Authenticate to the direct management Azure API Management REST API
This guide describes how to create the access token (SAS token) required to make calls into the direct management Azure API Management REST API.
For more information about authorization and other prerequisites for accessing the direct management REST API, see Direct management API Management REST API.
Important
The direct management API Management REST API is deprecated and will be retired in March 2025.
Important
SAS token access can be applied only for direct management API calls, for example: https://apim-instance.management.azure-api.net/ /subscriptions/{subscriptionId}/resourceGroups/{resourceGroupName}/providers/Microsoft.ApiManagement/service/{serviceName}/apis?api-version=2021-08-01. You cannot use it for API calls to Azure Resource Manager.
Manually create a SAS token
Navigate to your Azure API Management instance in the Azure portal.
Select Management API from the Deployment + infrastructure section of the menu on the left.
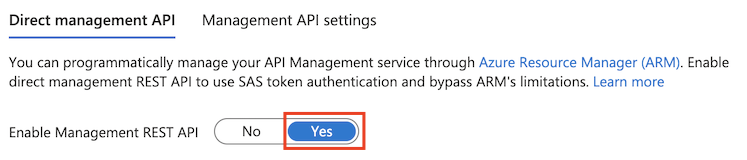
In Enable API Management REST API, select Yes.
Important
If Enable API Management REST API is not selected, calls made to the REST API for that service instance will fail.
Specify the expiration date and time for the access token in the Expiry text box. This value must be in the format
MM/DD/YYYY H:MM PM|AM.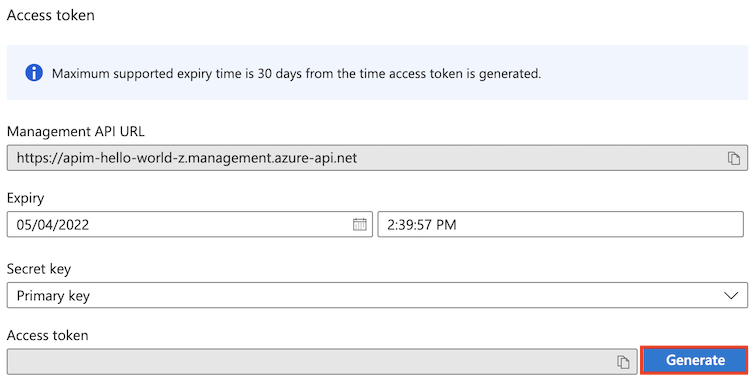
Select either the primary key or secondary key in the Secret key drop-down list. The keys provide equivalent access; two keys are provided to enable flexible key management strategies.
Select Generate to create the access token.
Copy the full access token and provide it in the
Authorizationheader of every request to the API Management REST API, as shown in the following example.Authorization: SharedAccessSignature integration&201808020500&aAsTE43MAbKMkZ6q83Z732IbzesfsaPEU404oUjQ4ZLE9iIXLz+Jj9rEctxKYw43SioCfdLaDq7dT8RQuBKc0w==
Programmatically create a SAS token
Construct a string-to-sign in the following format:
{identifier} + "\n" + {expiry}where:
identifier- the value of Identifier field from the Management API tab of your Azure API Management instance (see previous section for details).
expiry- desired expiry date of the SAS token.Generate a signature by applying an HMAC-SHA512 hash function to the string-to-sign using either the primary or secondary key.
Base64 encode the returned signature key.
Create an access token using the following format.
uid={identifier}&ex={expiry}&sn={Base64 encoded signature}Example:
uid=53dd860e1b72ff0467030003&ex=2014-08-04T22:03:00.0000000Z&sn=ItH6scUyCazNKHULKA0Yv6T+Skk4bdVmLqcPPPdWoxl2n1+rVbhKlplFrqjkoUFRr0og4wjeDz4yfThC82OjfQ==Use these values to create an
Authorizationheader in every request to the API Management REST API, as shown in the following example.Authorization: SharedAccessSignature uid=53dd860e1b72ff0467030003&ex=2014-08-04T22:03:00.0000000Z&sn=ItH6scUyCazNKHULKA0Yv6T+Skk4bdVmLqcPPPdWoxl2n1+rVbhKlplFrqjkoUFRr0og4wjeDz4yfThC82OjfQ==
The following example demonstrates the preceding steps for generating the access token.
using System;
using System.Text;
using System.Globalization;
using System.Security.Cryptography;
public class Program
{
public static void Main()
{
var id = "53d7e14aee681a0034030003";
var key = "pXeTVcmdbU9XxH6fPcPlq8Y9D9G3Cdo5Eh2nMSgKj/DWqeSFFXDdmpz5Trv+L2hQNM+nGa704Rf8Z22W9O1jdQ==";
var expiry = DateTime.UtcNow.AddDays(10);
using (var encoder = new HMACSHA512(Encoding.UTF8.GetBytes(key)))
{
var dataToSign = id + "\n" + expiry.ToString("O", CultureInfo.InvariantCulture);
var hash = encoder.ComputeHash(Encoding.UTF8.GetBytes(dataToSign));
var signature = Convert.ToBase64String(hash);
var encodedToken = string.Format("SharedAccessSignature uid={0}&ex={1:o}&sn={2}", id, expiry, signature);
Console.WriteLine(encodedToken);
}
}
}
Note
Both SAS token formats are correct and accepted:
SharedAccessSignature uid=53dd860e1b72ff0467030003&ex=2014-08-04T22:03:00.0000000Z&sn=ItH6scUyCazNKHULKA0Yv6T+Skk4bdVmLqcPPPdWoxl2n1+rVbhKlplFrqjkoUFRr0og4wjeDz4yfThC82OjfQ==
and
SharedAccessSignature integration&201808020500&aAsTE43MAbKMkZ6q83Z732IbzesfsaPEU404oUjQ4ZLE9iIXLz+Jj9rEctxKYw43SioCfdLaDq7dT8RQuBKc0w==
For complete sample code, see the API Management .NET REST API Sample.
Next steps
- See the API Management REST API reference.