Start using Microsoft Security Exposure Management
This article describes how to start working with the Microsoft Security Exposure Management dashboard.
Security Exposure Management is currently in public preview. Initially, your data uses default settings in Security Exposure Management.
Important
Some information in this article relates to a prereleased product which may be substantially modified before it's commercially released. Microsoft makes no warranties, expressed or implied, with respect to the information provided here.
Reviewing security exposure state
On the Exposure Management > Overview dashboard, you can review the overall state of your organizational security exposure.
Use the dashboard as a starting point for a snapshot of organizational posture and exposure, and drill down to details as needed.
Review assets
Get a quick view of your organization's exposed assets.
You can see onboarded devices, discovered devices not yet onboarded, internet facing devices, and cloud resources.
Knowing what is exposed helps you to address asset exposure risks.
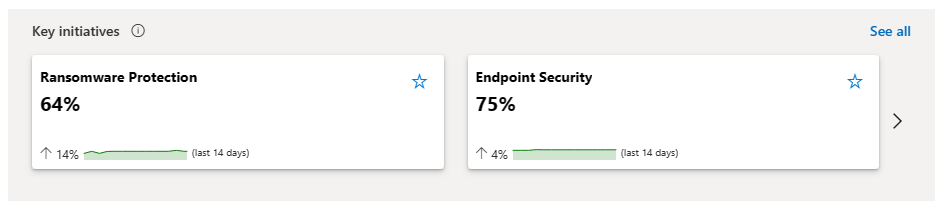
Review key initiatives
Key initiatives show initiatives that are marked as favorites in the initiatives page, and any newly added recommended initiatives.
Select an individual key initiative to drill down. You can also navigate to all initiatives.
Review top metrics
Top metrics identifies the security metrics with the most significant exposure.
You can see the current exposure value, a 14 day change trend, and associated recommendations.
Drilling down into an individual security metric takes you to its metric page. You can also access all metrics.
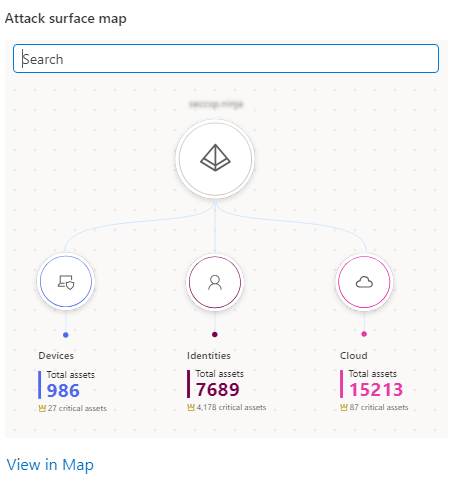
Review assets in the map
The Attack surface map displays your tenant's total and critical device, identity, and cloud assets.
You can select and search on a specific asset type, and open it in the map.
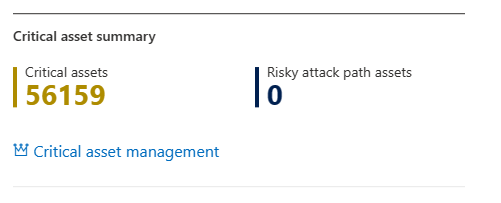
Review and manage critical assets
The Critical asset summary shows you how many critical assets you have and how many have attack paths that put them at risk.
From here you can view and manage critical assets and devices.
In Critical asset management, you can manage the criticality level of assets identified by Security Exposure Management, and create custom classification rules to detect other critical assets.
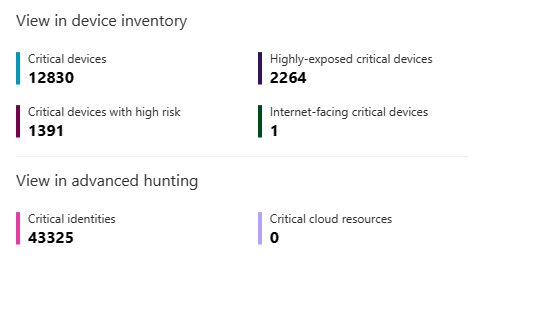
View in device inventory and advanced hunting
You can review critical assets in the context of the Defender XDR device inventory and in Defender XDR advanced hunting.
The device inventory provides quick links to devices sorted by:
- Critical devices
- Critical devices with high risk
- Highly exposed critical devices
- Internet-facing critical devices
In advanced hunting, you can quickly access queries for:
- Critical identities
- Critical cloud resources
Examine key initiative score over time
The Key initiative score over time graph shows each key initiative, color coded, with score changes over time.
You can hover over points on the timeline to see what the score of the key initiative was on that date.
Review recent security events
Recent security events displays security events from the past week sorted by all events or by either initiatives or metrics drop. Select the View all events button to view a complete list of all events in the last 30 days occurring in your organization.