Use Microsoft Defender for Endpoint Security Settings Management to manage Microsoft Defender Antivirus
Applies to:
- Microsoft Defender XDR
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender for Endpoint Plan 1
Platforms
- Windows
- Windows Server
- macOS
- Linux
Use the Microsoft Defender for Endpoint Security Settings Management to manage Microsoft Defender Antivirus security policies on devices.
Pre-requisites:
Please review the pre-requisites here.
Note
The Endpoint Security Policies page in the Microsoft Defender portal is available only for users with the Security Administrator role assigned. Any other user role, such as Security Reader, cannot access the portal. When a user has the required permissions to view policies in the Microsoft Defender portal, the data is presented based on Intune permissions. If the user is in scope for Intune role-based access control, it applies to the list of policies presented in the Microsoft Defender portal. We recommend granting security administrators with the Intune built-in role, "Endpoint Security Manager" to effectively align the level of permissions between Intune and the Microsoft Defender portal.
As a security administrator, you can configure different Microsoft Defender Antivirus security policy settings in the Microsoft Defender portal.
Important
Microsoft recommends that you use roles with the fewest permissions. This helps improve security for your organization. Global Administrator is a highly privileged role that should be limited to emergency scenarios when you can't use an existing role.
You'll find endpoint security policies under Endpoints > Configuration management > Endpoint security policies.
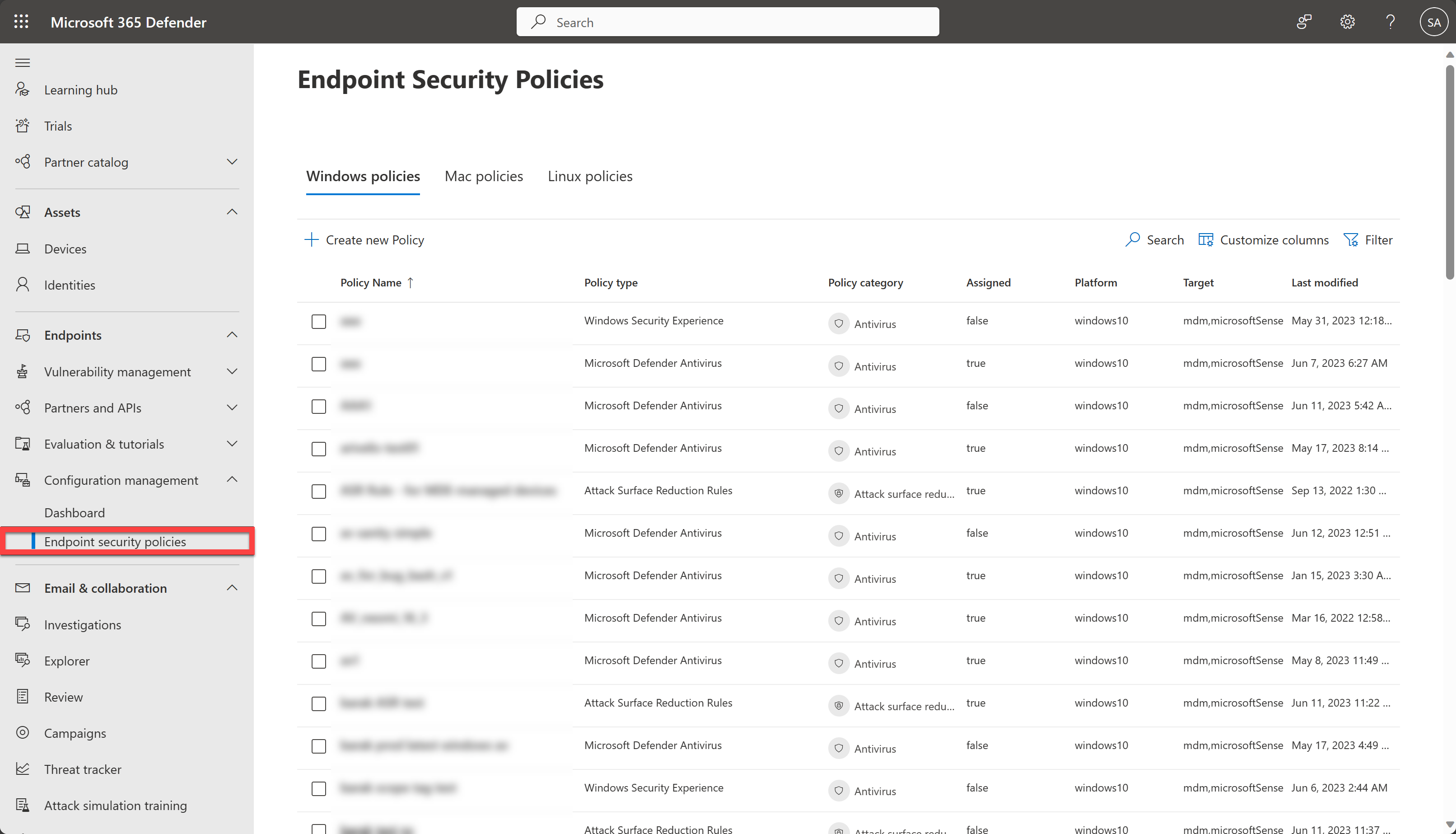
The following list provides a brief description of each endpoint security policy type:
Antivirus - Antivirus policies help security admins focus on managing the discrete group of antivirus settings for managed devices.
Disk encryption - Endpoint security disk encryption profiles focus on only the settings that are relevant for a devices built-in encryption method, like FileVault or BitLocker. This focus makes it easy for security admins to manage disk encryption settings without having to navigate a host of unrelated settings.
Firewall - Use the endpoint security Firewall policy in Intune to configure a devices built-in firewall for devices that run macOS and Windows 10/11.
Endpoint detection and response - When you integrate Microsoft Defender for Endpoint with Intune, use the endpoint security policies for endpoint detection and response (EDR) to manage the EDR settings and onboard devices to Microsoft Defender for Endpoint.
Attack surface reduction - When Microsoft Defender Antivirus is in use on your Windows 10/11 devices, use Intune endpoint security policies for attack surface reduction to manage those settings for your devices.
Create an endpoint security policy
Sign in to the Microsoft Defender portal using at least a Security Administrator role.
Select Endpoints > Configuration management > Endpoint security policies and then select Create new Policy.
Select a platform from the dropdown list.
Select a template, then select Create policy.
On the Basics page, enter a name and description for the profile, then choose Next.
On the Settings page, expand each group of settings, and configure the settings you want to manage with this profile.
When you're done configuring settings, select Next.
On the Assignments page, select the groups that will receive this profile.
Select Next.
On the Review + create page, when you're done, select Save. The new profile is displayed in the list when you select the policy type for the profile you created.
Note
To edit the scope tags, you'll need to go to the Microsoft Intune admin center.
To edit an endpoint security policy
Select the new policy, and then select Edit.
Select Settings to expand a list of the configuration settings in the policy. You can't modify the settings from this view, but you can review how they're configured.
To modify the policy, select Edit for each category where you want to make a change:
- Basics
- Settings
- Assignments
After you've made changes, select Save to save your edits. Edits to one category must be saved before you can introduce edits to additional categories.
Verify endpoint security policies
To verify that you have successfully created a policy, select a policy name from the list of endpoint security policies.
Note
It can take up to 90 minutes for a policy to reach a device. To expedite the process, for devices Managed by Defender for Endpoint, you can select Policy sync from the actions menu so that it is applied in approximately 10 minutes.
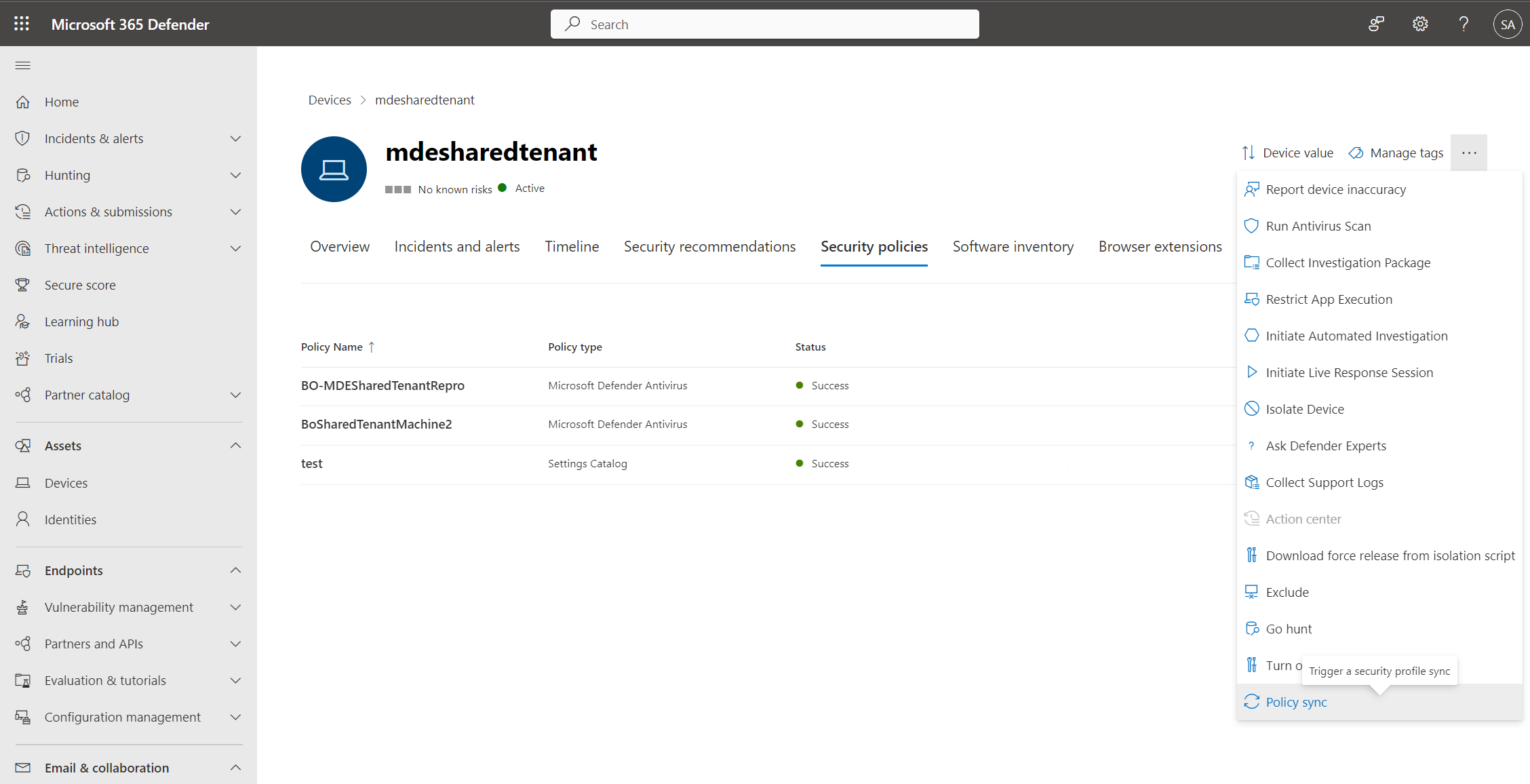
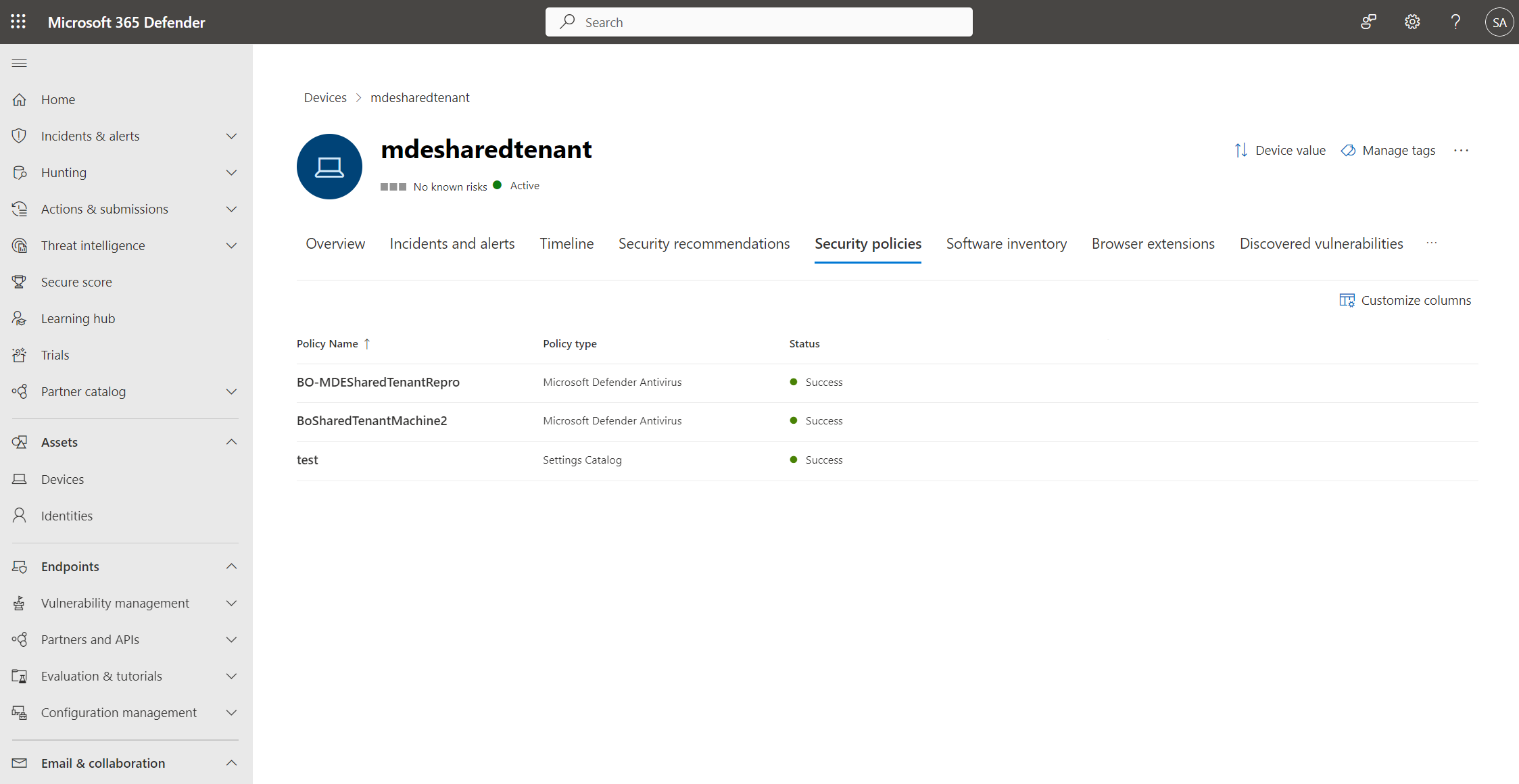
The policy page displays details that summarize the status of the policy. You can view a policy's status, which devices it has been applied to, and assigned groups.
During an investigation, you can also view the Security policies tab in the device page to view the list of policies that are being applied to a particular device. For more information, see Investigating devices.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for