Quickstart: Deploy an Azure Linux Container Host for AKS cluster by using an ARM template
Get started with the Azure Linux Container Host by using an Azure Resource Manager (ARM) template to deploy an Azure Linux Container Host cluster. After installing the prerequisites, you'll create a SSH key pair, review the template, deploy the template and validate it, and then deploy an application.
An Azure Resource Manager template is a JavaScript Object Notation (JSON) file that defines the infrastructure and configuration for your project. The template uses declarative syntax. You describe your intended deployment without writing the sequence of programming commands to create the deployment.
Prerequisites
-
If you don't have an Azure subscription, create an Azure free account before you begin.
Use the Bash environment in Azure Cloud Shell. For more information, see Azure Cloud Shell Quickstart - Bash.

If you prefer to run CLI reference commands locally, install the Azure CLI. If you're running on Windows or macOS, consider running Azure CLI in a Docker container. For more information, see How to run the Azure CLI in a Docker container.
If you're using a local installation, sign in to the Azure CLI by using the az login command. To finish the authentication process, follow the steps displayed in your terminal. For other sign-in options, see Sign in with the Azure CLI.
When you're prompted, install the Azure CLI extension on first use. For more information about extensions, see Use extensions with the Azure CLI.
Run az version to find the version and dependent libraries that are installed. To upgrade to the latest version, run az upgrade.
If you don't already have kubectl installed, install it through Azure CLI using
az aks install-clior follow the upstream instructions.To create an AKS cluster using a Resource Manager template, you provide an SSH public key. If you need this resource, see the following section; otherwise skip to the Review the template section.
The identity you're using to create your cluster has the appropriate minimum permissions. For more information on access and identity for AKS, see Access and identity options for Azure Kubernetes Service (AKS).
To deploy a Bicep file or ARM template, you need write access on the resources you're deploying and access to all operations on the Microsoft.Resources/deployments resource type. For example, to deploy a virtual machine, you need Microsoft.Compute/virtualMachines/write and Microsoft.Resources/deployments/* permissions. For a list of roles and permissions, see Azure built-in roles.
Create an SSH key pair
To access AKS nodes, you connect using an SSH key pair (public and private), which you generate using the ssh-keygen command. By default, these files are created in the ~/.ssh directory. Running the ssh-keygen command overwrites any SSH key pair with the same name already existing in the given location.
Go to https://shell.azure.com to open Cloud Shell in your browser.
Run the
ssh-keygencommand. The following example creates an SSH key pair using RSA encryption and a bit length of 4096:ssh-keygen -t rsa -b 4096
For more information about creating SSH keys, see Create and manage SSH keys for authentication in Azure.
Review the template
The following deployment uses an ARM template from Azure Quickstart Templates.
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.1",
"parameters": {
"clusterName": {
"type": "string",
"defaultValue": "azurelinuxakscluster",
"metadata": {
"description": "The name of the Managed Cluster resource."
}
},
"location": {
"type": "string",
"defaultValue": "[resourceGroup().location]",
"metadata": {
"description": "The location of the Managed Cluster resource."
}
},
"dnsPrefix": {
"type": "string",
"metadata": {
"description": "Optional DNS prefix to use with hosted Kubernetes API server FQDN."
}
},
"osDiskSizeGB": {
"type": "int",
"defaultValue": 0,
"minValue": 0,
"maxValue": 1023,
"metadata": {
"description": "Disk size (in GB) to provision for each of the agent pool nodes. This value ranges from 0 to 1023. Specifying 0 will apply the default disk size for that agentVMSize."
}
},
"agentCount": {
"type": "int",
"defaultValue": 3,
"minValue": 1,
"maxValue": 50,
"metadata": {
"description": "The number of nodes for the cluster."
}
},
"agentVMSize": {
"type": "string",
"defaultValue": "Standard_DS2_v2",
"metadata": {
"description": "The size of the Virtual Machine."
}
},
"linuxAdminUsername": {
"type": "string",
"metadata": {
"description": "User name for the Linux Virtual Machines."
}
},
"sshRSAPublicKey": {
"type": "string",
"metadata": {
"description": "Configure all linux machines with the SSH RSA public key string. Your key should include three parts, for example 'ssh-rsa AAAAB...snip...UcyupgH azureuser@linuxvm'"
}
},
"osType": {
"type": "string",
"defaultValue": "Linux",
"allowedValues": [
"Linux"
],
"metadata": {
"description": "The type of operating system."
}
},
"osSKU": {
"type": "string",
"defaultValue": "AzureLinux",
"allowedValues": [
"AzureLinux",
"Ubuntu"
],
"metadata": {
"description": "The Linux SKU to use."
}
}
},
"resources": [
{
"type": "Microsoft.ContainerService/managedClusters",
"apiVersion": "2021-03-01",
"name": "[parameters('clusterName')]",
"location": "[parameters('location')]",
"properties": {
"dnsPrefix": "[parameters('dnsPrefix')]",
"agentPoolProfiles": [
{
"name": "agentpool",
"mode": "System",
"osDiskSizeGB": "[parameters('osDiskSizeGB')]",
"count": "[parameters('agentCount')]",
"vmSize": "[parameters('agentVMSize')]",
"osType": "[parameters('osType')]",
"osSKU": "[parameters('osSKU')]",
"storageProfile": "ManagedDisks"
}
],
"linuxProfile": {
"adminUsername": "[parameters('linuxAdminUsername')]",
"ssh": {
"publicKeys": [
{
"keyData": "[parameters('sshRSAPublicKey')]"
}
]
}
}
},
"identity": {
"type": "SystemAssigned"
}
}
],
"outputs": {
"controlPlaneFQDN": {
"type": "string",
"value": "[reference(parameters('clusterName')).fqdn]"
}
}
}
To add Azure Linux to an existing ARM template, you need to add "osSKU": "AzureLinux" and "mode": "System" to agentPoolProfiles and set the apiVersion to 2021-03-01 or newer ("apiVersion": "2021-03-01").
Deploy the template
Select the following button to sign in to Azure and open a template.
Select or enter the following values.
For this quickstart, leave the default values for the OS Disk Size GB, Agent Count, Agent VM Size, OS Type, and Kubernetes Version. Provide your own values for the following template parameters:
- Subscription: Select an Azure subscription.
- Resource group: Select Create new. Enter a unique name for the resource group, such as testAzureLinuxResourceGroup, then choose OK.
- Location: Select a location, such as East US.
- Cluster name: Enter a unique name for the AKS cluster, such as testAzureLinuxCluster.
- DNS prefix: Enter a unique DNS prefix for your cluster, such as myAzureLinuxCluster.
- Linux Admin Username: Enter a username to connect using SSH, such as azureUser.
- SSH RSA Public Key: Copy and paste the public part of your SSH key pair (by default, the contents of ~/.ssh/id_rsa.pub).
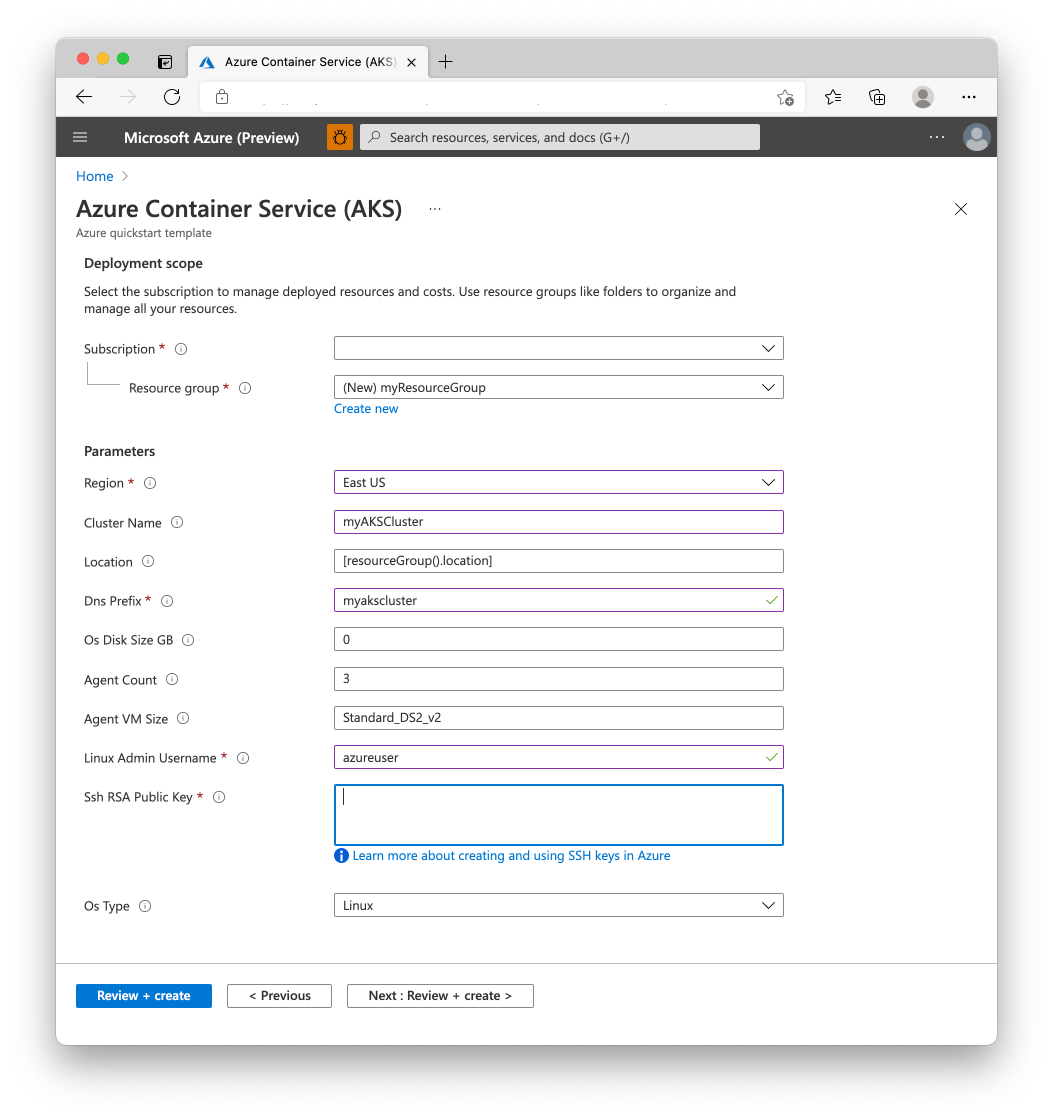
Select Review + Create.
It takes a few minutes to create the Azure Linux Container Host cluster. Wait for the cluster to be successfully deployed before you move on to the next step.
Validate the deployment
Connect to the cluster
To manage a Kubernetes cluster, use the Kubernetes command-line client, kubectl.
Install
kubectllocally using theaz aks install-clicommand:az aks install-cliConfigure
kubectlto connect to your Kubernetes cluster using theaz aks get-credentialscommand. This command downloads credentials and configures the Kubernetes CLI to use them.az aks get-credentials --resource-group testAzureLinuxResourceGroup --name testAzureLinuxClusterVerify the connection to your cluster using the
kubectl getcommand. This command returns a list of the cluster nodes.kubectl get nodesThe following output example shows the three nodes created in the previous steps. Make sure the node status is Ready:
NAME STATUS ROLES AGE VERSION aks-agentpool-41324942-0 Ready agent 6m44s v1.12.6 aks-agentpool-41324942-1 Ready agent 6m46s v1.12.6 aks-agentpool-41324942-2 Ready agent 6m45s v1.12.6
Deploy the application
A Kubernetes manifest file defines a cluster's desired state, such as which container images to run.
In this quickstart, you use a manifest to create all objects needed to run the Azure Vote application. This manifest includes two Kubernetes deployments:
- The sample Azure Vote Python applications.
- A Redis instance.
Two Kubernetes Services are also created:
- An internal service for the Redis instance.
- An external service to access the Azure Vote application from the internet.
Create a file named
azure-vote.yaml.- If you use the Azure Cloud Shell, this file can be created using
code,vi, ornanoas if working on a virtual or physical system
- If you use the Azure Cloud Shell, this file can be created using
Copy in the following YAML definition:
apiVersion: apps/v1 kind: Deployment metadata: name: azure-vote-back spec: replicas: 1 selector: matchLabels: app: azure-vote-back template: metadata: labels: app: azure-vote-back spec: nodeSelector: "kubernetes.io/os": linux containers: - name: azure-vote-back image: mcr.microsoft.com/oss/bitnami/redis:6.0.8 env: - name: ALLOW_EMPTY_PASSWORD value: "yes" resources: requests: cpu: 100m memory: 128Mi limits: cpu: 250m memory: 256Mi ports: - containerPort: 6379 name: redis --- apiVersion: v1 kind: Service metadata: name: azure-vote-back spec: ports: - port: 6379 selector: app: azure-vote-back --- apiVersion: apps/v1 kind: Deployment metadata: name: azure-vote-front spec: replicas: 1 selector: matchLabels: app: azure-vote-front template: metadata: labels: app: azure-vote-front spec: nodeSelector: "kubernetes.io/os": linux containers: - name: azure-vote-front image: mcr.microsoft.com/azuredocs/azure-vote-front:v1 resources: requests: cpu: 100m memory: 128Mi limits: cpu: 250m memory: 256Mi ports: - containerPort: 80 env: - name: REDIS value: "azure-vote-back" --- apiVersion: v1 kind: Service metadata: name: azure-vote-front spec: type: LoadBalancer ports: - port: 80 selector: app: azure-vote-frontFor a breakdown of YAML manifest files, see Deployments and YAML manifests.
Deploy the application using the kubectl apply command and specify the name of your YAML manifest:
kubectl apply -f azure-vote.yamlThe following example resembles output showing the successfully created deployments and services:
deployment "azure-vote-back" created service "azure-vote-back" created deployment "azure-vote-front" created service "azure-vote-front" created
Test the application
When the application runs, a Kubernetes service exposes the application front end to the internet. This process can take a few minutes to complete.
Monitor progress using the kubectl get service command with the --watch argument.
kubectl get service azure-vote-front --watch
The EXTERNAL-IP output for the azure-vote-front service will initially show as pending.
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
azure-vote-front LoadBalancer 10.0.37.27 <pending> 80:30572/TCP 6s
Once the EXTERNAL-IP address changes from pending to an actual public IP address, use CTRL-C to stop the kubectl watch process. The following example output shows a valid public IP address assigned to the service:
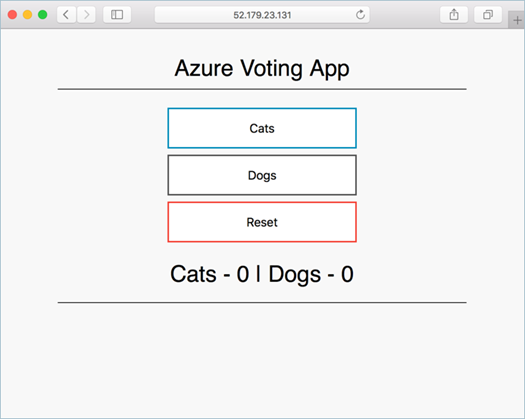
azure-vote-front LoadBalancer 10.0.37.27 52.179.23.131 80:30572/TCP 2m
To see the Azure Vote app in action, open a web browser to the external IP address of your service.
Delete the cluster
If you're not going to continue through the following tutorials, to avoid Azure charges clean up any unnecessary resources. Use the az group delete command to remove the resource group and all related resources.
az group delete --name testAzureLinuxCluster --yes --no-wait
Next steps
In this quickstart, you deployed an Azure Linux Container Host cluster. To learn more about the Azure Linux Container Host, and walk through a complete cluster deployment and management example, continue to the Azure Linux Container Host tutorial.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for
