AMSI demonstrations with Microsoft Defender for Endpoint
Applies to:
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender for Business
- Microsoft Defender for Endpoint Plan 1
- Microsoft Defender Antivirus
Microsoft Defender for Endpoint utilizes the Antimalware Scan Interface (AMSI) to enhance protection against fileless malware, dynamic script-based attacks, and other nontraditional cyber threats. In this article, we describe how to test the AMSI engine with a benign sample.
Scenario requirements and setup
- Windows 10 or newer
- Windows Server 2016, or newer
- Microsoft Defender Antivirus (as primary) and these capabilities need to be enabled:
- Real-Time Protection (RTP)
- Behavior Monitoring (BM)
- Turn on script scanning
Testing AMSI with Defender for Endpoint
In this demonstration article, you have two engine choices to test AMSI:
- PowerShell
- VBScript
Test AMSI with PowerShell
Save the following PowerShell script as
AMSI_PoSh_script.ps1:On your device, open PowerShell as an administrator.
Type
Powershell -ExecutionPolicy Bypass AMSI_PoSh_script.ps1, and then press Enter.The result should be as follows:
Testing AMSI with VBScript
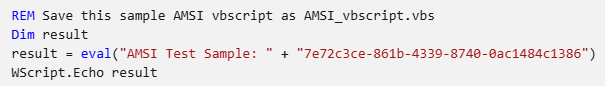
Save the following VBScript as
AMSI_vbscript.vbs:On your Windows Device, open Command Prompt as an administrator.
Type
wscript AMSI_vbscript.js, and then press Enter.The result should be as follows:
Verifying the test results
In your protection history, you should be able to see the following information:
Get the list of Microsoft Defender Antivirus threats
You can view detected threats by using the Event log or PowerShell.
Use the Event log
Go to Start, and search for
EventVwr.msc. Open Event Viewer in the list of results.Go to Applications and Services Logs > Microsoft > Windows > Windows Defender operational events.
Look for
event ID 1116. You should see the following information:
Use PowerShell
On your device, open PowerShell.
Type the following command:
Get-MpThreat.You might see the following results:
See also
Microsoft Defender for Endpoint - demonstration scenarios
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.