Verifying a Signed Message
These steps verify the signature of signed data. The following illustration depicts the individual tasks that must be accomplished, as shown in the list that follows it.
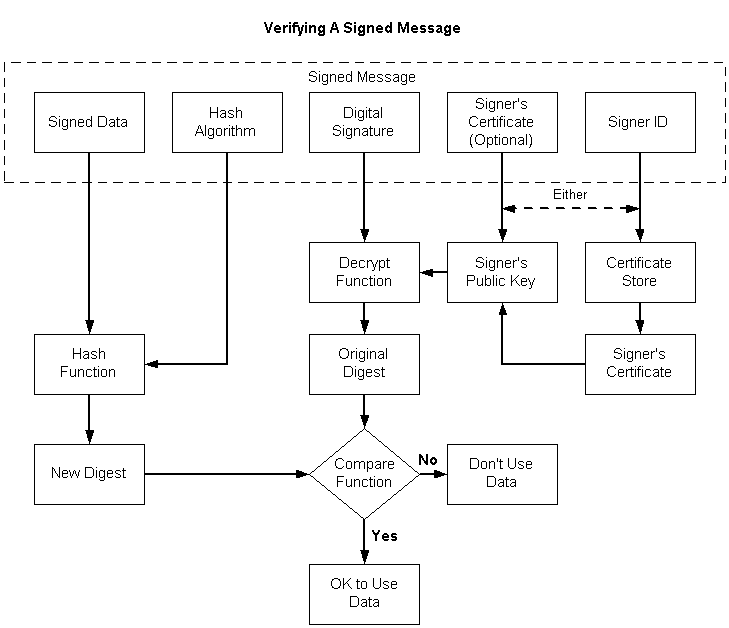
To verify the signature of a signed message
Get a pointer to the signed message.
Open a certificate store.
Using the signer ID contained in the message, get the sender's certificate and get a handle to its public key.
As an alternative to steps 2 and 3, you can use the certificate contained in the message to retrieve the signer's public key.
Using the signer's public key, decrypt the digital signature, producing the original digest of the data in the message.
Using the hash algorithm contained in the message, hash the data contained in the message, yielding a new digest.
Compare the digest retrieved from the message with the new digest just created.
If the two digests match, the signature is verified. This means that the private key that was used to sign the data matches the public key just used to decrypt the signature, and that the data has not changed since the data was signed.
If the two digests do not match, the signature is not verified, and either the private/public keys do not match, or the data has been changed since the data was signed, or both.
A single function, CryptVerifyMessageSignature, can be used to verify a signature, as shown in the following procedure.
To verify a signed message
- Get a pointer to the signed message.
- Get the size of the signed message.
- Get a handle on a cryptographic provider.
- Initialize the CRYPT_VERIFY_MESSAGE_PARA structure.
- Call CryptVerifyMessageSignature to verify the signature.
Code that implements this procedure is included in Example C Program: Signing a Message and Verifying a Message Signature.