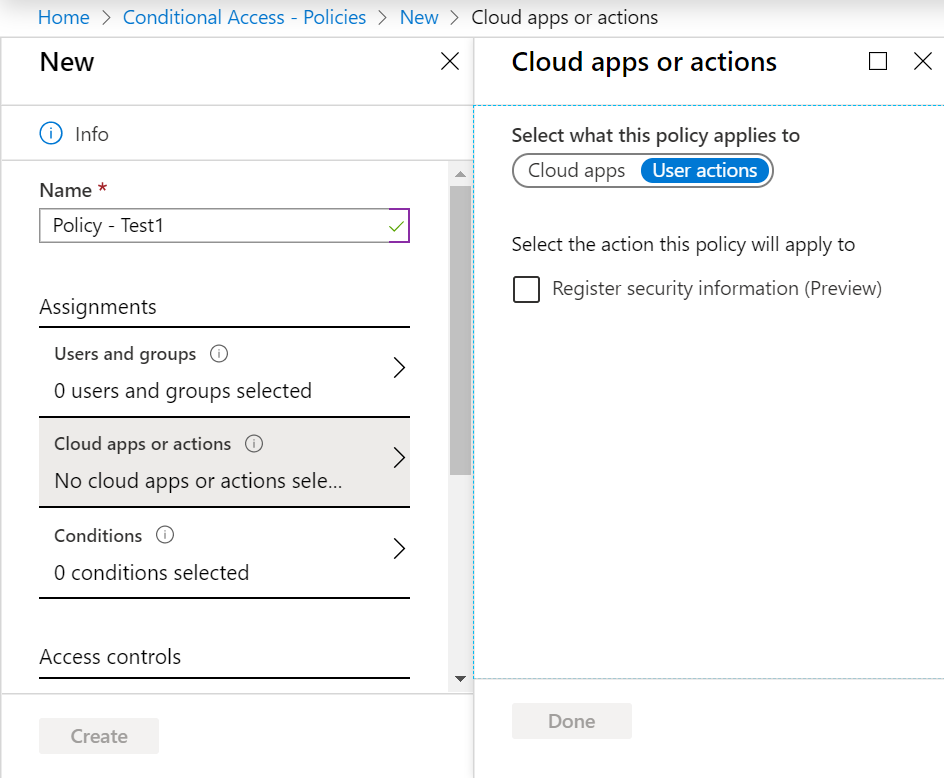
Step 4 : Click on Cloud apps or actions. The logic is always about inclusion and exclusion within the scope of the policy application. To start with the cloud apps, you can select that the policy applies to no app, to all of them or to specific ones you can select.
Of course, to get more granularity when you select all apps, you can make specific exclusions.
Step 5 : Click on Cloud apps or actions. The logic is always about inclusion and exclusion within the scope of the policy application. To start with the cloud apps, you can select that the policy applies to no app, to all of them or to specific ones you can select.
There is also User actions section which allows you to target only users are trying to register their security information. In other words, when users are registering for Azure Multi-Factor Authentication and self-service password reset, selecting the option Register security information would allow to define them part of the scope so that, as part of your policy, you can define when and how they can register. This is generally used to define from where these users can register that could be specific locations, like your organization offices.
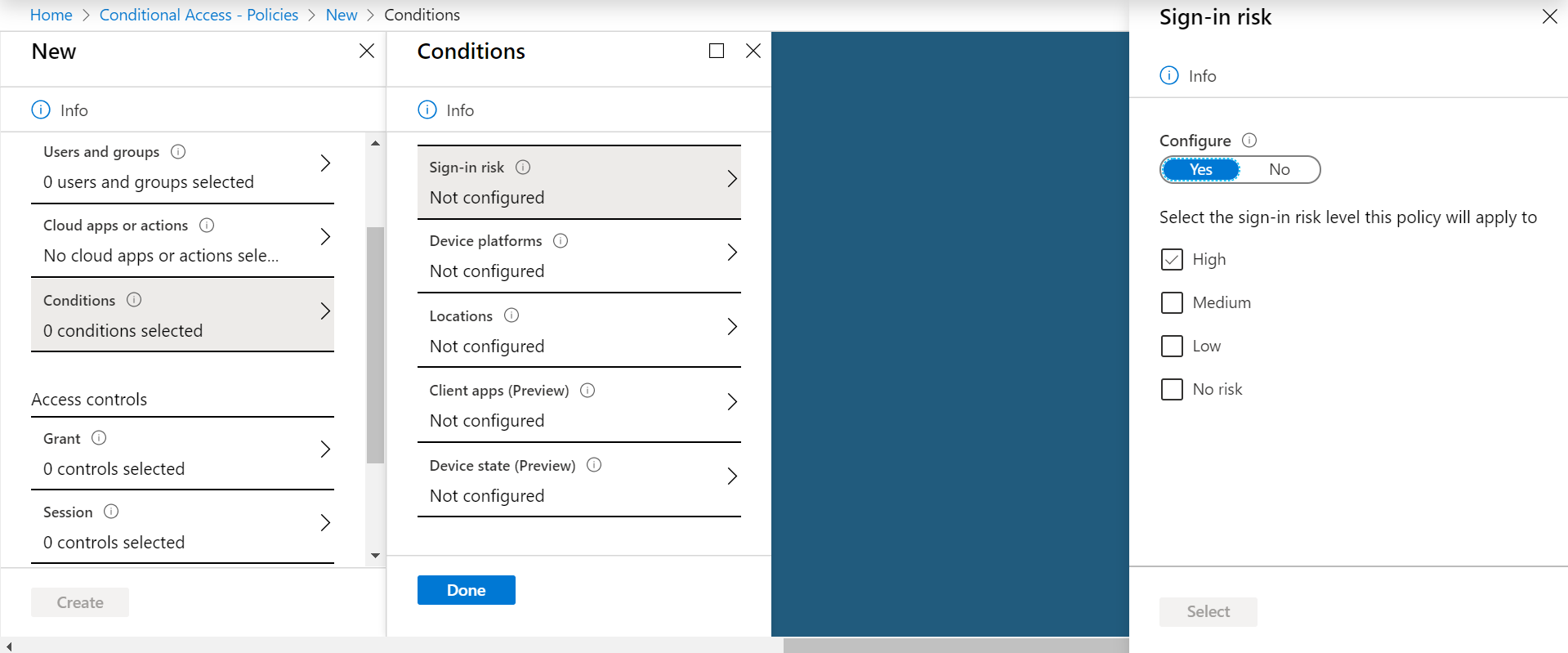
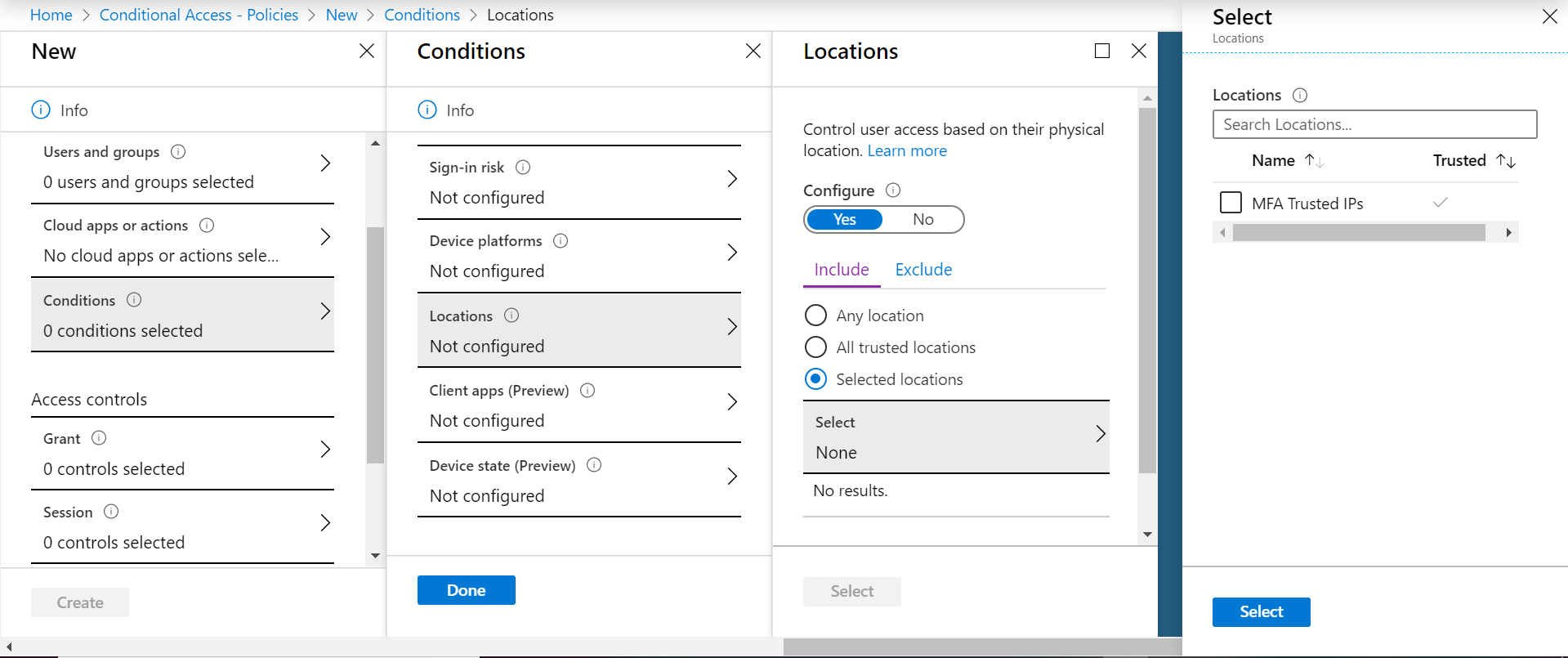
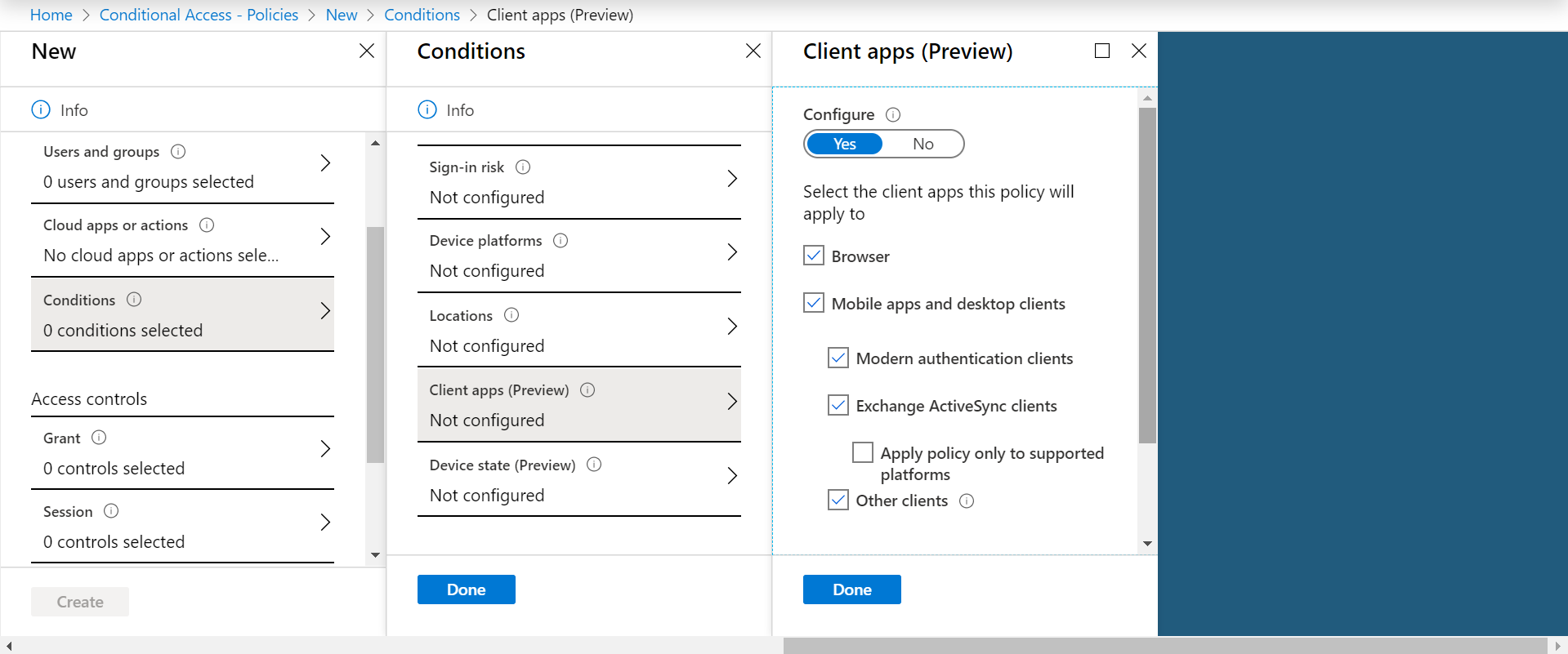
Step 6 : Click on Conditions to specify which additional criteria you would require to apply the policy
The first criteria Sign-in risk allows you to select users that have been flagged or not to be at risk, based on Microsoft data and analysis. This is a very powerful feature and you can select the different levels of risks : High, Medium, Low and No risk.
The second criteria is the Device platforms. With inclusions and exclusions, this feature allows you to include or exclude devices based on their operating systems. Of course, include devices first then exclude the others. The supported operating systems are Android, iOS, Windows iPhone, Windows and MacOS.
The third criteria is Locations. It allows you to specify locations to include that could be any locations, the ones you specified as trusted or specific ones you can select from the ones you created earlier. Same as before, you can setup exclusions.
The fourth criteria is Client apps. It allows you going granular in terms of applying the policy based on the client apps.
The last condition is Device state. By default, it accepts all device states but you can make two possible exclusions. First, you can exclude Device Hybrid Azure AD joined and Device marked as compliants which are two possible states of your devices that you may consider excluding depending on your policy.
Step 7 : All the steps above allowed you to specify your scope when applying the policy. This step focuses on what exactly you want to apply. Click on Grant and you will see a pretty simple set of actions. You can grant or block access.
If you wish to block access, you can setup requirements to be met so that you can set the target free and granted access. These requirements are to require multi-factor authentication (This is generally used to require multi-factor authentication when you are not in a safe area), to require device to be marked as compliant (This is generally used to require a minimum level of device compliance that you can define before allowing access to sensitive systems), ro required hybrid Azure AD joined device, require approved client app or to require app protection policy.
Of course, you can require one or all of these conditions to be true, which is what you can setup through the For multiple controls available configurations.
Step 8 : As well, you can focus on applying controls that over the session initated to your Azure environment. A very well description of these features is available at : /en-us/azure/active-directory/conditional-access/concept-conditional-access-session
Congrats ! Now, you are done. You have seen the available granularity and how powerful this feature is. If you think well about your threat scenarios, this feature will allow you introduce pretty strong protections while allowing you be granular in terms of applications.