Mitigate zero-day vulnerabilities
Applies to:
- Microsoft Defender Vulnerability Management
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender XDR
- Microsoft Defender for Servers Plan 1 & 2
A zero-day vulnerability is a flaw in software for which no official patch or security update has been released. A software vendor may or may not be aware of the vulnerability, and no public information about this risk is available. Zero-day vulnerabilities often have high severity levels and are actively exploited.
Vulnerability management will only display zero-day vulnerabilities it has information about.
Tip
Did you know you can try all the features in Microsoft Defender Vulnerability Management for free? Find out how to sign up for a free trial.
Find information about zero-day vulnerabilities
Once a zero-day vulnerability has been found, information about it will be conveyed through the following experiences in the Microsoft Defender portal.
Note
0-day vulnerability capability is currently available only for Windows products.
Defender Vulnerability Management dashboard
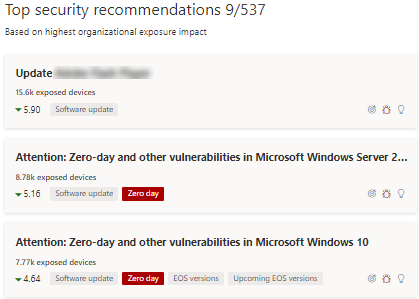
Look for recommendations with a zero-day tag in the "Top security recommendations" card.
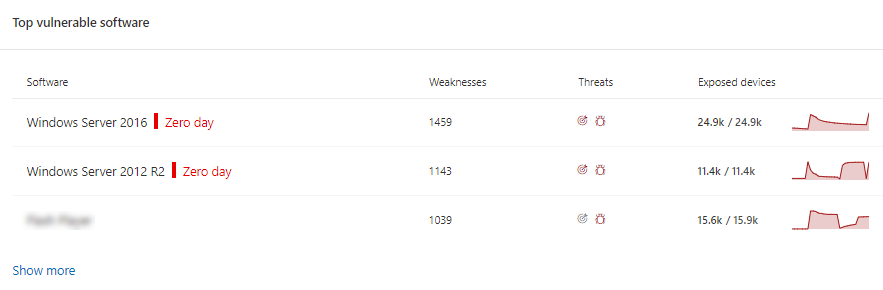
Find top software with the zero-day tag in the "Top vulnerable software" card.
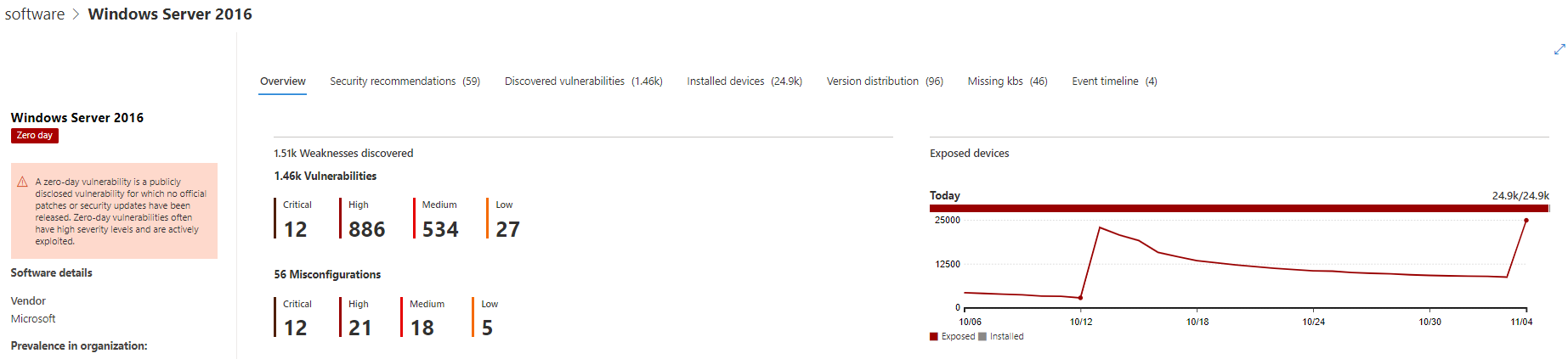
Weaknesses page
Look for the named zero-day vulnerability along with a description and details.
If this vulnerability has a CVE-ID assigned, you'll see the zero-day label next to the CVE name.
If this vulnerability has no CVE-ID assigned, you'll find it under an internal, temporary name that looks like "TVM-XXXX-XXXX". The name will be updated once an official CVE-ID has been assigned, but the previous internal name will still be searchable and found in the side-panel.
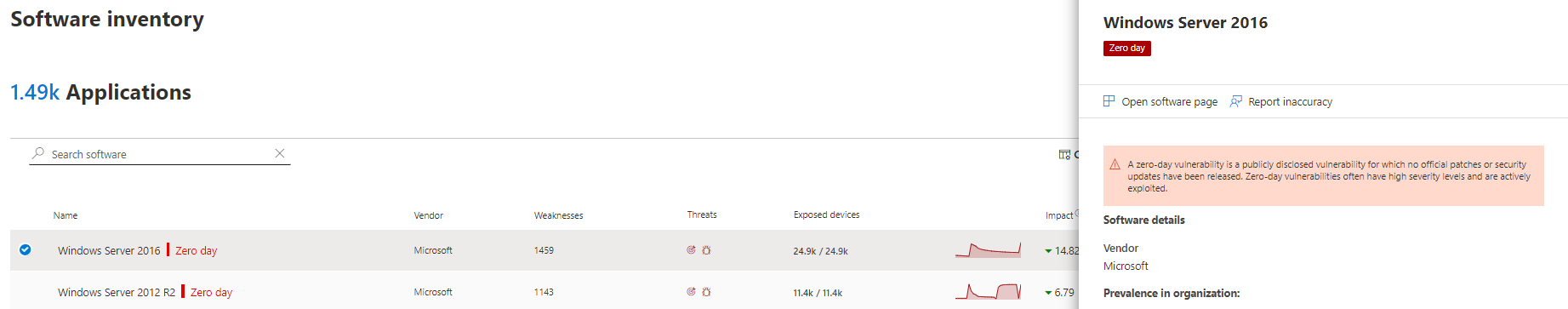
Software inventory page
Look for software with the zero-day tag. Filter by the "zero day" tag to only see software with zero-day vulnerabilities.
Software page
Look for a zero-day tag for each software that has been affected by the zero-day vulnerability.
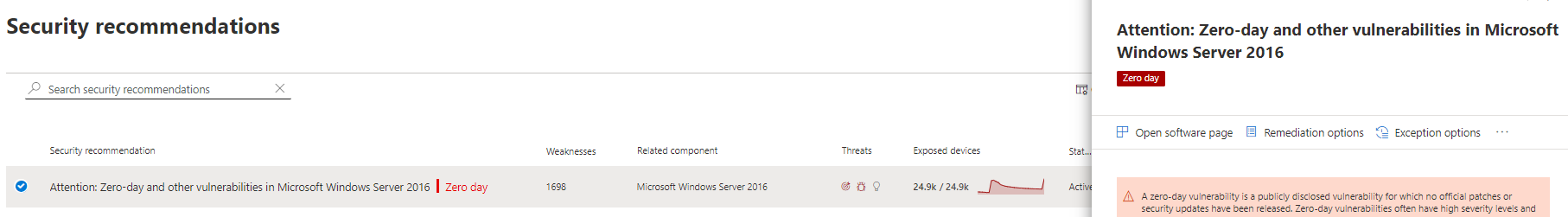
Security recommendations page
View clear suggestions about remediation and mitigation options, including workarounds if they exist. Filter by the "zero day" tag to only see security recommendations addressing zero-day vulnerabilities.
If there's software with a zero-day vulnerability and additional vulnerabilities to address, you'll get one recommendation about all vulnerabilities.
Addressing zero-day vulnerabilities
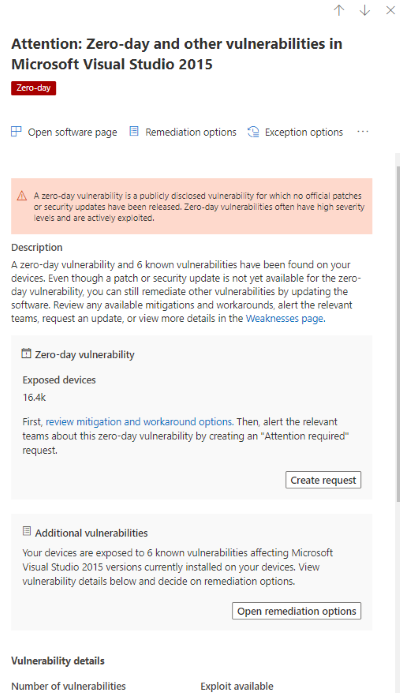
Go to the security recommendation page and select a recommendation with a zero-day. A flyout will open with information about the zero-day and other vulnerabilities for that software.
There will be a link to mitigation options and workarounds if they are available. Workarounds may help reduce the risk posed by this zero-day vulnerability until a patch or security update can be deployed.
Open remediation options and choose the attention type. An "attention required" remediation option is recommended for the zero-day vulnerabilities, since an update hasn't been released yet. You won't be able to select a due date, since there's no specific action to perform. If there are older vulnerabilities for this software you wish to remediation, you can override the "attention required" remediation option and choose "update."
Track zero-day remediation activities
Go to the Remediation page to view the remediation activity item. If you chose the "attention required" remediation option, there will be no progress bar, ticket status, or due date since there's no actual action we can monitor. You can filter by remediation type, such as "software update" or "attention required," to see all activity items in the same category.
Patching zero-day vulnerabilities
When a patch is released for the zero-day, the recommendation will be changed to "Update" and a blue label next to it that says "New security update for zero day." It will no longer consider as a zero-day, the zero-day tag will be removed from all pages.