Meet multifactor authentication requirements of memorandum 22-09
Learn about using Microsoft Entra ID as the centralized identity management system when implementing Zero Trust principles. See, US Office of Management and Budget (OMB) M 22-09 Memorandum for the Heads of Executive Departments and Agencies.
The memo requirements are that employees use enterprise-managed identities to access applications, and that multifactor authentication protects employees from sophisticated online attacks, such as phishing. This attack method attempts to obtain and compromise credentials, with links to inauthentic sites.
Multifactor authentication prevents unauthorized access to accounts and data. The memo requirements cite multifactor authentication with phishing-resistant methods: authentication processes designed to detect and prevent disclosure of authentication secrets and outputs to a website or application masquerading as a legitimate system. Therefore, establish what multifactor authentication methods qualify as phishing-resistant.
Phishing-resistant methods
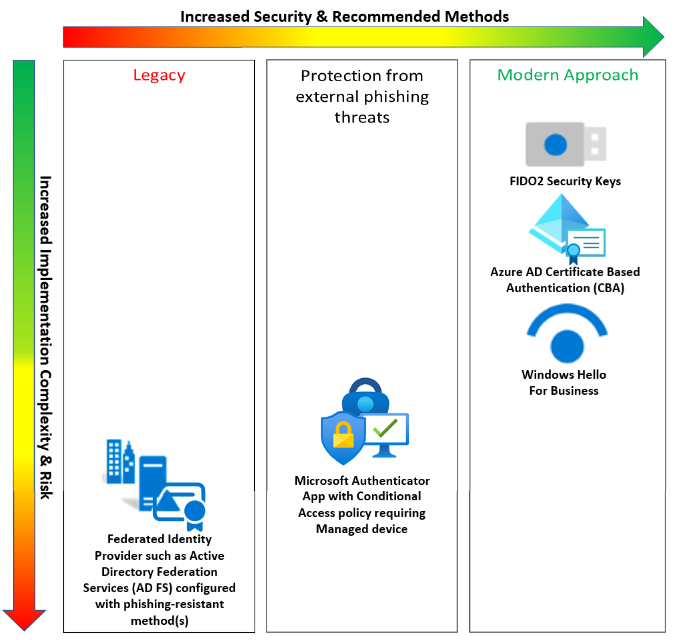
Some federal agencies have deployed modern credentials such as FIDO2 security keys or Windows Hello for Business. Many are evaluating Microsoft Entra authentication with certificates.
Learn more:
- FIDO2 security keys
- Windows Hello for Business
- Overview of Microsoft Entra certificate-based authentication
Some agencies are modernizing their authentication credentials. There are multiple options for meeting phishing-resistant multifactor authentication requirements with Microsoft Entra ID. Microsoft recommends adopting phishing-resistant multifactor authentication method that matches the agency capabilities. Consider what's possible now for phishing-resistance multifactor authentication to improve the overall cybersecurity posture. Implement modern credentials. However, if the quickest path isn't a modern approach, take the step to begin the journey toward modern approaches.
Modern approaches
- FIDO2 security keys are, according to the Cybersecurity & Infrastructure Security Agency (CISA) the gold standard of multifactor authentication
- See, Passwordless authentication options for Microsoft Entra ID, FIDO2 security keys
- Go to cisa.gov for More than a Password
- Microsoft Entra certificate authentication without dependency on a federated identity provider.
- This solution includes smart card implementations: Common Access Card (CAC), Personal Identity Verification (PIV), and derived PIV credentials for mobile devices or security keys
- See, Overview of Microsoft Entra certificate-based authentication
- Windows Hello for Business has phishing-resistant multifactor authentication
Protection from external phishing
Microsoft Authenticator and Conditional Access policies enforce managed devices: Microsoft Entra hybrid joined devices or devices marked as compliant. Install Microsoft Authenticator on devices accessing applications protected by Microsoft Entra ID.
Learn more: Authentication methods in Microsoft Entra ID - Microsoft Authenticator app
Important
To meet the phishing-resistant requirement: Manage only the devices accessing the protected application. Users allowed to use Microsoft Authenticator are in scope for Conditional Access policy requiring managed devices for access. A Conditional Access policy blocks access to the Microsoft Intune Enrollment Cloud App. Users allowed to use Microsoft Authenticator are in scope for this Conditional Access policy. Use the same group(s) to allow Microsoft Authenticator authentication in Conditional Access policies to ensure that users enabled for the authentication method are in scope for both policies. This Conditional Access policy prevents the most significant vector of phishing threats from malicious external actors. It also prevents malicious actor from phishing Microsoft Authenticator to register a credential, or join a device and enroll it in Intune to mark it as compliant.
Learn more:
- Plan your Microsoft Entra hybrid join implementation, or
- How to: Plan your Microsoft Entra join implementation
- See also, Common Conditional Access policy: Require a compliant device, Microsoft Entra hybrid joined device, or multifactor authentication for all users
Note
Microsoft Authenticator isn't phishing-resistant. Configure Conditional Access policy to require that managed devices get protection from external phishing threats.
Legacy
Federated identity providers (IdPs) such as Active Directory Federation Services (AD FS) configured with phishing-resistant method(s). While agencies achieve phishing resistance with federated IdP, it adds cost, complexity, and risk. Microsoft encourages the security benefits of Microsoft Entra ID an IdP, removing the associated risk of a federated IdP
Learn more:
- Protecting Microsoft 365 from on-premises attacks
- Deploying AD Federation Services in Azure
- Configuring AD FS for user certificate authentication
Phishing-resistant method considerations
Your current device capabilities, user personas, and other requirements might dictate multi-factor methods. For example, FIDO2 security keys with USB-C support require devices with USB-C ports. Consider the following information when evaluating phishing-resistant multifactor authentication:
- Device types and capabilities you can support: kiosks, laptops, mobile phones, biometric readers, USB, Bluetooth, and near-field communication devices
- Organizational user personas: front-line workers, remote workers with and without company-owned hardware, administrators with privileged access workstations, and business-to-business guest users
- Logistics: distribute, configure, and register multifactor authentication methods such as FIDO2 security keys, smart cards, government-furnished equipment, or Windows devices with TPM chips
- Federal Information Processing Standards (FIPS) 140 validation at an authenticator assurance level: some FIDO security keys are FIPS 140 validated at levels for AAL3 set by NIST SP 800-63B
Implementation considerations for phishing-resistant multifactor authentication
See the following sections for support of implementing phishing-resistant methods for application and virtual device sign-in.
Application sign-in scenarios from various clients
The following table details the availability of phishing-resistant multifactor authentication scenarios, based on the device type that's used to sign in to the applications:
| Device | AD FS as a federated IdP with certificate authentication | Microsoft Entra certificate authentication | FIDO2 security keys | Windows Hello for Business | Microsoft Authenticator with Conditional Access policies enforcing Microsoft Entra hybrid join or compliant devices |
|---|---|---|---|---|---|
| Windows device |  |
 |
 |
 |
 |
| iOS mobile device |  |
 |
Not applicable | Not applicable |  |
| Android mobile device |  |
 |
Not applicable | Not applicable |  |
| macOS device |  |
 |
Edge/Chrome | Not applicable |  |
Learn more: Browser support for FIDO2 passwordless authentication
Virtual device sign-in scenarios that require integration
To enforce phishing-resistant multifactor authentication, integration might be necessary. Enforce multifactor authentication for users accessing applications and devices. For the five phishing-resistant multifactor authentication types, use the same features to access the following device types:
| Target system | Integration actions |
|---|---|
| Azure Linux virtual machine (VM) | Enable the Linux VM for Microsoft Entra sign-in |
| Azure Windows VM | Enable the Windows VM for Microsoft Entra sign-in |
| Azure Virtual Desktop | Enable Azure Virtual Desktop for Microsoft Entra sign-in |
| VMs hosted on-premises or in other clouds | Enable Azure Arc on the VM and then enable Microsoft Entra sign-in. Currently in private preview for Linux. Support for Windows VMs hosted in these environments is on our roadmap. |
| Non-Microsoft virtual desktop solution | Integrate the virtual desktop solution as an app in Microsoft Entra ID |
Enforcing phishing-resistant multifactor authentication
Use Conditional Access to enforce multifactor authentication for users in your tenant. With the addition of cross-tenant access policies, you can enforce it on external users.
Learn more: Overview: Cross-tenant access with Microsoft Entra External ID
Enforcement across agencies
Use Microsoft Entra B2B collaboration to meet requirements that facilitate integration:
- Limit what other Microsoft tenants your users access
- Allow access to users you don't have to manage in your tenant, but enforce multifactor authentication and other access requirements
Learn more: B2B collaboration overview
Enforce multifactor authentication for partners and external users who access organizational resources. This action is common in inter-agency collaboration scenarios. Use Microsoft Entra cross-tenant access policies to configure multifactor authentication for external users who access applications and resources.
Configure trust settings in cross-tenant access policies to trust the multifactor authentication method the guest user tenant uses. Avoid having users register a multifactor authentication method with your tenant. Enable these policies on a per-organization basis. You can determine the multifactor authentication methods in the user home tenant and decide if they meet phishing resistance requirements.
Password policies
The memo requires organizations to change ineffective password policies, such as complex, rotated passwords. Enforcement includes removing the requirement for special characters and numbers, with time-based password rotation policies. Instead, consider the following options:
- Password protection to enforce a common list of weak passwords that Microsoft maintains
- In addition, include custom banned passwords
- See, Eliminate bad passwords using Microsoft Entra Password Protection
- Self-service password reset to enable users to reset passwords, for instance after account recovery
- Microsoft Entra ID Protection for alerts about compromised credentials
- What is risk?
Although the memo isn't specific about policies to use with passwords, consider the standard from NIST 800-63B.
See, NIST Special Publication 800-63B, Digital Identity Guidelines.