Methodology
The Secure methodology of the Microsoft Cloud Adoption Framework for Azure provides a complete end-state vision to guide your security program's improvement over time. The Secure methodology provides a bridge between your business' digital transformation and your security program and strategy. It also provides structured guidance for modernizing your security disciplines.
Watch the following video to learn more about the Secure methodology and how it helps guide continuing security improvements over time:
The following infographic provides a visual mapping of the key ways security integrates with the larger organization and the disciplines within security:
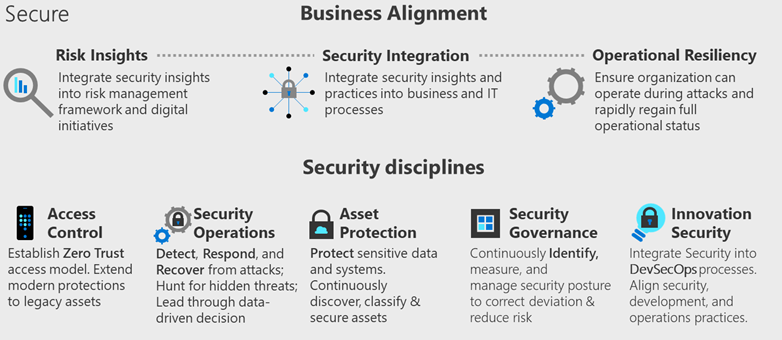
Business alignment
Focus your security program on business alignment in three categories:
- Risk insights: Align and integrate security insights and risk signals and sources to the business initiatives. Ensure repeatable processes educate all teams on the application of those insights and hold teams accountable for improvements.
- Security integration: Integrate security knowledge, skills, and insights deeper into daily business operations and IT environment. Use repeatable processes and develop a deep partnership at all levels of the organization.
- Business resilience: Prevent as many attacks as possible and limit the damage of those attacks to foster organizational resilience. Ensure that you can continue operations during an attack, even if at a degraded state. Also ensure the organization rapidly bounces back to full operations.
Security disciplines
Cloud migration affects each security discipline differently. Each of these disciplines is important and requires continuous investment and improvement as you adopt the cloud.
- Access control: Apply network and identity create access boundaries and segmentation to reduce the frequency and reach of any security breaches.
- Security operations: Monitor IT operations to detect, respond, and recover from a breach. Use data to continuously reduce risk of breach.
- Asset protection: Maximize protection of infrastructure, devices, data, applications, networks, and identities to minimize risk to the overall environment.
- Security governance: Monitor decisions, configurations, and data to govern decisions made across the environment and within all workloads across the portfolio.
- Innovation security: Integrate security into your DevOps models to improve security and safety assurances as you increase the pace of innovation in your organization. To avoid expensive security incidents and late-stage mitigation, security must become an integral part of a DevSecOps process. Empower workload teams to quickly identify and mitigate security risks.