Describe Microsoft Defender Vulnerability Management
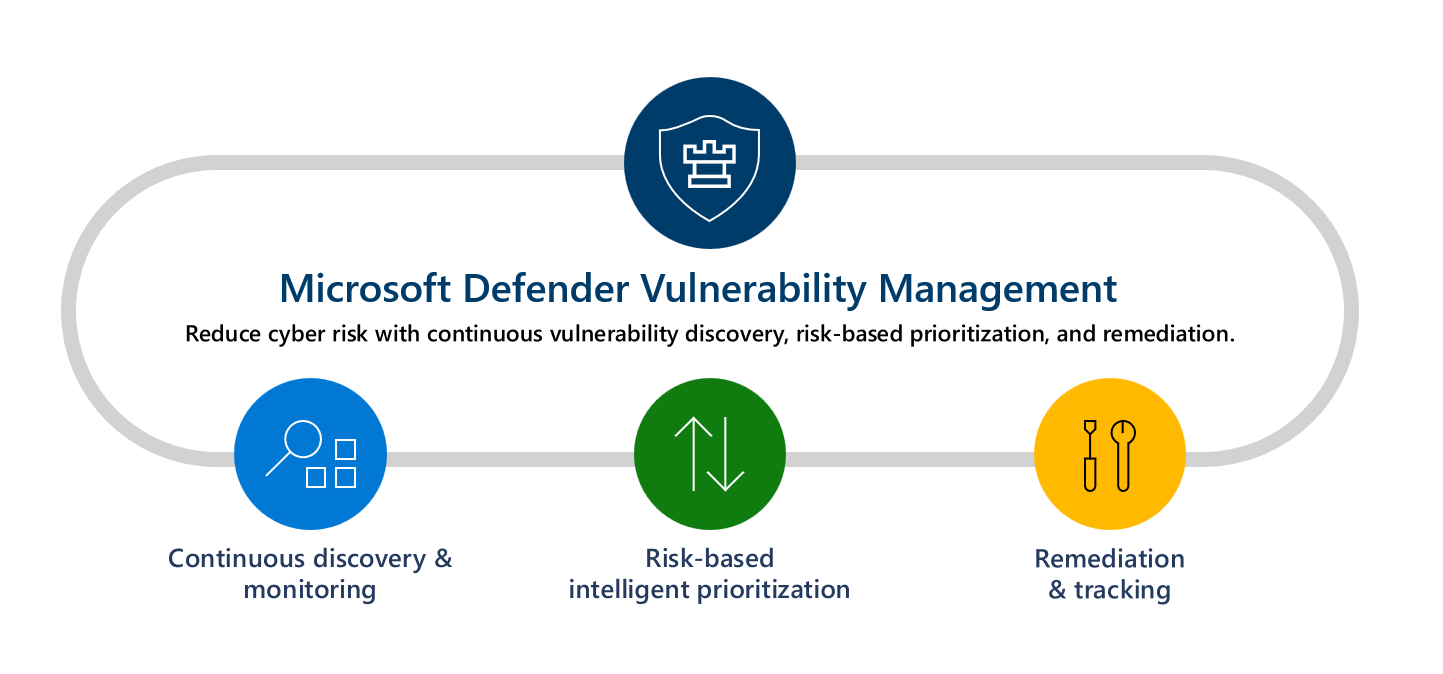
Defender Vulnerability Management delivers asset visibility, intelligent assessments, and built-in remediation tools for Windows, macOS, Linux, Android, iOS, and network devices.
Using Microsoft threat intelligence, breach likelihood predictions, business contexts, and devices assessments, Defender Vulnerability Management rapidly and continuously prioritizes the biggest vulnerabilities on your most critical assets and provides security recommendations to mitigate risk.
Continuous asset discovery and monitoring
Defender Vulnerability Management built-in and agentless scanners continuously monitor and detect risk in your organization even when devices aren't connected to the corporate network.
Consolidated inventories provide a real-time view of your organization's software applications, digital certificates, hardware and firmware, and browser extensions to help you monitor and assess all your organization's assets. Examples include:
- Visibility into software and vulnerabilities - Get a view of the organization's software inventory, and software changes like installations, uninstalls, and patches.
- Network share assessment - Assess vulnerable internal network shares configuration with actionable security recommendations.
- Browser extensions assessment - View a list of the browser extensions installed across different browsers in your organization. View information on an extension's permissions and associated risk levels.
- Digital certificates assessment - View a list of certificates installed across your organization in a single central certificate inventory page. Identify certificates before they expire and detect potential vulnerabilities due to weak signature algorithms.
- And more...
Risk-based intelligent prioritization
Defender Vulnerability Management uses Microsoft's threat intelligence, breach likelihood predictions, business contexts, and device assessments to quickly prioritize the biggest vulnerabilities in your organization.
Risk-based intelligent prioritization focuses on emerging threats to align the prioritization of security recommendations with vulnerabilities currently being exploited in the wild and emerging threats that pose the highest risk. Risk-based intelligent prioritization also pinpoints active breaches and protects high value assets.
A single view of prioritized recommendations from multiple security feeds, along with critical details including related Common Vulnerabilities and Exposures (CVEs) and exposed devices, helps you quickly remediate the biggest vulnerabilities on your most critical assets.
Remediation and tracking
Remediation and tracking enable security administrators and IT administrators to collaborate and seamlessly remediate issues with built-in workflows.
- Remediation requests sent to IT - Create a remediation task in Microsoft Intune from a specific security recommendation.
- Block vulnerable applications - Mitigate risk with the ability to block vulnerable applications for specific device groups.
- Alternate mitigations - Gain insights on other mitigations, such as configuration changes that can reduce risk associated with software vulnerabilities.
- Real-time remediation status - Real-time monitoring of the status and progress of remediation activities across the organization.
Microsoft Defender Vulnerability Management in the Microsoft Defender portal
Microsoft Defender Vulnerability Management is experienced through the Microsoft Defender portal. The Defender portal is the home for monitoring and managing security across your Microsoft identities, data, devices, apps, and infrastructure, allowing security admins to perform their security tasks, in one location.
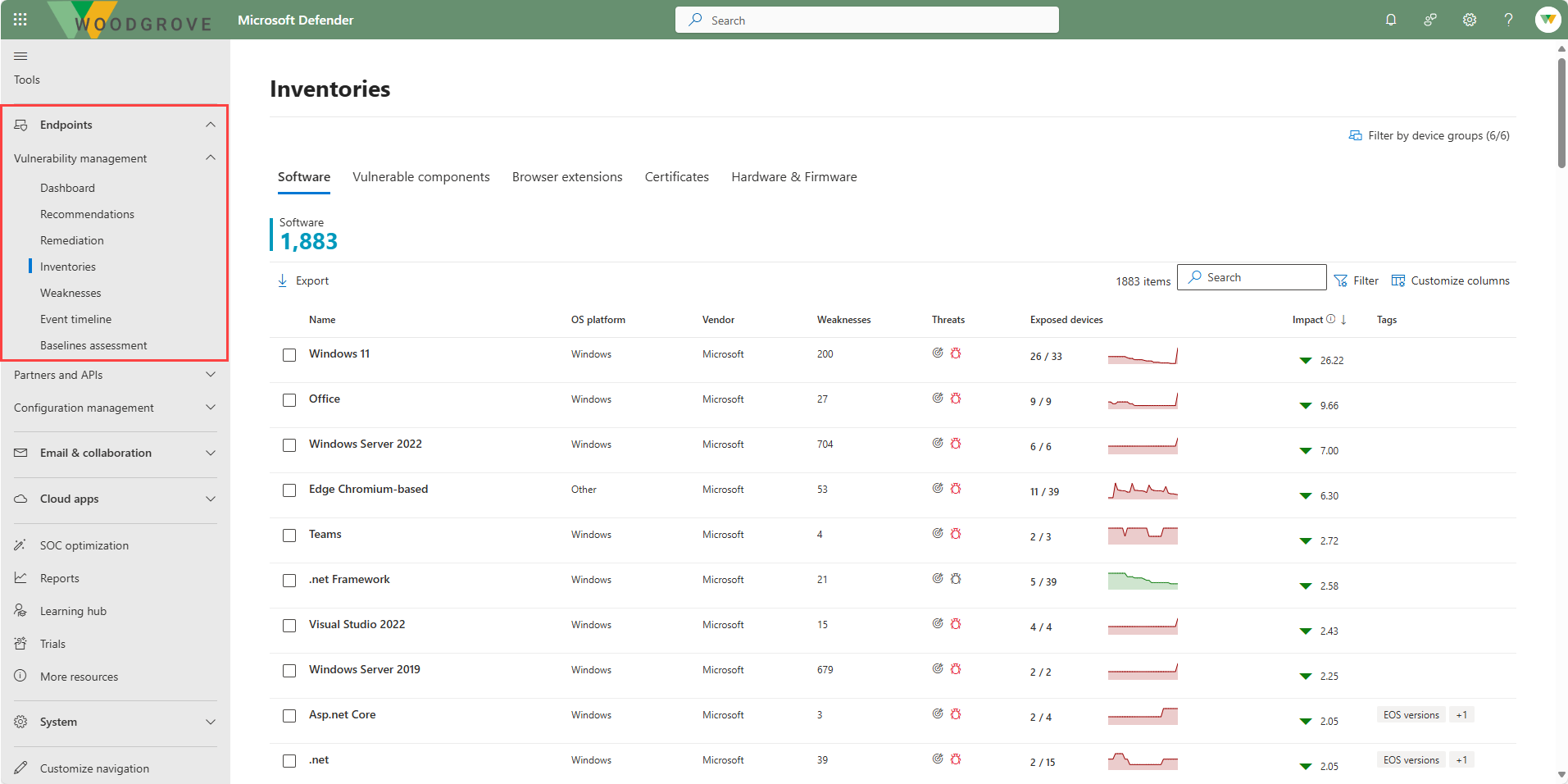
The Vulnerability management node is listed under Endpoints on the left navigation panel of the Microsoft Defender portal. From this section, you can access Microsoft Defender Vulnerability functionality.
- Dashboard - You can use Defender Vulnerability Management dashboard in the Microsoft Defender portal to view your exposure score and Microsoft Secure Score for Devices, along with top security recommendations, software vulnerability, remediation activities, exposed devices, and more.
- Recommendations - From the recommendations page, you can view recommendations, the number of weaknesses found, related components, threat insights, number of exposed devices, and much more.
- Remediation - When you submit a remediation request from the Security recommendations page, it kicks off a remediation activity. A security task is created that can be tracked on a Remediation page. From the Remediation page, you can follow the remediation steps, track progress, view the related recommendation, export to CSV, or mark as complete.
- Inventories - The Software inventory page opens with a list of software installed in your network, including the vendor name, weaknesses found, threats associated with them, exposed devices, impact to exposure score, and tags. Software that isn't currently supported by vulnerability management may be present in the software inventory page, but because it isn't supported, only limited data will be available.
- Weaknesses - The Weaknesses page opens with a list of the CVEs your devices are exposed to. You can view the severity, Common Vulnerability Scoring System (CVSS) rating, corresponding breach and threat insights, and more.
- Event timeline - The Event timeline helps you interpret how risk is introduced into the organization through new vulnerabilities or exploits. You can view events that may impact your organization's risk. You can view the all the necessary info related to an event.
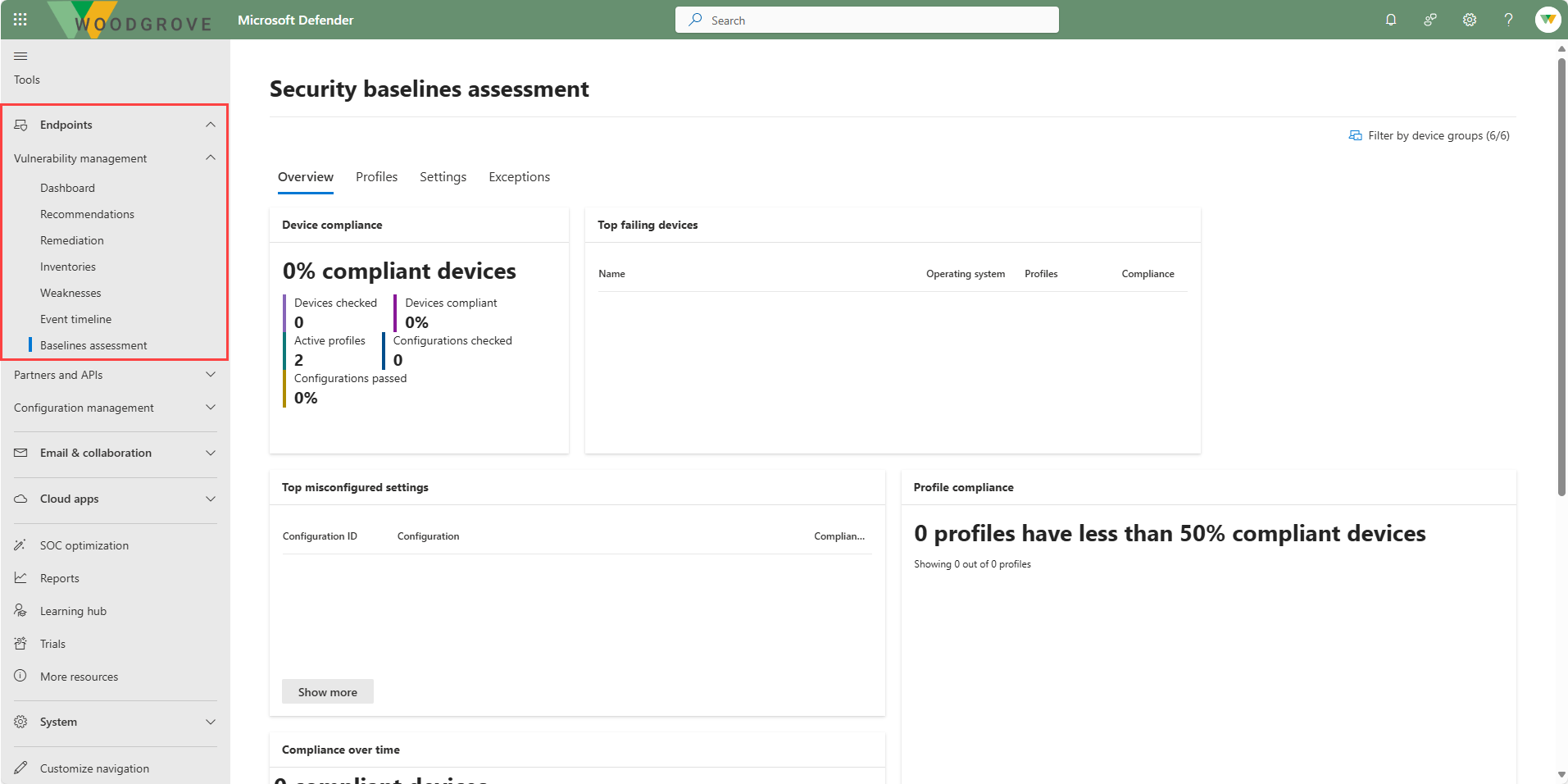
- Baseline assessments - A security baseline profile is a customized profile that you create to assess and monitor endpoints in your organization against industry security benchmarks. On the security baselines assessment overview page you can view device compliance, profile compliance, top failing devices, and top misconfigured devices for the available baselines.
Settings, permissions, incidents and alerts, reports and other features are also available through the Microsoft Defender portal. More information is covered in the unit, "Describe the Microsoft Defender portal," included in this module.