Explore the vulnerabilities and risk events detected by Microsoft Entra ID Protection
This unit examines the vulnerabilities detected by Microsoft Entra ID Protection and the risk events detected by Microsoft Entra ID.
Vulnerabilities detected by Microsoft Entra ID Protection
A vulnerability is a weakness that an attacker can exploit to do unauthorized actions within a computer system. Recommended solutions enable organizations to address these vulnerabilities to improve their security posture and prevent attackers from exploiting them.
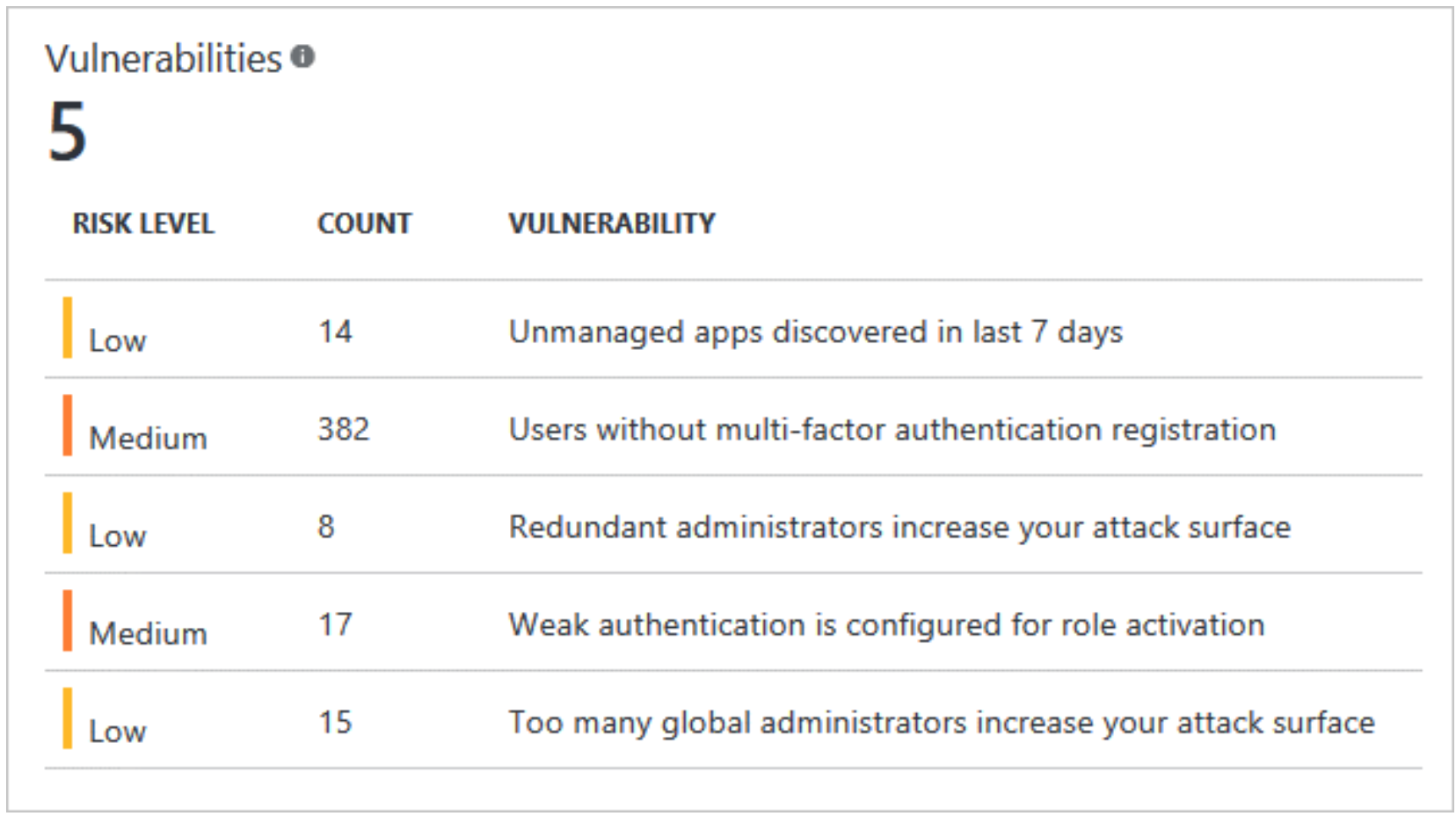
The following sections provide an overview of the vulnerabilities reported by Microsoft Entra ID Protection, along with recommendations on how to address those issues.
Multifactor authentication registration not configured
This vulnerability can affect the deployment of Microsoft Entra multifactor authentication in an organization. Multifactor authentication provides a second layer of security to user authentication. It helps safeguard access to data and applications while meeting user demand for a simple sign-in process. Multifactor authentication delivers strong authentication through a range of easy verification options, such as:
- phone call
- text message
- mobile app notification
- verification code
- third-party OATH tokens
Recommended Action: Microsoft recommends that you require Microsoft Entra multifactor authentication for user sign-in attempts. Multifactor authentication plays a key role in risk-based conditional access policies available through Microsoft Entra ID Protection.
Unmanaged cloud apps
This vulnerability helps you identify unmanaged cloud apps in your organization. In modern enterprises, IT departments are often unaware of all the cloud applications that users in their organization are using to do their work. It's easy to see why administrators have concerns about unauthorized access to corporate data, possible data leakage, and other security risks.
Recommended Action: Microsoft recommends that you deploy Cloud App Discovery to discover unmanaged cloud applications. Once you identify these unmanaged cloud apps, Microsoft recommends that you manage them using Microsoft Entra ID.
Security alerts from Privileged Identity Management
This vulnerability helps you discover and resolve alerts about privileged identities in your organization. To enable users to carry out privileged operations, organizations must grant users temporary or permanent privileged access in Microsoft Entra ID, Azure or Microsoft 365 resources, or other SaaS apps. Each of these privileged users increases the attack surface for an organization. This vulnerability helps organizations identify users with unnecessary privileged access. By doing so, organizations can take appropriate action to reduce or eliminate the risk these users pose.
Recommended Action: Microsoft recommends that organizations use Microsoft Entra Privileged Identity Management (PIM) to manage, control, and monitor privileged identities. PIM can manage access of these identities to resources in Microsoft Entra ID and other Microsoft online services, such as Microsoft 365 and Microsoft Intune.
Risk events detected by Microsoft Entra ID
Most security breaches occur when attackers gain access to an environment by stealing a user’s identity. Discovering compromised identities is no easy task. Microsoft Entra ID uses adaptive machine learning algorithms and heuristics to detect suspicious actions that are related to an organization’s user accounts. It stores each detected suspicious action in a record called a risk event.
Currently, Microsoft Entra ID detects six types of risk events:
- Users with leaked credentials
- Sign in attempts from anonymous IP addresses
- Impossible travel to atypical locations
- Sign in attempts from infected devices
- Sign in attempts from IP addresses with suspicious activity
- Sign in attempts from unfamiliar locations
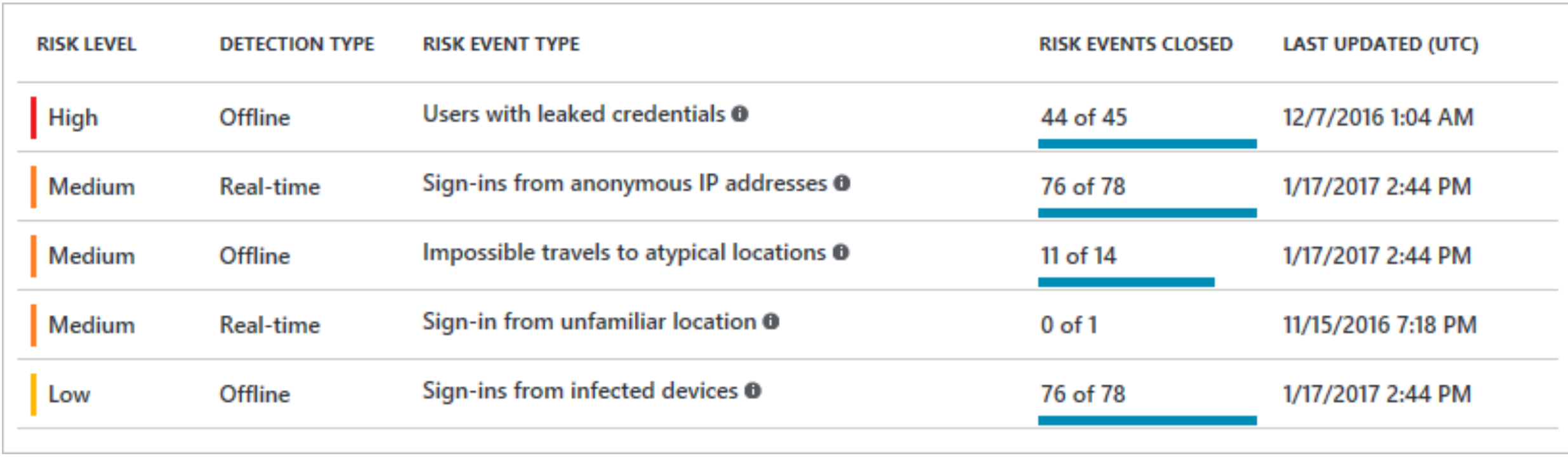
The following table outlines the parameters that define each risk event type.
| Detection Type | Reporting Latency |
|---|---|
| Real-time | 5 to 10 minutes |
| Offline | 2 to 4 hours |
| Risk Level | Description |
| High | High confidence and high severity risk events. The events strongly indicate that someone compromised the user's identity, and the company should remediate any affected user accounts. |
| Medium | High severity and lower confidence risk event, or low severity and high confidence risk event. These events are potentially risky, and the company should remediate any affected user accounts. |
| Low | Low confidence and low severity risk event. This event might not require an immediate action. However, when you combine it with other risk events, it can strongly indicate that someone compromised the user's identity. |
Note
Your Microsoft Entra subscription ties the insight you receive for a detected risk event. With the Microsoft Entra Premium P2 edition, you get the most detailed information about all underlying detections. The Microsoft Entra Premium P1 edition shows the following risk event for detections not covered by your license: Sign in with additional risk detected.
Microsoft Entra ID creates a risk event record for a suspicious action. The identifier for the suspicious action is the risk event type. The following sections introduce each of the risk event types currently tracked in Microsoft Entra ID.
Users with leaked credentials
Cybercriminals often share credentials when they compromise valid passwords of legitimate users. Criminals share credentials by:
- Posting them publicly on the dark web or paste sites.
- Trading or selling the credentials on the black market.
The Microsoft Leaked Credentials Service acquires username/password pairs by monitoring public and dark web sites and by working with:
- Researchers
- Law enforcement
- Security teams at Microsoft
- Other trusted sources
When the service acquires username/password pairs, it checks them against the Microsoft Entra ID user's current credentials. If it detects a match, it indicates that someone compromised the user's password. As a result, the service creates a leaked credentials risk event.
Sign-ins from anonymous IP address
This risk event type identifies users who successfully signed in from an IP address the system identified as an anonymous proxy IP address. People use these proxies when they want to hide their device’s IP address. Attackers often use these proxies for malicious intent.
Impossible travel to atypical locations
This risk event type identifies two sign-in attempts that originate from geographically distant locations. At least one of the locations might also be atypical for the user, given past behavior. Among several other factors, this machine learning algorithm considers:
- The time between the two sign-in attempts.
- The time it would take for the user to travel from the first location to the second.
The risk event type can compare these two values and determine whether it's possible that a different user used the same credentials in the second sign-in attempt.
The algorithm ignores obvious "false positives" contributing to the impossible travel conditions. For example, VPNs and locations regularly used by other users in the organization. The system has an initial learning period of 14 days. During this time, it's able to learn a new user’s sign-in behavior.
Sign in from unfamiliar locations
This risk event type considers past sign-in locations (IP, Latitude/Longitude, and ASN) to determine new or unfamiliar locations. The system stores information about previous locations from which a user signed in. It considers these “familiar” locations. The system triggers a risk event when the sign-in occurs from a location that's not already in the list of familiar locations. The system has an initial learning period of 30 days. During this time, the system doesn't flag any new locations as unfamiliar locations. The system also ignores sign in attempts from familiar devices, and locations that are close to a familiar location.
Microsoft Entra ID Protection also detects sign in attempts from unfamiliar locations for basic authentication/legacy protocols. Because these protocols don't have modern familiar features such as client ID, there aren't enough measurements to reduce false positives. To reduce the number of detected risk events, you should move to modern authentication.
Sign in attempts from infected devices
This risk event type identifies sign-in attempts from devices infected with malware that actively communicate with a bot server. Microsoft Entra ID Protection detects this event by correlating IP addresses of the user’s device against IP addresses that were in contact with a bot server.
Sign in attempts from IP addresses with suspicious activity
This risk event type identifies IP addresses that have a high number of failed sign-in attempts across multiple user accounts over a short period of time. This match of traffic patterns of IP addresses used by attackers strongly indicates either compromised accounts or potentially compromised accounts. This machine learning algorithm ignores obvious "false-positives," such as IP addresses regularly used by other users in the organization. The system has an initial learning period of 14 days where it learns the sign-in behavior of a new user and new tenant.
Knowledge check
Choose the best response for the following question. Then select “Check your answers.”