The Zero Trust security model
Zero Trust is an end-to-end security strategy that monitors and controls the six main pillars of security: identity, endpoints, applications, network, infrastructure, and data.
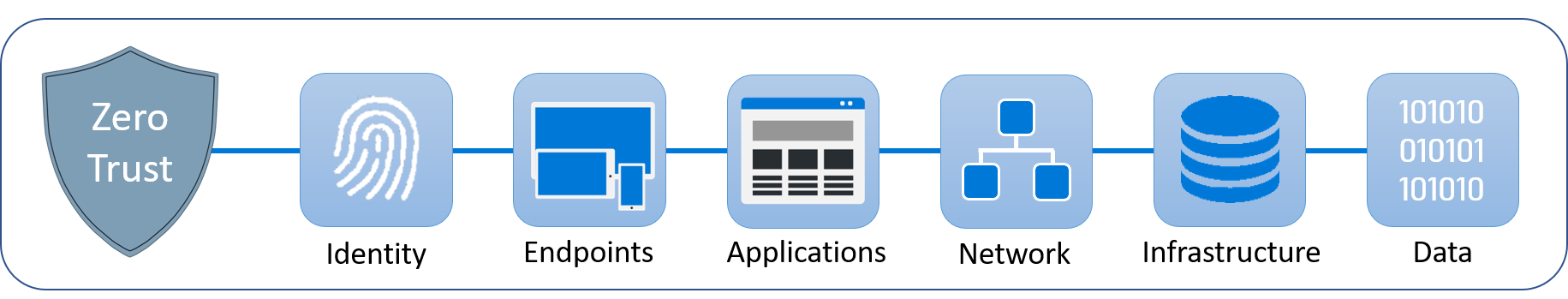
The Zero Trust approach addresses the security concerns that emerge due to the evolving digital landscape. Today, nearly every organization has a mobile, remote or hybrid workforce, cloud applications, data stored in different environments, and devices enrolled from various locations. In the absence of a robust security model, all these factors can inadvertently lead to a major security breach.
In practice, the "trust no one and verify everything" rule suggests that every request, device, or user must not be trusted and should be treated as a potential threat until verified by strong authentication methods, before allowing access to the network. This also means that users and devices are only allowed access to the specific applications or data that they need.
Zero Trust principles
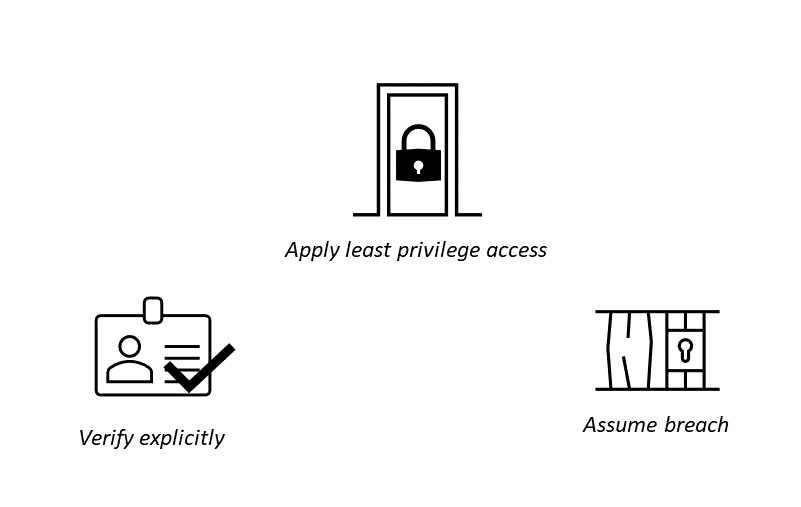
The Zero Trust security framework operates on key principles to provide multiple layers of defense:
- Verify explicitly: Zero Trust requires strict identity verification for every user and device attempting to access resources. With Zero Trust, the identity verification of users and devices is a continuous process, often at multiple levels. This ensures the constant monitoring and validating of who can access what.
- Use least privilege access: The principle of least privilege access ensures that user access is minimized with Just-In-Time (JIT) and Just-Enough-Access (JEA). This means only granting access to systems and applications to authorized users for specific tasks for a minimum time.
- Assume breach: This principle assumes attackers are already in your network and are looking to move laterally and get to get more information. It embodies a deny-all approach and uses real-time monitoring to assess every request against known behaviors to limit and control access. Assume breach is the mindset of creating the necessary segregation of access to contain the damage to a small area, and in doing so, minimizing the impact to your business.