How to create a Self-Signed SAN Certificate in Windows 8
One of the cool features of Windows 8 is the improved set of PowerShell commandlets that have been shipped with it. There are several of them which could have made the task a lot easier for the server admins.
In here I will be discussing about one of the commandlets using which we can create a self-signed SSL Certificate. Yes, I mean self-signed and a SAN Certificate.
What you also need to know is that there are no lengthy procedures, it is a simple command with few parameters which adds to the simplicity.
So here are few pre-requisites that I could think of,
- Windows PowerShell and PowerShell ISE needs to be installed.
- OS is either Windows Server 2012 or Windows 8. (I’m not aware if this cmdlet has been back-ported to previous OS versions, I hope they do)
- The Windows PowerShell help menu is updated (Well this is not a necessity, but it will help if this is done.)
Commandlet Name: New-SelfSignedCertificate
Syntax:
New-SelfSignedCertificate [-CertStoreLocation <String>] [-CloneCert <Certificate>] [-DnsName <String>] [-Confirm <SwitchParameter>] [-WhatIf <SwitchParameter>] [<CommonParameters>]
Scenario
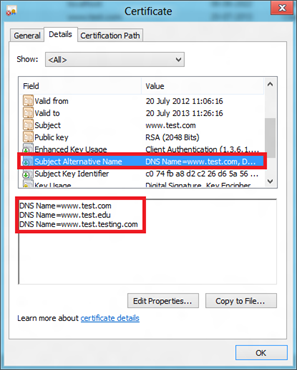
Consider you need to create a self-signed SAN certificate for the following hostnames:
Using the above commandlet the cert can be issued and automatically placed in the personal store of My Computer Account.
Here is the command that we need to execute to generate the cert.
PS C:\> New-SelfSignedCertificate -DnsName www.test.com, www.test.edu, www.test.testing.com -CertStoreLocation cert:\LocalMachine\My Directory: Microsoft.PowerShell.Security\Certificate::LocalMachine\My
Thumbprint Subject ---------- ------- 7020CC054B5818262ECF6C7D9BB2E2546D2B4FD8 CN=www.test.com |
This will install the self-signed cert in the Personal store of machine account.
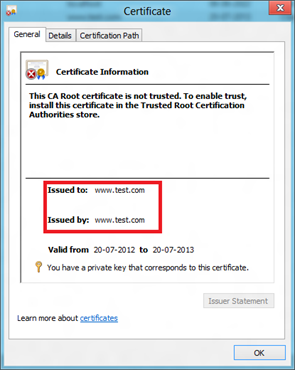
Note: Certificate wouldn’t be trusted. Place the certificate in the Trusted Root CA store and the error will go away.
So this is what the certificate looks like:
It can’t get easier than this.
Another thing worthwhile mentioning is the help menu, which is very descriptive. I have pasted the entire help menu content for the above commandlet below
The good thing is that it also provides descriptive examples.
New-SelfSignedCertificate Help |
Description The New-SelfSignedCertificate cmdlet creates a self-signed certificate for testing purposes. Using the CloneCert parameter, a test certificate can be created based on an existing certificate with all settings copied from the original certificate except for the public key. A new key of the same algorithm and length will be created. If an existing certificate is not being cloned, then an SSL server certificate with the following default settings is created:
Delegation may be required when using this cmdlet with Windows PowerShell® remoting and changing user configuration. Parameters -CertStoreLocation <String> Specifies the certificate store in which a new certificate will be stored. The current path is the default value.
-CloneCert <Certificate> Identifies the certificate to copy when creating a new certificate. The certificate being cloned can be identified by an X509 certificate or the file path in the certificate provider. When this parameter is used, all fields and extensions of the certificate will be inherited except the public key (a new key of the same algorithm and length will be created) and the NotAfter and NotBefore fields (the validity period for the NotBefore field is set to ten minutes in the past).
-DnsName <String> Specifies one or more DNS names to put into the Subject Alternative Name extension of the certificate when a certificate to be copied is not specified via the CloneCert parameter. The first DNS name is also saved as Subject Name and Issuer Name.
-Confirm <SwitchParameter> Prompts you for confirmation before running the cmdlet.
-WhatIf <SwitchParameter> Shows what would happen if the cmdlet runs. The cmdlet is not run.
Microsoft.CertificateServices.Commands.Certificate The Certificate object can either be provided as a Path object to a certificate or an X509Certificate2 object. Outputs System.Security.Cryptography.X509Certificates.X509Certificate2 An X509Certificate2 object for the certificate that has been created. |
Comments
Anonymous
November 09, 2012
Very handy!Anonymous
August 06, 2013
My Windows 8 machine does not have this object (New-SelfSignedCertificate), even with all the requisites installed. Do I need any other program or role installed?Anonymous
August 07, 2013
Did you run the Windows Powershell ISE or something else? This comes as a part of default installation. Could you check this: -- Browse to the folder location: C:WindowsSystem32WindowsPowerShellv1.0ModulesPKI -- Open the file "pki.psd1" -- Here are the contents: =========================================================================== @{ GUID="{cf094c6b-63d1-4dda-bf70-15a602c4eb2b}" Author="Microsoft Corporation" CompanyName="Microsoft Corporation" Copyright="© Microsoft Corporation. All rights reserved." ModuleVersion="1.0.0.0" NestedModules="Microsoft.CertificateServices.PKIClient.Cmdlets" TypesToProcess = 'pki.types.ps1xml' HelpInfoUri='go.microsoft.com/fwlink PowerShellVersion='3.0' CLRVersion='4.0' CmdletsToExport = @('Add-CertificateEnrollmentPolicyServer', 'Export-Certificate', 'Export-PfxCertificate', 'Get-CertificateAutoEnrollmentPolicy', 'Get-Certificate', 'Get-CertificateNotificationTask', 'Get-CertificateEnrollmentPolicyServer', 'Get-PfxData', 'Import-Certificate', 'Import-PfxCertificate', 'New-CertificateNotificationTask', 'New-SelfSignedCertificate', 'Remove-CertificateNotificationTask', 'Remove-CertificateEnrollmentPolicyServer', 'Set-CertificateAutoEnrollmentPolicy', 'Switch-Certificate', 'Test-Certificate') } =========================================================================== If you see the New-SelfSignedCertificate commandlet is present in that file. If it is present then I think there is some other problem. If it is not then you have a bigger problem to address.Anonymous
November 05, 2013
Can you elaborate on how to do this: Note: Certificate wouldn’t be trusted. Place the certificate in the Trusted Root CA store and the error will go away.Anonymous
November 13, 2013
Eric, export the certificate without private key and then import this into the Trusted Root CA store.Anonymous
January 04, 2014
Exactly what I needed. Saved my time.. Thanks !!Anonymous
March 30, 2015
I must be doing something incorrectly or I'm missing a step (entirely possible). The correct output displays in PowerShell, but the certificate is nowhere to be found. Thanks for any help!Anonymous
April 01, 2015
@Karen, the certificate will be present in the certificate store for the computer account. Follow these steps:
- Windows+R
- Enter "MMC" to launch the snap-in
- Go to "File--> Add/Remove Snap-in..."
- This will launch a new window.
- Select "Certificates" and click on "Add >"
- This will prompt another window which provides you the account to choose.
- Select "Computer account" and click on Next
- Click on Finish and then click on OK. Once done you will see Certificates tree in the left pane. Expand it and it will populate the list of stores available under this account. When we specify LocalMachine/My it puts the certificate in the Personal store. Expand the Personal store. You may consider saving the MMC for future use.
Anonymous
July 12, 2015
private key is not exportable by this command. just a suggestion to create a cert with private key exportable: C:Program Files (x86)Microsoft Visual Studio 11.0>makecert -r -pe -n "CN=www.contoso.com, CN=www.test.edu" -b 01/01/2005 -e 01/01/2040 -sky exchange -ss myAnonymous
October 04, 2016
how do you create a cert with a validity period of longer than 1 year?