Migrate from Microsoft 365 Basic Mobility and Security to Intune
Microsoft 365 includes a basic set of policies that protect devices and protect Microsoft 365 apps, like Outlook. These policies are managed in the Microsoft Defender portal and are called Basic Mobility and Security. For more information on what Basic Mobility and Security offers, go to Capabilities of Basic Mobility and Security.
Many organizations want more or next-level device management features. Specifically, they want the features that are included with Microsoft Intune. For a comparison of the features, go to Choose between Basic Mobility and Security or Intune.
You can migrate from Basic Mobility and Security to Microsoft Intune. Migrating to Intune requires the following major steps:
Prepare:
Review your Intune licenses, Basic Mobility and Security policies, group memberships, and devices to streamline the migration.
Evaluate and migrate your existing policies:
Use the Migration evaluation in the Microsoft Intune admin center. The output shows Intune policy and group recommendations that replace the Basic Mobility and Security policies.
Assign the policies and complete the migration:
Assign licenses to users or groups, which will automatically switch the users to Intune device management at the next refresh cycle.
This article helps you migrate your mobile device management (MDM) from Microsoft 365 Basic Mobility and Security to Microsoft Intune.
Before you begin
When you sign in to the Intune admin center, use an account that has Microsoft Entra License administrator rights. For more information on this role, go to Microsoft Entra built-in roles - License Administrator.
Test the steps in this article on a test users group that have devices enrolled in Basic Mobility and Security. Confirm that the policies behave as you expect.
After you migrate to Intune, the existing device security policies deployed with Basic Mobility and Security are permanently frozen.
Assigning Intune licenses impacts the migration process. The license assignment controls the migration of devices from Basic Mobility and Security to Intune.
Users with Intune licenses already assigned can start receiving policies immediately, possibly sooner than you expect. The policies can happen even if Basic Mobility and Security didn't previously manage the users or devices.
If you want to prevent this behavior, you can unassign the Intune licenses before the migration. You can also create separate groups to help manage when the policies are deployed:
- Group 1: Users with Intune licenses already assigned
- Group 2: Users without Intune licenses assigned
Then, you can assign the migrated Basic Mobility and Security device security policies to users who aren't assigned Intune licenses.
Step 1 - Prepare
Before you migrate from Basic Mobility and Security device management to Intune device management:
Be sure you have enough Intune licenses to cover all your users managed by Basic Mobility and Security.
Review the device security policies in the Microsoft Defender portal. Delete any policies that are no longer needed. Deleting unneeded policies reduces the number of recommendations created by the Intune migration evaluation. The idea is to have fewer recommendations to review after the migration evaluation.
Review the membership of groups that are currently assigned device security policies.
If these groups include users that are already licensed for Intune, then they can get policies assigned sooner than expected. For more information on the impact of existing Intune licenses, go to Before you begin (in this article).
Review the types of devices currently enrolled in Basic Mobility and Security. Unsupported OS versions and variants may continue to work, but they aren't supported if migrated to Intune.
Settings applied to unsupported operating systems aren't moved to Intune. And if the user is already licensed for Intune, then their devices lose any configuration set by device security policies in the Microsoft Defender portal.
Before migration:
- Don't assign Intune licenses to users whose devices are managed by Basic Mobility and Security.
- Don't assign Intune licenses to enable app protection policies, also known as mobile application management (MAM).
Only assign Intune licenses to users after the policy migration is complete. For more information on the impact of Intune licenses, go to Before you begin (in this article).
You may have to create new Intune policies to replace Basic Mobility and Security policies. For more information on a minimum base set of policies, go to Get started with Intune.
After the migration evaluation process activates, you can't make changes to your device security policies in the Microsoft Defender portal. The existing Basic Mobility and Security policies are still enforced, but changes to these existing policies aren't saved.
Important
If you have any of the following products or service, then contact the support team before you proceed:
- Enterprise Mobility + Security A3 for Faculty
- Enterprise Mobility + Security A3 for Students
- Enterprise Mobility + Security A3 for students use benefit
- Enterprise Mobility + Security A5 for Faculty
- Enterprise Mobility + Security A5 for Students
- Enterprise Mobility + Security A5 for students use benefit
- Intune for Education
- Intune for Education Add-On
- Microsoft Intune for Education for Faculty
- Microsoft Intune for Education for Student
- Microsoft Intune for Education Prepaid Device
Step 2 - Evaluate and migrate your existing policies
After you've prepared your licenses and reviewed the information in Step 1 - Prepare, use the Microsoft Intune admin center Migration evaluation to get Intune policy recommendations.
The tool can migrate your existing Basic Mobility and Security device security policies to Intune as compliance policies and device configuration profiles. It also makes recommendations for which groups the new policies should be assigned.
These Intune recommendations are designed to replicate the Basic Mobility and Security policies. You need to review these recommendations to make sure they reflect the old policies.
To evaluate and migrate policies from Basic Mobility and Security to Intune:
Complete the steps in the Step 1 - Prepare section (in this article).
Open the Migration evaluation > select Start. It takes a few minutes to complete the evaluation.
Note
- If you navigate away from the Migration evaluation, the only way to return is to open the Migration evaluation link again.
- After you start the migration evaluation, you can't create new or edit existing device security policies in the Microsoft Defender portal.
Select Recommendations.
This page displays the Intune policy recommendations based on your Basic Mobility and Security policies. The recommendations are read only and can't be changed.
The name of each recommendation has a prefix based on the Basic Mobility and Security policy name. You need to review each item in the list, like the following example:
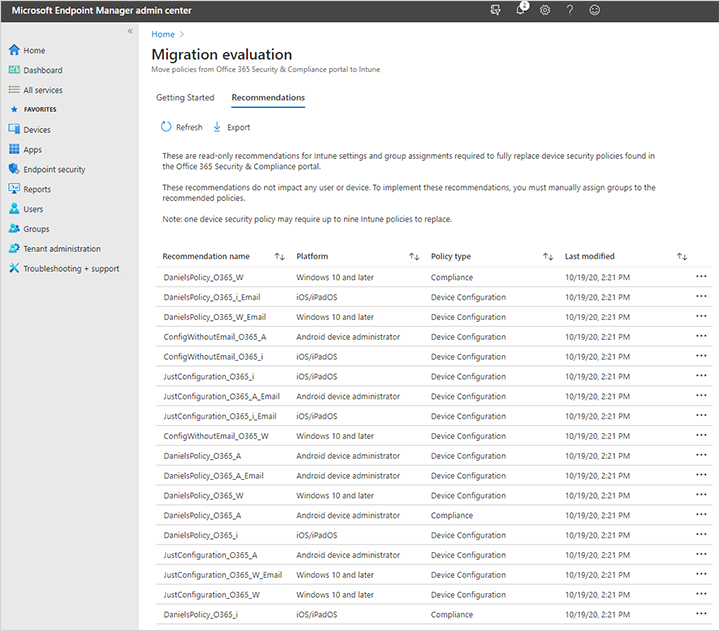
- Not all device settings correspond exactly to Intune settings and values. So, they can't be moved with precise one-to-one mapping. You need to review and possibly adjust these settings.
- The conditional access (CA) settings that control the Office 365 services are the same CA policies in Microsoft Entra ID. So, you don't need to review or make changes to them unless you want to.
Select an item in the list. The Compliance policy recommendation overview page opens. Review the instructions.
Select Details to review the recommended settings and group assignments:
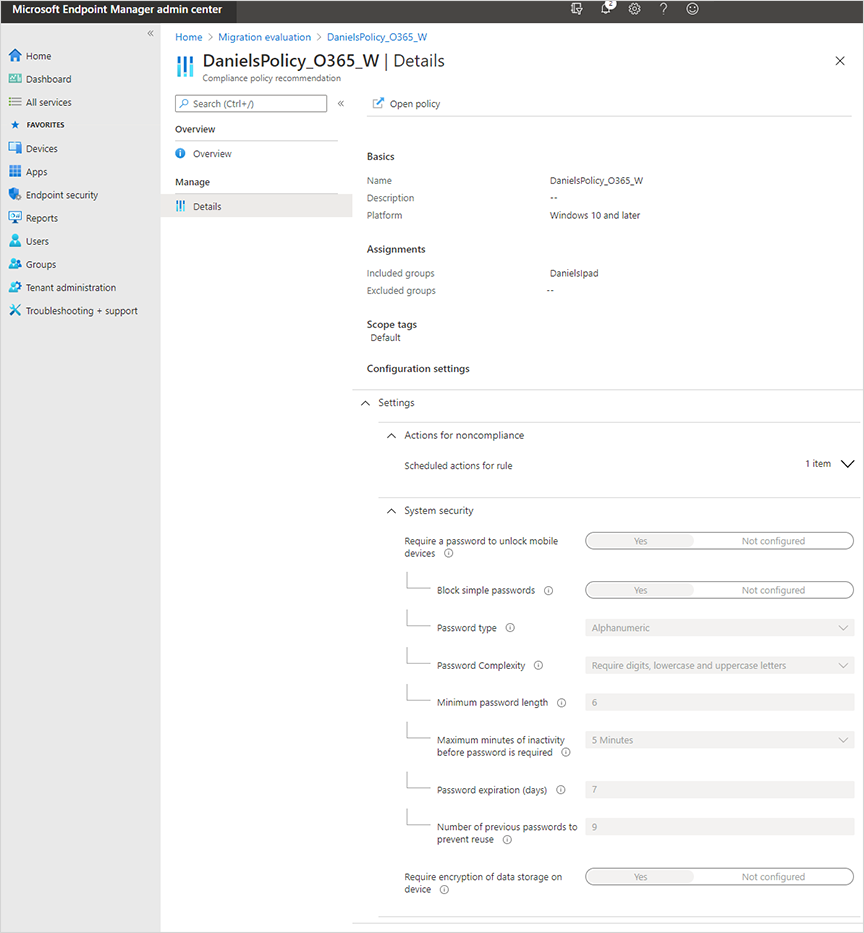
The policy recommendations on this page are a read-only report documenting the suggested settings and assignments to use. They aren't Intune policies yet.
While reviewing the recommendations, keep the following points in mind:
If the groups listed in the recommendation already have Intune policies assigned to them, then these policies may conflict with the recommended settings. To learn how conflicts are handled in Intune, go to Common questions and answers with device policies and profiles in Microsoft Intune.
Note
If you make any changes to migrated email profiles or fail to assign them to recommended groups, then users may be asked to re-enter their username and password to access email on their devices when the device migrates to Intune. For more information, go to policy mapping for Configuration.
If there are already Intune-licensed users in the recommended groups, then verify that the recommended policies are appropriate for these users. After you assign the policies to these groups, all Intune licensed users in the groups receive the policies, even users not previously managed by Basic Mobility and Security.
Note
For the Windows operating system, only Windows 10/11 desktop devices will have policy migrated for them. Other versions of Windows won't have policy migrated. For more information, see the Policy mapping for Access Requirements and Policy mapping for Configuration.
If you want to implement the recommended policy, then select Open policy. The policy page opens and the Intune policy is created. You can change or update the migrated policies.
Note
If you delete the policy, the Open policy link from the recommendation page won't work.
At this point, the policy is created, but it's not doing anything yet. The next step is to assign the policy to the recommended groups or other groups you choose.
Step 3 - Assign the policies and complete the migration
After the policies are created, they're ready to be assigned. For this migration to complete, all three have to be complete: assign groups, enable coexistence, and assign Intune licenses.
Assign the recommended groups to the policy. Select Open policy > Properties > Edit (next to Assignments) > use the assignments workflow to assign the groups.
When you assign groups, your newly migrated Intune policies replace the device settings configured in Basic Mobility and Security. If you don't assign the groups, then devices managed by Basic Mobility and Security could lose settings and email configuration when their users are licensed for Intune. Remember, the Intune license assignment is a key step in the migration of devices from Basic Mobility and Security to Intune device management.
For more information on the impact of existing Intune licenses, go to Before you begin (in this article).
Sign in to the Microsoft Intune admin center with Microsoft Entra License administrator rights.
Enable coexistence. When enabled:
- Users with existing Intune licenses are immediately moved to Intune and the newly migrated policies are applied at the next Intune refresh cycle.
- For users without Intune licenses, coexistence is the second step in the migration process. They'll be moved to Intune in the next step.
For users without Intune licenses, assign Intune licenses to the users you want to migrate. Your options:
- Assign licenses to Users. For more information, go to Assign licenses to users.
- Assign licenses to Groups. For more information, go to Assign licenses to a group.
For more information on assigning licenses in Intune, go to Assign licenses to users so they can enroll devices in Intune.
At this point, the key steps are complete:
- The policies are assigned to your groups.
- Coexistence is enabled in Intune.
- Intune licenses are assigned.
At the next Intune device refresh cycle, the devices automatically switch to Intune management and the new policies start affecting user devices.
What did I just do?
This section describes what happens behind the scenes when you migrate from Basic Mobility and Security to Intune.
The policies are mapped to Intune policies. For a mapping reference of the policies migrated by the Migration evaluation, go to:
When you complete the migration, your migrated policies are in Microsoft Intune admin center. The new policies include compliance policies, device configuration profiles, and conditional access policies. The new policies are in the following locations:
Intune policy type Intune location Compliance policies
Specify the device settings as access requirements.Microsoft Intune Microsoft Intune admin center > Devices > Compliance Configuration profiles
Specify other settings that aren't part of the access requirements, including email profiles.Microsoft Intune admin center > Devices > Manage devices > Configuration Conditional access policies
Microsoft Entra Conditional Access blocks access if the settings aren't compliant.Microsoft Intune admin center > Devices > Conditional access > Classic policies
Known issues
Start button always appears
Each time you open the Microsoft Intune admin center Migration evaluation, the Start button shows, even if the evaluation is already generated. If you dismiss the Start prompt, then the previously generated recommendations won't load.
Workaround: Start the evaluation again. It won't create more or duplicate recommendations or policies. Rerunning the migration detects that the evaluation has already succeeded and loads the previous recommendations.
Number of sign-in failures before device is wiped setting isn't migrated
The Number of sign-in failures before device is wiped setting isn't migrated to Intune.
Workaround: If this setting was enabled in the Basic Mobility and Security policy, then this setting must be manually added to Intune device configuration profiles. For more information on the similar settings you can configure in Intune, go to:
- Android Enterprise corporate-owned devices: Settings list to allow or restrict features
- Android Enterprise personally owned devices: Settings list to allow or restrict features
- iOS/iPadOS devices: Settings list to allow or restrict features
- Windows 10/11 device: Settings list to allow or restrict features