Customer Lockbox for Microsoft Fabric
Use Customer Lockbox for Microsoft Azure to control how Microsoft engineers access your data. In this article you'll learn how Customer Lockbox requests are initiated, tracked, and stored for later reviews and audits.
Typically, Customer Lockbox is used to help Microsoft engineers troubleshoot a Microsoft Fabric service support request. Customer Lockbox can also be used when Microsoft identifies a problem, and a Microsoft-initiated event is opened to investigate the issue.
Enable Customer Lockbox for Microsoft Fabric
To enable Customer Lockbox for Microsoft Fabric, you must be a Microsoft Entra Global Administrator. To assign roles in Microsoft Entra ID, see Assign Microsoft Entra roles to users.
Open the Azure portal.
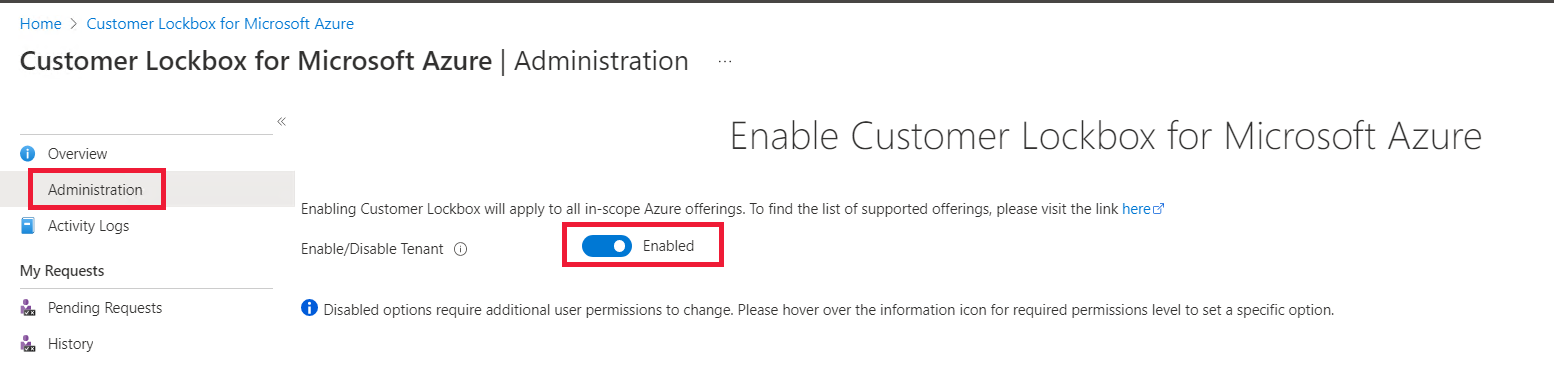
Go to Customer Lockbox for Microsoft Azure.
In the Administration tab, select Enabled.
Microsoft access request
In cases where the Microsoft engineer can't troubleshoot your issue by using standard tools, elevated permissions are requested using the Just-In-Time (JIT) access service. The request can come from the original support engineer, or from a different engineer.
After the access request is submitted, the JIT service evaluates the request, considering factors such as:
The scope of the resource
Whether the requester is an isolated identity or using multifactor authentication
Permissions levels
Based on the JIT role, the request may also include an approval from internal Microsoft approvers. For example, the approver might be the customer support lead or the DevOps Manager.
When the request requires direct access to customer data, a Customer Lockbox request is initiated. For example, in cases where remote desktop access to a customer's virtual machine is needed. Once the Customer Lockbox request is made, it awaits customer's approval before access is granted.
These steps describe a Microsoft initiated Customer Lockbox request, for Microsoft Fabric service.
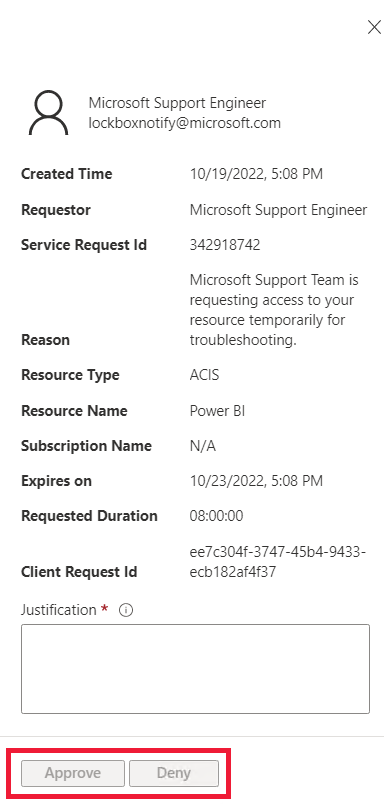
The Microsoft Entra Global Administrator receives a pending access request notification email from Microsoft. The admin who received the email, becomes the designated approver.
The email provides a link to Customer Lockbox in the Azure Administration module. Using the link, the designated approver signs in to the Azure portal to view any pending Customer Lockbox requests. The request remains in the customer queue for four days. After that, the access request automatically expires and no access is granted to Microsoft engineers.
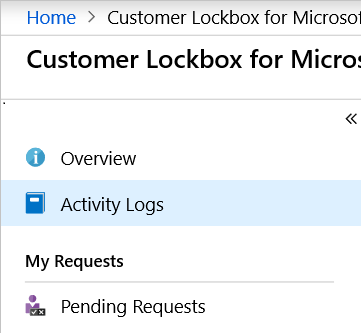
To get the details of the pending request, the designated approver can select the Customer Lockbox request from the Pending Requests menu option.
After reviewing the request, the designated approver enters a justification and selects one of the options below. For auditing purposes, the actions are logged in the Customer Lockbox logs.
Approve - Access is granted to the Microsoft engineer for a default period of eight hours.
Deny - The access request by the Microsoft engineer is rejected and no further action is taken.
Logs
Customer Lockbox has two type of logs:
Activity logs - Available from the Azure Monitor activity log.
The following activity logs are available for Customer Lockbox:
- Deny Lockbox Request
- Create Lockbox Request
- Approve Lockbox Request
- Lockbox Request Expiry
To access the activity logs, in the Azure portal, select Activity Log. You can filter the results for specific actions.
Audit logs - Available from the Microsoft Purview compliance portal. You can see the audit logs in the admin portal.
Customer Lockbox for Microsoft Fabric has four audit logs:
Audit log Friendly name GetRefreshHistoryViaLockbox Get refresh history via lockbox DeleteAdminUsageDashboardsViaLockbox Delete admin usage dashboards via lockbox DeleteUsageMetricsv2PackageViaLockbox Delete usage metrics v2 package via lockbox DeleteAdminMonitoringFolderViaLockbox Delete admin monitoring folder via lockbox GetQueryTextTelemetryViaLockbox Get query text from secured telemetry store via Lockbox
Exclusions
Customer Lockbox requests aren't triggered in the following engineering support scenarios:
Emergency scenarios that fall outside of standard operating procedures. For example, a major service outage requires immediate attention to recover or restore services in an unexpected scenario. These events are rare and usually don't require access to customer data.
A Microsoft engineer accesses the Azure platform as part of troubleshooting, and is accidentally exposed to customer data. For example, during troubleshooting the Azure Network Team captures a packet on a network device. Such scenarios don't usually result in access to meaningful customer data.
External legal demands for data. For details, see government requests for data on the Microsoft Trust Center.
Data access
Access to data varies according to the Microsoft Fabric experience your request is for. This section lists which data the Microsoft engineer can access, after you approve a Customer Lockbox request.
Power BI - When running the operations listed below, the Microsoft engineer will have access to a few tables linked to your request. Each operation the Microsoft engineer uses, is reflected in the audit logs.
- Get model refresh history
- Delete admin usage dashboard
- Delete usage metrics v2 package
- Delete admin monitoring folder
- Delete admin workspace
- Access particular Dataset in storage
- Get query text from secured telemetry store
Real-Time Intelligence - The Real-Time Intelligence engineer will have access to the data in the KQL database that's linked to your request.
Data Engineering - The Data Engineering engineer will have access to the following Spark logs linked to your request:
- Driver logs
- Event logs
- Executor logs
Data Factory - The Data Factory engineer will have access to data pipeline definitions linked to your request, if permission is granted.