Zero Trust adoption framework overview
Digital transformation is shaping a new normal. Organizations are embracing digital transformation to manage continuous business environment changes by tracking:
- Shifting business models and partnerships.
- Technology trends.
- Regulatory, geopolitical, and cultural forces.
Additionally, COVID-19 remote work accelerated this transformation and is shifting security from a cost center to a strategic driver for growth.
Zero Trust is security for digital business. Digital transformation requires updating traditional security models because traditional security approaches don’t meet current requirements for business agility, user experiences, and continuously evolving threats. Organizations are implementing Zero Trust to address these challenges and enable the new normal of working anywhere, with anyone, at any time.
However, shifting from a traditional security model to Zero Trust represents a significant transformation that requires buy-in, adoption, and change management across an entire organization. Business leaders, technology leaders, security leaders, and security practitioners all play critical parts in creating an agile Zero Trust security approach.
Many security architects and IT teams ask for help with communicating to business leaders, tracking progress, and driving adoption. This guidance helps security and technology teams collaborate with business leaders on Zero Trust by providing:
- Recommended Zero Trust objectives for business leaders across organizations.
- A methodical and phased approach to implementing a Zero Trust architecture.
- A systematic way to track progress, scoped to business leaders.
- Curation of the most relevant resources for adoption of Zero Trust from slides that are ready to present to business leaders to technical implementation guidance and user infographics.
"Our goal is to help every organization strengthen its security capabilities through a Zero Trust architecture built on our comprehensive solutions that span identity, security, compliance, and device management across all clouds and platforms." –Satya Nadella, executive chairman and CEO of Microsoft
As a Microsoft partner, NBConsult contributed to and provided material feedback to this adoption guidance.
Zero Trust protects business assets wherever they are located and wherever they go. Zero Trust is a proactive, integrated approach to security that requires knowing what business assets and processes are most important to protect, and securing these while preserving business agility.
Adopting a Zero Trust approach requires buy-in across the C-suite. As the threat landscape expands, and critical attacks become more common, business leaders across functional areas are increasingly concerned with the cybersecurity approach their organization's take.
Zero Trust allows the entire C-suite and business to embrace a measurable business outcome that is aligned to reducing threats and increasing productivity.
Zero Trust adds value to two predominant scenarios that are seen in the marketplace:
- A formal security strategy aligned to business outcomes. This Zero Trust approach provides a holistic view on security to the entire business, through values that are shared across the business and adopted at every level from the top down. This is often CISO-led and business outcomes are tracked as part of the reporting function of Zero Trust in an ongoing manner.
- Delegated security to IT functions where security is treated as another technology vertical with minimal C-suite input and integration. This often focuses on short term cost optimization for security rather than managing it as a business risk, often further separating security into non-integrated "best of breed" independent solutions.
Zero Trust provides a way of integrating the vertical solutions into a single vision. This vision supports consistent business capabilities and outcomes and provides ongoing measurable metrics on the state of security.
Traditionally the CISO or IT/Security manager sets strategy, or at least security technology choices. However, buy-in from the other C-level leaders is required to justify additional "security" spending. Under the Zero Trust security strategy, other C-suite members are required to take part in the Zero Trust journey, understanding that security is a shared business responsibility aligned to business outcomes.
The following is a generalized view of the possible functions taken by various C-level functions and how they align to an integrated vision of security using Zero Trust.
| Role | Responsibility | Zero Trust interest |
|---|---|---|
| Chief Executive Officer (CEO) | Responsible for the business | Zero Trust provides an integrated approach to security across all digital layers. |
| Chief Marketing Officer (CMO) | Responsible for the marketing vision and execution | Zero Trust allows for the rapid recovery from breach and empowers the responsible reporting function for a public-facing organization, allowing breaches to be contained without reputational loss. |
| Chief Information Officer (CIO) | Responsible for IT as a whole | Zero Trust principles eliminate vertical security solutions that aren't aligned to business outcomes and enables Security as a Platform, which does align to business outcomes. |
| Chief Information Security Officer (CISO) | Responsible for security program implementation | Zero Trust principles provide a sufficient foundation for the organization to comply with various security standards and enables the organization to secure data, assets, and infrastructure. |
| Chief Technology Officer (CTO) | Chief Architect in the business | Zero Trust helps with defensible technology alignment aligned to business outcomes. Using Zero Trust, security is baked into every architecture. |
| Chief Operations Officer (COO) | Responsible for operational execution | Zero Trust helps with operational governance; the "how to" of the security vision and the surfacing of who did what and when. Both are aligned to business outcomes. |
| Chief Financial Officer (CFO) | Responsible for governance and spend | Zero Trust helps with the accountability of spend and the defensibility of spend; a measurable way of gaining a risk-based measure against security and Zero Trust spending aligned to business outcomes. |
Zero Trust is a strategy and architecture based on three principles.
| Principle | Technical description | Business description |
|---|---|---|
| Verify explicitly | Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies. | This principle requires users to verify who they are, using more than one method, so that compromised accounts gained by hackers aren't allowed to access your data and apps. This approach also requires devices to be recognized as being allowed to access the environment and, ideally, to be managed and healthy (not compromised by malware). |
| Use least privileged access | Limit user access with just-in-time and just-enough-access (JIT/JEA), risk-based adaptive policies, and data protection to help secure both data and productivity. | This principle limits the blast radius of a potential breach so that if an account is compromised, the potential damage is limited. For accounts with greater privileges, such as administrator accounts, this involves using capabilities that limit how much access these accounts have and when they have access. It also involves using higher-levels of risk-based authentication policies for these accounts. This principle also involves identifying and protecting sensitive data. For example, a document folder associated with a sensitive project should only include access permissions for the team members who need it. These protections together limit how much damage can be caused by a compromised user account. |
| Assume breach | Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses. | This principle assumes the likelihood that an attacker will gain access to an account, identity, endpoint, application, API, or other asset. To respond, Microsoft protects all of the assets accordingly to limit the damage. This principle also involves implementing tools for ongoing threat detection and rapid response. Ideally these tools have access to signals integrated across your environment and can take automated actions, such as disabling an account, to reduce the damage as soon as possible. |
The three principles of Zero Trust are applied across defense areas. These are sometimes referred to as functional areas or disciplines of IT management. Many organizations are structured around these areas with teams of specialized individuals.
Zero Trust requires taking an integrated approach across these areas and teams, which is why it's so important to have buy-in across the C-suite and a well-orchestrated strategy and plan across your organization.
| Functional area | Technical definition | Business translation |
|---|---|---|
| Identities | Human and non-human identities, including users, computers, and service principals. Anything that can authenticate. | Anything human or machine based that is able to sign in or use your services. |
| Endpoints | End user computing devices, including computers, laptops, mobile phones, and tablets. | The devices our users use to connect to your services and operate on your data. |
| Apps | Cloud or datacenter-based applications that require users to sign in and consume those services or applications. | All apps that are used by your organization, including SaaS apps that you subscribe to and other applications, whether in the cloud or on-premises. |
| Infrastructure | Infrastructure as a Service (IaaS) or datacenter-based infrastructure, including network components, servers, and data storage. | These are the technical foundations and components that support your organization, including physical and virtual servers hosted in your datacenter or a cloud service. |
| Data | Structured, unstructured, and application- contained data. | Your businesses data contained in files, databases, or other applications (such as CRM). |
| Network | LAN, WAN, wireless, or internet connection, including mobile (such as 3G and 5G) or even the coffee shop wireless network. | The network used to connect your users to the services they need. This might be a corporate-run local area network (LAN), the wider network encompassing access to your digital estate, or the internet connections used by your workers to connect. |
When applying Zero Trust strategy across a digital estate, it’s less helpful to think about tackling each of these domain areas independently. It’s not as if the identity team can accomplish all the recommendations and then the Zero Trust focus can move to the team that manages endpoints. Zero Trust strategy applies these functional areas together to secure an area within a digital estate and then broaden the scope of the protection across it.
For example, the identity team can only make so much progress in utilizing Microsoft Entra Conditional Access policies before coordinating with the endpoints team to weave together protection.
The following diagram integrates these functional areas into a unified Zero Trust architecture.
In the diagram:
- Each of the functional areas is represented: Identities, Endpoints, Network, Data, Apps, Infrastructure
- Zero Trust integrates protection across all the functional areas through policies and Policy Optimization.
- Threat protection brings together signals across the organization in real-time to provide visibility into attacks and to streamline remediation through automated actions and incident response tracking.
The next section discusses how to get started on the Zero Trust journey. We’ll use the Identities functional area as an example.
Customers who are familiar with the Cloud Adoption Framework for Azure have asked, "Where’s the Zero Trust adoption framework?"
The Cloud Adoption Framework for Azure is a methodical process for introducing new apps and services into an organization. The focus is primarily on a proven process an organization can follow to introduce an app or service into the environment. The scale motion is repeating the process for each app that is added to a digital estate.
Adoption of a Zero Trust strategy and architecture requires a different scope. It's about introducing new security configurations across an entire digital estate. The scale motion is two dimensional:
- Taking a piece of the Zero Trust architecture, such as data protection, and scaling out this protection across the entire digital estate.
- Repeating the process with each additional piece of the Zero Trust architecture, starting with strategic quick wins and foundational pieces, and then advancing to more complex pieces.
Like the Cloud Adoption Framework for Azure, this Zero Trust adoption guidance addresses the work through adoption scenarios as described in the next section.
The following diagram summarizes the differences between these two types of adoption motions.
This Zero Trust adoption guidance uses the same lifecycle phases as the Cloud Adoption Framework for Azure but adapted for Zero Trust.
The following table describes the lifecycle phases.
| Lifecycle phase | Description |
|---|---|
| Define strategy | Build a business case focused on the outcomes most closely aligned with your organization’s risks and strategic goals. |
| Plan |
|
| Ready |
|
| Adopt | Incrementally implement the strategy across functional areas. |
| Govern | Track and measure the success of your deployment. |
| Manage |
|
This Zero Trust adoption guidance recommends building a Zero Trust strategy and architecture through these business scenarios:
- Rapidly modernize your security posture
- Secure remote and hybrid work
- Identify and protect sensitive business data
- Prevent or reduce business damage from a breach
- Meet regulatory and compliance requirements
Each business scenario is described in an article that describes how to progress the technical work through each of the lifecycle phases, starting with building the business case. The most appropriate resources are provided along the way.
Each of these business scenarios breaks down the work of Zero Trust into manageable pieces that can be implemented over four implementation stages. This helps you prioritize, move forward, and track work as you move through the different layers of implementing a Zero Trust architecture.
This guidance includes a PowerPoint slide deck with progress slides that you can use to present the work and track your progress at a high level for business leaders and other stakeholders. The slides include features that help you keep track of and present progress to stakeholders. Here's an example.
This guidance also includes an Excel workbook with worksheets for each business scenario that you can use to assign owners and track progress for each stage, objective, and task. Here's an example.
Across the business scenarios, the implementation stages are roughly aligned so that accomplishing the objectives of Stage 1 across the scenarios help keep your organization progressing on all fronts together.
If you're embarking on a Zero trust journey that is aligned to a business scenario or looking to embrace Zero Trust as a strategic defense doctrine, success can be difficult to measure. This is because security doesn't pass a simple pass/fail type of evaluation. Rather, security is a commitment and a journey, to which Zero Trust supplies guiding principles.
Using this adoption guidance as a process framework, first establish and document our security strategy, very similar to a Project Initiation Document (PID). Using the principles that apply to strategy, at minimum, you should document:
- What are you doing?
- Why are you doing it?
- How do you agree on and measure success?
Each business scenario encompasses a different set of assets with different tools to take inventory. Methodically, you begin with an inventory and classification of the assets for each business scenario:
- Asset Identification: What assets do you want to protect, such as identities, data, apps, services, and infrastructure? You might use the functional areas called out above as a guide of where to start. Asset identification forms part of your Define strategy and Plan lifecycle phases. The Define strategy phase can articulate a specific scenario, while the Plan phase documents the digital estate.
- Asset Classification: How important is each one of the identified assets, such as identities, business critical data, and human resources data? Asset classification is part of the Ready phase where you begin to identify the protection strategy for each asset.
- Asset Management: How do you choose to protect (govern) and administer (manage) these assets?
- Asset Recovery: How do you recover from compromise or loss of control of an asset (govern)?
Each business scenario recommends how to take inventory as well as how to protect the assets and report on progress. While there's inevitably some overlap across the business scenarios, this adoption guidance attempts to simplify as much as possible by addressing asset types in predominantly one business scenario.
Tracking your progress throughout the Zero Trust adoption process is crucial as it allows your organization to monitor and measure strategic goals and objectives.
Microsoft recommends taking two approaches to tracking your progress:
- Measure your progress against mitigating risks to your business.
- Measure your progress towards achieving strategic objectives across the Zero Trust architecture.
Many organizations use International Organization for Standardization (ISO) standards resources and tools to gauge an organization’s risk. Specifically:
ISO/IEC 27001:2022
- Information security, cybersecurity, and privacy protection
- Information security management systems
- Requirements
ISO 31000
- Risk management
The requirements and guidelines in these standards are generic and can apply to any organization. They provide a structured and comprehensive way for you to review and gauge the risks that apply to your organization, as well as mitigations.
Identifying and understanding the specific risks that apply to your organization will help you prioritize your most strategic objectives across the Zero Trust architecture.
Once your organization has identified and prioritized your most strategic technical objectives, you can map out a staged roadmap for implementation. You can then track your progress by using various tools.
Microsoft provides customizable PowerPoint and Excel tracking tools. These are pre-populated with objectives and tasks, organized by Zero Trust business scenarios. You can customize these with your own priorities, objectives, and team members.
- Business leader tracker — A downloadable PowerPoint slide deck with progress tracking slides. These are designed to help you track and communicate progress at a high level. Customize these slides for your own use.
- Implementer tracker — A downloadable Excel workbook to assign ownership and track your progress through the stages, objectives, and tasks. For business scenario project leads, IT leads, and IT implementers.
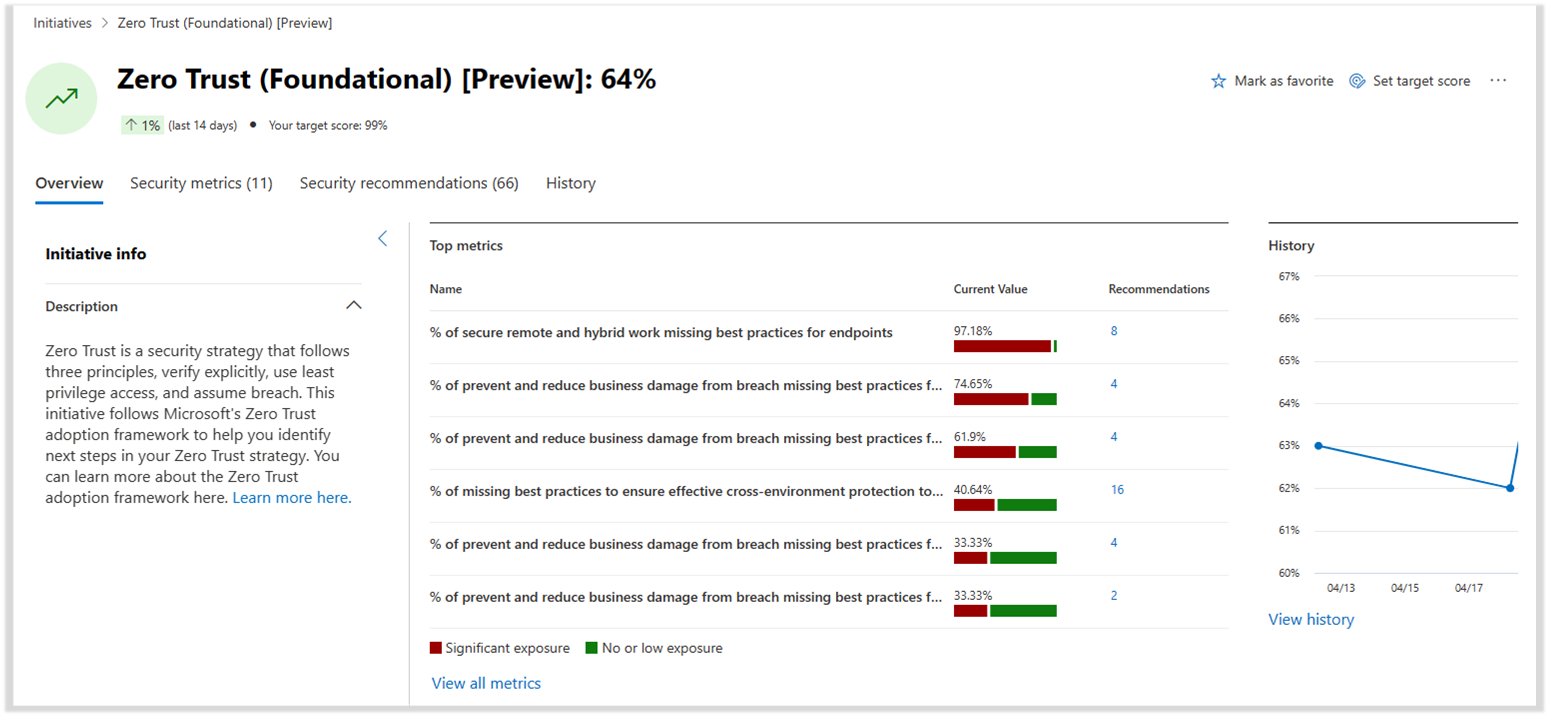
Microsoft Security Exposure Management is a security solution that provides a unified view of security posture across company assets and workloads. Within this tool, Security Initiatives help you assess readiness and maturity in specific areas of security risk. Security Initiatives take a proactive approach to managing security programs towards specific risk or domain-related objectives.
Use the Zero Trust initiative to track your organization’s progress toward implementing Zero Trust security. This initiative is aligned with this Microsoft Zero Trust adoption framework, allowing you to track your progress with metrics aligned with business scenarios. These metrics capture your resource coverage across prioritized actionable recommendations to help security teams protect their organization. The initiative also provides real-time data on your Zero Trust progress that can be shared with stakeholders.
For more information about how to use the Zero Trust initiative within the Exposure Management tool, see Rapidly modernize your security posture — Track and measure.
Additionally, several other portals and reports can assist you in creating an overview of risk within your business, including:
- The Critical Asset Protection initiative in Microsoft Security Exposure Management brings together critical asset risk across Defender products and areas.
- Reports within Microsoft Defender XDR provide information regarding security trends and track the protection status of your identities, data, devices, applications, and infrastructure.
- The Cloud Security Explorer allows you to proactively hunt for security risks.
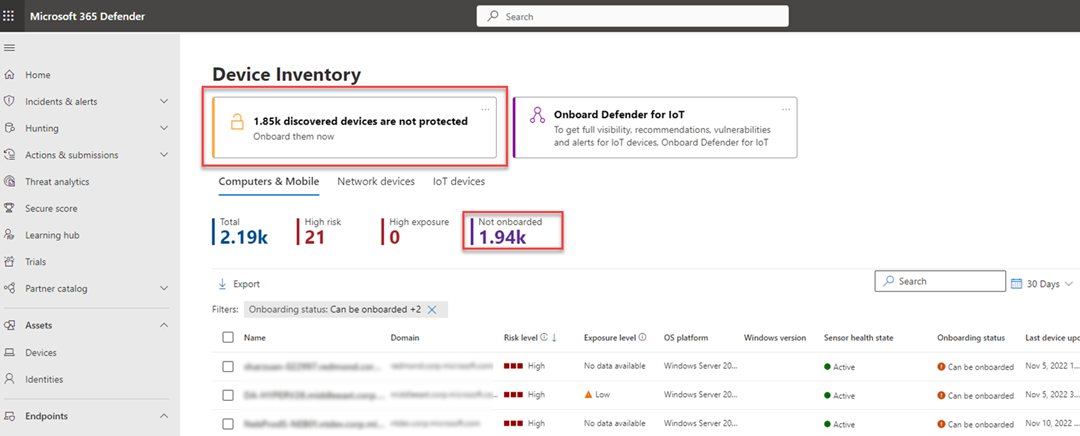
For example, within Microsoft Defender XDR, the device inventory provides a clear view into newly discovered devices in your network that aren't yet protected. At the top of each Device inventory tab, you can see the total number of devices that aren't onboarded. Here's an example.
For more information on using Microsoft Defender XDR to track your progress, see Strengthen your security posture with Microsoft Defender XDR.
Note that the progress percentages provided by in-product tools might not be accurate for organizations that aren't willing to implement all controls due to reasons such as:
- Scope of the business
- Licensing
- Capacity
- Rapidly modernize your security posture
- Secure remote and hybrid work with Zero Trust
- Identify and protect sensitive business data
- Prevent or reduce business damage from a breach
- Meet regulatory and compliance requirements
For each business scenario, you can use the following progress tracking resources.
| Progress tracking resource | That helps you… | Designed for… |
|---|---|---|
Adoption Scenario Plan Phase Grid downloadable Visio file or PDF 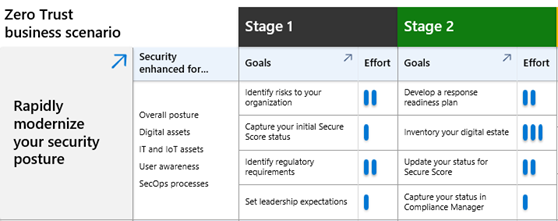
|
Easily understand the security enhancements for each business scenario and the level of effort for the stages and objectives of the Plan phase. | Business scenario project leads, business leaders, and other stakeholders. |
| Zero Trust adoption tracker downloadable PowerPoint slide deck |
Track your progress through the stages and objectives of the Plan phase. | Business scenario project leads, business leaders, and other stakeholders. |
Business scenario objectives and tasks downloadable Excel workbook 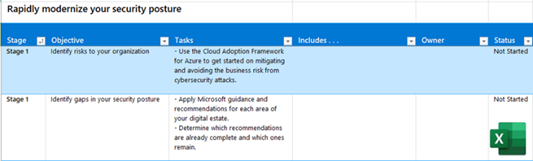
|
Assign ownership and track your progress through the stages, objectives, and tasks of the Plan phase. | Business scenario project leads, IT leads, and IT implementers. |
For additional resources, see Zero Trust assessment and progress tracking resources.
See additional Zero Trust content based on a documentation set or your role in your organization.
Follow this table for the best Zero Trust documentation sets for your needs.
| Documentation set | Helps you... | Roles |
|---|---|---|
| Concepts and deployment objectives for general deployment guidance for technology areas | Apply Zero Trust protections aligned with technology areas. | IT teams and security staff |
| Zero Trust for small businesses | Apply Zero Trust principles to small business customers. | Customers and partners working with Microsoft 365 for business |
| Zero Trust Rapid Modernization Plan (RaMP) for project management guidance and checklists for easy wins | Quickly implement key layers of Zero Trust protection. | Security architects and IT implementers |
| Zero Trust deployment plan with Microsoft 365 for stepped and detailed design and deployment guidance | Apply Zero Trust protections to your Microsoft 365 tenant. | IT teams and security staff |
| Zero Trust for Microsoft Copilots for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Microsoft Copilots. | IT teams and security staff |
| Zero Trust for Azure services for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Azure workloads and services. | IT teams and security staff |
| Partner integration with Zero Trust for design guidance for technology areas and specializations | Apply Zero Trust protections to partner Microsoft cloud solutions. | Partner developers, IT teams, and security staff |
| Develop using Zero Trust principles for application development design guidance and best practices | Apply Zero Trust protections to your application. | Application developers |
Follow this table for the best documentation sets for your role in your organization.
| Role | Documentation set | Helps you... |
|---|---|---|
| Member of an IT or security team | Concepts and deployment objectives for general deployment guidance for technology areas | Apply Zero Trust protections aligned with technology areas. |
| Customer or partner for Microsoft 365 for business | Zero Trust for small businesses | Apply Zero Trust principles to small business customers. |
| Security architect IT implementer |
Zero Trust Rapid Modernization Plan (RaMP) for project management guidance and checklists for easy wins | Quickly implement key layers of Zero Trust protection. |
| Member of an IT or security team for Microsoft 365 | Zero Trust deployment plan with Microsoft 365 for stepped and detailed design and deployment guidance for Microsoft 365 | Apply Zero Trust protections to your Microsoft 365 tenant. |
| Member of an IT or security team for Microsoft Copilots | Zero Trust for Microsoft Copilots for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Microsoft Copilots. |
| Member of an IT or security team for Azure services | Zero Trust for Azure services for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Azure workloads and services. |
| Partner developer or member of an IT or security team | Partner integration with Zero Trust for design guidance for technology areas and specializations | Apply Zero Trust protections to partner Microsoft cloud solutions. |
| Application developer | Develop using Zero Trust principles for application development design guidance and best practices | Apply Zero Trust protections to your application. |