Authentication methods using Azure Active Directory
Important
This is the Azure Sphere (Legacy) documentation. Azure Sphere (Legacy) is retiring on 27 September 2027, and users must migrate to Azure Sphere (Integrated) by this time. Use the Version selector located above the TOC to view the Azure Sphere (Integrated) documentation.
The Azure Sphere Public API (PAPI) supports multiple methods of user authentication and authorization in Azure Active Directory (AAD).
With Azure Active Directory, an application token can be used to authenticate and grant access to specific Azure resources from a user app, service, or automation tool by using the service principal or managed identity method for authentication.
Important
When you create a service principal you must protect the generated application credentials such as client secrets or client certificates. Be sure that you do not include the application credentials in your code or check the credentials into your source control. As an alternative, consider using managed identity to avoid the need to use credentials.
The following illustration shows the supported authentication methods using Azure Active Directory:
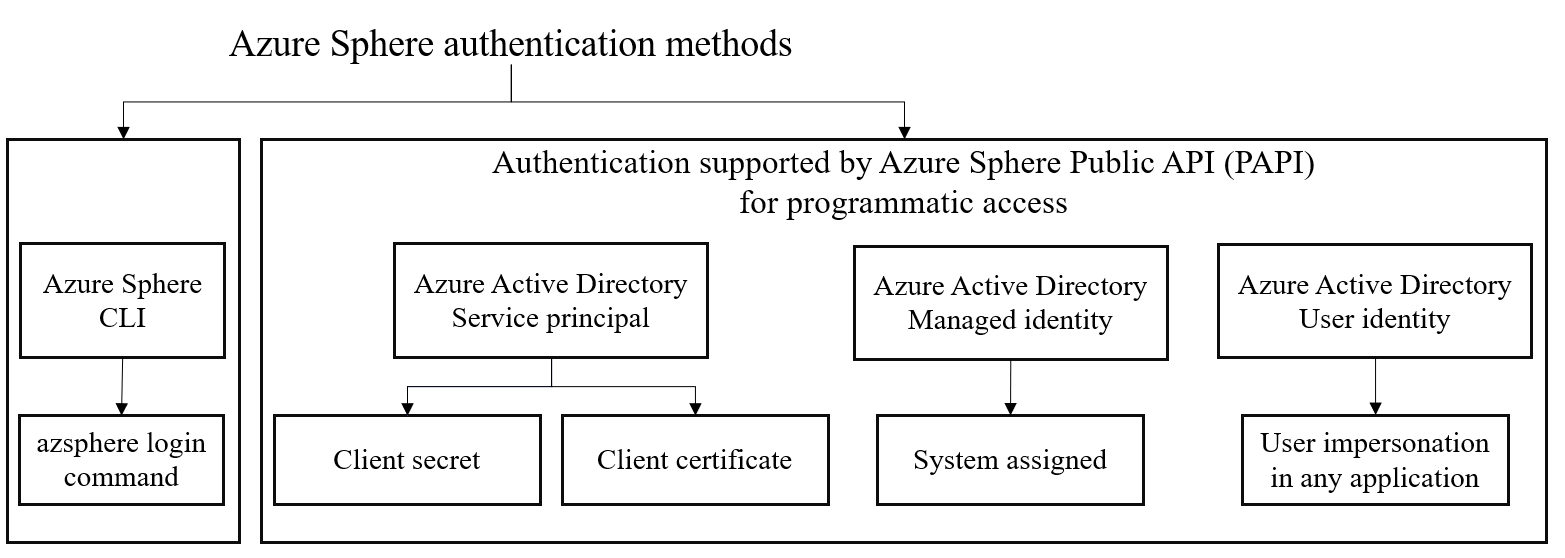
Service principal method
An Azure service principal can be set up to use a client secret or client certificate for authentication. Service principals are accounts not tied to any particular user, but can have permissions assigned through pre-defined roles. Authenticating with a service principal is the best way to write secure scripts or programs, allowing you to apply both permission restrictions and locally stored static credential information. For more information, see Azure service principal.
There are two options available for service principals: client secrets and client certificates. For more information, see Service principal authentication method.
Managed identity method
Azure managed identity can also be used to communicate with Azure Sphere Public API service. Managed identity is supported in various Azure services. The benefit of using a managed identity for Azure resources authentication method is that you don’t have to manage any client secrets or client certificates. For more information, see Managed identity for resource method.
User identity method
Using this method you do not need to authenticate using the Azure Sphere tenant. You can log in using the Azure Active Directory user identity. For more information, see User authentication method.
Add the Azure Sphere Public API Application ID to your Azure tenant
You first need to add the Azure Sphere Public API Application ID to your Azure tenant using a one-time setup:
Note
- Use a Global Administrator account for your Azure Active Directory (Azure AD) tenant to run this command.
- The value for the
AppIdparameter is static. - We recommended using
Azure Sphere Public APIfor the-DisplayNameso a common display name can be used across tenants.
Open an elevated Windows PowerShell Command Prompt window (run Windows PowerShell as an administrator) and run the following command to install the Azure AD Powershell module:
Install-Module AzureADSign in to Azure AD PowerShell with an admin account. Specify the
-TenantIdparameter to authenticate as a service principal:Connect-AzureAD -TenantId <Azure Active Directory TenantID><Azure Active Directory TenantID> represents the TenantID of the Azure Active directory. For more information, see How to find your Azure Active Directory tenant ID.
Create the service principal and connect it to the
Azure Sphere Public APIapplication by specifying the Azure Sphere Public API Application ID as described below:New-AzureADServicePrincipal -AppId 7c209960-a417-423c-b2e3-9251907e63fe -DisplayName "Azure Sphere Public API"