The Case of the Temporary Registry Profiles
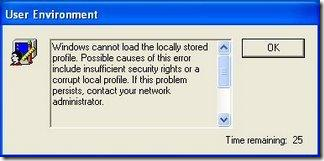
Microsoft Customer Support Services (CSS) is one of the biggest customers of the Sysinternals tools and they often send me interesting cases they’ve solved with them. This particular case is especially interesting because it affected a large number of users and the troubleshooting process made use of one of Process Monitor’s lesser-known features. The case opened when a customer contacted Microsoft support reporting that several of their users would occasionally get this error message when loggging on to their systems:
This caused Windows to create a temporary profile for the user’s logon session. A user profile consists of a directory, %UserProfile%, into which applications save user-specific configuration and data files, as well as a registry hive file stored in that directory, %UserProfile%\Ntuser.dat, that the Winlogon process loads when the user logs in. Applications store user settings in the registry hive by calling registry functions that refer to the HKEY_CURRENT_USER (HKCU) root key. The user’s loss of access to their profile made the problem critical, because whenever that happened, the user would apparently lose all their settings and access to files stored in their profile directory. In most cases, users contacted the company’s support desk, which would ask the user to try rebooting and logging in until the problem resolved itself.
As with all cases, Microsoft support began by asking about the system configuration, inventory of installed software, and about any recent changes the company had made to their systems. In this case, the fact that stood out was that all the systems on which the problem had occurred had recently been upgraded to a new version of Citrix Corporation's ICA client, a remote desktop application. Microsoft contacted Citrix support to see if they knew of any issues with the new client. They didn’t, but said they would investigate.
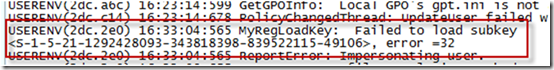
Unsure whether the ICA client upgrade was responsible for the profile problem, Microsoft support instructed the customer to enable profile logging, which you can do by configuring a registry key as per this Knowledge Base article: How to enable user environment debug logging in retail builds of Windows. The customer pushed a script out to their systems to make the required registry changes and shortly after got another call from a user with the profile problem. They grabbed a copy of the profile log off the system from %SystemRoot%\Debug\UserMode\Userenv.log and sent it into Microsoft. The log was inconclusive, but did provide an important clue: it indicated that the user’s profile had failed to load because of error 32, which is ERROR_SHARING_VIOLATION:
When a process opens a file, it specifies what kinds of sharing it allows for the file. If it is writing to the file it may allow other processes to read from the file, for example, but not to also write to the file. The sharing violation in the log file meant that another process had opened the user’s registry hive in a way that was incompatible with the way that the logon process wanted to open the file.
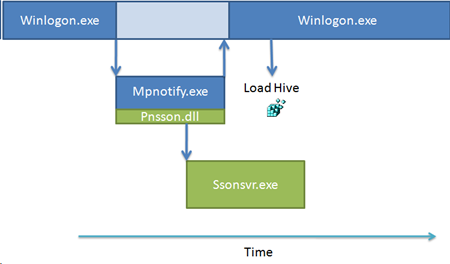
In the meantime, more customers around the world began contacting Microsoft and Citrix with the same issue, all had also deployed the new ICA client. Citrix support then reported that they suspected that the sharing violation might be caused by one of the ICA client’s processes, Ssonvr.exe. During installation, the ICA client registers a Network Provider DLL (Pnsson.dll) that the Windows Multiple Provider Notification Application (%SystemRoot%\System32\Mpnotify.exe) calls when the system boots. Mpnotify.exe is itself launched at logon by the Winlogon process.The Citrix notification DLL launches the Ssonvr.exe process asynchronous to the user’s logon:
The only problem with the theory was that Citrix developers insisted that the process did not attempt to load any user registry profile or even read any keys or values from one. Both Microsoft and Citrix were stumped.
Microsoft created a version of Winlogon and the kernel with additional diagnostic information and tried to reproduce the problem on lab systems configured identically to the client’s, but without success. The customer couldn’t even reproduce the problem with the modified Windows images, presumably because the images changed the timing of the system enough to avoid the problem. At this point a Microsoft support engineer suggested that the customer capture a trace of logon activity with Process Monitor.
There are a couple of ways to configure Process Monitor to record logon operations: one is to use Sysinternals PsExec to launch it in the session 0 so that it survives the logoff and subsequent logon and another is to use the boot logging feature to capture activity from early in the boot, including the logon. The engineer chose the latter, so he told the customer to run Process Monitor on one of the system’s that persistently exhibited the problem, select Enable Boot Logging from the Process Monitor Options menu, and reboot, repeating the steps until the problem reproduced. This procedure configures the Process Monitor driver to load early in the boot process and log activity to %SystemRoot%\Procmon.pmb. Once the user logged encountered the issue, they were to run Process Monitor again, at which point the driver would stop logging and Process Monitor would offer to convert the boot log into a standard Process Monitor log file.
After a couple of attempts the user captured a boot log file that they submitted to Microsoft. Microsoft support engineers scanned through the log and came across the sharing violation error when Winlogon tried to load the user’s registry hive:
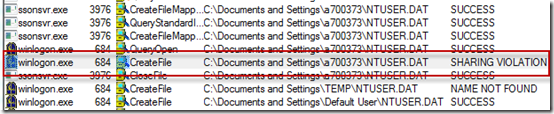
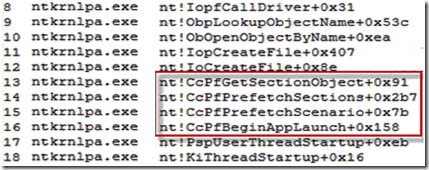
It was obvious from operations immediately preceding the error that Ssonsvr.exe was the process that had the hive opened. The question was, why was Ssonsvr.exe opening the registry hive? To answer that question the engineers turned to Process Monitor’s stack trace functionality. Process Monitor captures a call stack for every operation, which represents the function call nesting responsible for the operation. By looking at a call stack you can often determine an operation’s root cause when it might not be obvious just from the process that executed it. For example, the stack shows you if a DLL loaded into the process executed the operation and, if you have symbols configured and the call originates in a Windows image or other image for which you have symbols, it will even show you the names of the responsible functions.
The stack for Ssonsvr.exe’s open of the Ntuser.dat file showed that Ssonsvr.exe wasn’t actually responsible for the operation, the Windows Logical Prefetcher was:
Introduced in Windows XP, the Logical Prefetcher is a kernel component that monitors the first ten seconds of a process launch, recording the directories and portions of files accessed by the process during that time to a file it stores in %SystemRoot%\Prefetch. So that multiple executables with the same name but in different directories get their own prefetch file, the Logical Prefetcher gives the file a name that’s a concatenation of the executable image name and the hash of the path in which the image is stored e.g. NOTEPAD.EXE-D8414F97.pf. You can actually see the files and directories the Logical Prefetcher saw an application reference the last time it launched by using the Sysinternals Strings utility to scan a prefetch file like this:
strings <prefetch file>
The next time the application launches, the Logical Prefetcher, executing in the context of the process’s first thread, looks for a prefetch file. If one exists, it opens each directory it lists to bring the directory’s metadata into memory if not already present. The Logical Prefetcher then maps each file listed in the prefetch file and references the portions accessed the last time the application ran so that they also get brought into memory. The Logical Prefetcher can speed up an application launch because it generates large, sequential I/Os instead of issuing small random accesses to file data as the application would typically do during startup.
The implication of the Logical Prefetcher in the profile problem only raised more questions, however. Why was it prefetching the user’s hive file in the context of Ssonsvr.exe when Ssonsvr.exe itself never accesses registry profiles? Microsoft support contacted the Logical Prefetcher’s development team for the answer. The developers first noted that the registry on Windows XP is read into memory using cached file I/O operations, which means that the Cache Manager’s read-ahead thread will proactively read portions of the hive. Since the read-ahead thread executes in the System process, and the Logical Prefetcher associates System process activity with the currently launching process, that a specific timing sequence of process launches and activity during the boot and log on could cause hive accesses to be seen by the Logical Prefetcher as being part of the Ssonsvr.exe launch. If the order was slightly different the next boot and log on, Winlogon might collide with the Logical Prefetcher, as seen in the captured boot log.
The Logical Prefetcher is supposed to execute transparently to other activity on a system, but its file references can lead to sharing violations like this on Windows XP systems (on server systems the Logical Prefetcher only prefetches boot activity, and it does so synchronously before the boot process proceeds). For that reason, on Windows Vista and Windows 7 systems, the Logical Prefetcher makes use of a file system minifilter driver, Fileinfo (%SystemRoot%\System32\Drivers\Fileinfo.sys), to watch for potential sharing violation collisions and prevent them by stalling a second open operation on a file being accessed by the Logical Prefetcher until the Logical Prefetcher closes the file.
Now that the problem was understood, Microsoft and Citrix brainstormed on workarounds customers could apply while Citrix worked on an update to the ICA Client that would prevent the sharing violation. One workaround was to disable application prefetching and another was to write a logoff script that deletes the Ssonsvr.exe prefetch files. Citrix published the workarounds in this Citrix Knowledge Base article and Microsoft in this Microsoft Knowledge Base article. The update to the ICA Client, which was made available a few days later, changed the network provider DLL to 10 seconds after Ssonsvr.exe launches before returning control to Mpnotify.exe. Because Winlogon waits for Mpnotify to exit before logging on a user, the Logical Prefetcher won’t associate Winlogon’s accesses of the user’s hive with Ssonsvr.exe’s startup.
As I said in the introduction, I find this case particularly interesting because it demonstrates a little known Process Monitor feature, boot logging, and the power of stack traces for root cause analysis, two key tools for everyone’s troubleshooting arsenal. It also shows how successful troubleshooting sometimes means coming up with a workaround when there’s no fix or you must wait until a vendor provides one. Another case successfully closed with Process Monitor! Please keep sending me screen shots and log files of the cases you solve.
Comments
Anonymous
January 01, 2003
@stefang >This is exactly the problem with the windows file sharing model: In an ideal world it should be possible for the prefethcer to open a file for reading in a way that never interferes with other processes. Today this is impossible because winlogon opens the file in a way that disallows any file sharing. I think you're missing the point. It's up to the process that opens the file to decide what kinds of sharing it allows. If a process wants to allow other processes to read from a file it's got opened, it can do so. Presumably it will prevent concurrent access for a non-arbitrary reason. Winlogon choses to not allow other processes to read the raw contents of a hive that's loaded. It's taking advantage of the power of the sharing model to enforce it's wish. If a process wants to read the raw contents of a hive it can save a copy with RegSaveKey or create a volume snapshot, which allows full access to the hive file with consistent contents for the snapshot's point in time.Anonymous
January 01, 2003
@Robert It looks like you missed this important aspect of the case: When a process opens a file, it specifies what kinds of sharing it allows for the file. If it is writing to the file it may allow other processes to read from the file, for example, but not to also write to the file.Anonymous
January 01, 2003
@Robert That's my point: Windows sharing semantics do allow a process to specify that full sharing is allowed when they open a file for reading. The prefetcher specifies full sharing, but Winlogon doesn't, so both can't have the file open at the same time.Anonymous
August 11, 2009
Mark, a small typo in this excellent article - "could cause hive accesses to been by the Logical Prefetcher as being part". Been -> be seen Interesting investigation, thanks :)Anonymous
August 11, 2009
The comment has been removedAnonymous
August 11, 2009
> Microsoft and Citrix brainstormed on workarounds customers could apply while Citrix worked on an update to the ICA Client that would prevent the sharing violation. What I don't understand is why Citrix should solve a problem which is obviously created by Microsoft Windows? This is MS team who should introduce the patch, not Citrix.Anonymous
August 11, 2009
Hi,Mark, It's intersting. And I always use Process Monitor and Process Explorer to slove my problem. Those sysinternals tools make my life easy. Thank you very much!Anonymous
August 11, 2009
Great article, and it is also one of the most detailed descriptions of the "prefetch" feature I've seen so far.Anonymous
August 11, 2009
Mark, Very interesting article, thank you! I actually had this error message a little while ago too but it turned out to be something not related to the Citrix ICA software at all. I never did figure out what the problem was because at the time I had never heard about Process Monitor, but this information might help me troubleshoot it better in the future. Thanks! DavidAnonymous
August 11, 2009
The comment has been removedAnonymous
August 11, 2009
I have occasionally run into this very issue. Good to know the reason!Anonymous
August 11, 2009
I agree with Alexei; this is a Microsoft problem. And I don't see how this is specific to Citrix at all; this issue could have shown up in any application.Anonymous
August 11, 2009
The comment has been removedAnonymous
August 11, 2009
On Windows Vista some issue with Windows Media Player sharing service. If it loads and opens user profile before system :).Anonymous
August 11, 2009
“The developers first noted that the registry on Windows XP is read into memory using cached file I/O operations, which means that the Cache Manager’s read-ahead thread will proactively read portions of the hive proactively. Since the read-ahead thread executes in the System process, and the Logical Prefetcher associates System process activity with the currently launching process” Excuse my ability of understanding. I'm still having trouble understand the root cause of the problem. The above sentence to be specific. So the cache mgr will read the ntuser.dat when the system boots, and Logical Prefetcher will record cache mgr's access pattern, but why it has anything to do with Ssonsvr.exe shouldn't it be running in the context of the System process? Thanks,Anonymous
August 12, 2009
@liys: the Prefetcher associates the activities of the System process with the user process that's currently launching. It does this because much activity is indirectly done by the system on behalf of the process, especially during process startup -- capturing this activity makes for better prefetching. Keeping this activity separate only makes sense at boot time, when the System process is the only thing running (this is not literally true, by the way, but a good enough approximation). The fact that Prefetcher can't distinguish between System process activity on behalf of the process being prefetched and system activity that's unrelated is what causes the problem. Simply not recording System process activity at all would make prefetching much less effective.Anonymous
August 12, 2009
The discussion above makes an interesting point: Citrix is a responsible company that cares about its customers. Whoever was at fault, they put in the workaround so their customers won't run into the problem. I've seen plenty of companies that tracked an issue outside of their code and then said, "Nyah nyah, it's their fault, don't try to get us to do anything." Gets even worse in the case of conflicting interpretations of a spec. "No, we're right and they're wrong." It's also pretty common in the open-source community. The calling app considers the problem to be in the dependency, while the dependency thinks that it's a corner case that's not worth the time to investigate. Meanwhile, you just want the problem to be fixed.Anonymous
August 12, 2009
Nice write up. Our company ran into this issue a few months back. At that time, I captured the same Userenv.log error you have posted. That info helped isolate the problem with the Citrix client. Our company is on a older version 9.2 of the ICA client. Our user base is over 100K. All the machines work off a common XP build with same version of Citrix. The problem was only occuring with a single business unit. This was the part that has us baffled. Do you have any details on what could spur the problem for some users and not others with same desktop build? Thanks.Anonymous
August 12, 2009
Maybe that's behind the 10 second all-idle delay I experience when I boot my Lenovo 3000 n100. Proactive prefetch prevention. tOMAnonymous
August 12, 2009
The comment has been removedAnonymous
August 13, 2009
I always use Process Monitor and Process Explorer,good!thank you!Anonymous
August 13, 2009
What is the command to get process monitor to run as session 0 using psexec?Anonymous
August 13, 2009
I read and appreciate every one of your "The Case of..." articles. I'm slowly learning how to make better use of the Sysinternals tools and learning the deeper workings of Windows. Thank you for taking the time to create/update the tools and explaining how they work in real life situations.Anonymous
August 13, 2009
Thank you for sharing this exciting issue. I know a lot of people around me are aware of boot logging feature. But the other method of using PsExec to log the login activity is a new one. Reading that stack info is tough one because that doesn't shows any third party and one won't even dream of the prefetcher doing that.Anonymous
August 14, 2009
Excelente! Mark is my hero! Thanks for sharing!Anonymous
August 14, 2009
Great article, but noticed a small typo, "...proactively read portions of the hive proactively..."Anonymous
August 14, 2009
Thank you for the very educational article. I didn't know about the "Enable Boot Logging" feature nor the part about showing the process stack information. I found that there is still one small typo in the article: "activity during the boot and log on could cause hive accesses to seen by the Logical Prefetcher" should be: "activity during the boot and log on could cause hive accesses to be seen by the Logical Prefetcher"Anonymous
August 15, 2009
The comment has been removedAnonymous
August 16, 2009
@Mark I think file sharing is an issue. What I am thinking of is an option to open a private copy of a file for reading, without preventing other processes from opening the original file with sharing restrictions. Effectively the copy would only need to be made when another process starts writing to the file, so the prefetching mechanism would still work.Anonymous
August 17, 2009
The comment has been removedAnonymous
August 17, 2009
The comment has been removedAnonymous
August 17, 2009
@mark >It's up to the process that opens the file to decide what kinds of sharing it allows. If a process wants to allow other processes to read from a file it's got opened, it can do so. Yes, I know this. My point is that in this case everything had been much simpler if the prefetcher could have used a NOLOCK option to open a file and read from it while being fully aware that the data might be inconsistent. In this case the prefetcher did not care at all about the content of the file. But I fully understand that adding such a NOLOCK feature at this point in time is probably impossible - there are probably programs that open files exclusively and then writes confidential information to the files assuming that noone can read the information because the file is opened exclusively.Anonymous
August 17, 2009
Interesting. Precisely I faced today several profile related errors when trying to coarce XP to use an existent folder to store the profile. It was quite easy to test by deleting the three ntuser files and then logging in to have that user HKCU recreated. ntuser.dat and friend DO get created, but somehow the user wasn't allowed to write in the resulting hive. The registry permissions, instead of containing an entry for the user, had an entry for CREATOR OWNER, and the user wasn't able to write anything there (of course, the accounts weren't Administrators).Anonymous
August 21, 2009
@stefang - Code reading from a file can tell Windows NOT to lock it at all, i.e. let other processes read from, write to, and even delete the file at will. That seems very much like a NOLOCK to me.Anonymous
August 21, 2009
Hey:) i have been observing the forum lots of times - Thought I would say how much i enjoy visiting.Anonymous
August 24, 2009
Mr Russinovich, If everyone would give you a cent every time they used ProcessExplorer... I get this message (or a similar one, didnt pay attention) sometimes when I start a PC but log on by using Remote Desktop Connection from another PC. Never bothered to investigate, though, just restart, log on again and Windows loads my profile with my customized desktop and all.Anonymous
August 24, 2009
@Paul No, the difference is that with the current windows sharing semantics, one program can prevent any other programs from accessing a file just by opening the file in excusive mode - denying all other processes the possibility to open the file even for reading. If program A has a file opened exclusively, it is impossible for program B to open the file - it does not matter what sharing options program B specifies. Even worse, if program B has the file open, program A will be unable to open the file because it requires exclusive access. So it is currently not possible for a windows program to open a file in a way that is fully transparent to other programs. With my suggested NOLOCK option, program B would be able to specify that it wanted to open the file even if other programs had the file open for exclusive access.Anonymous
August 26, 2009
I'm facing this issue at the moment but I'm not using citrix - just rdp to a Windows2003 terminal server. I strongly suspect it's the Symantec Antivirus 10 client that is doing this due to the messages that uhpclean fires up. I've upgraded to v11 of Symantec to see if this fixes it - if not, then I may be able to look at this information to try and get an idea of what is going on but I'm not sure how to fix it!Anonymous
August 26, 2009
Oh - I meant to say that adding that user environment debug log didn't work for me.Anonymous
August 26, 2009
Hey, I'm a programmer from way way back. HP1000 systems and HPs RTE OS. That ages me pretty good. Anyway, to get around all this file locking nonsense, back than we also had a file system implementation similar to Windows, we just located the file by reading the dirctory and accessed the data by reading the raw disc sectors through a supported OS EXEC call. Thus avoiding the file system all together to get at what was needed around about ways. Yhis must be possible in Windows as well. Rhus this NOLOCK issue can be solved with a little finguer work. Pardon a comment from a retired old timer.Anonymous
August 27, 2009
The comment has been removedAnonymous
August 27, 2009
@Andy Helsby: of course, the amount of space consumed by boot logging depends on system activity, and duration of capture. I wonder if scheduling procmon to run with a scheduled task at some point may be an option - you could set the filter as desired, choose the option to Drop Filtered Events, and perhaps log to a backing file on a different drive... Pop into the Process Monitor forum at http://forum.sysinternals.com/forum_topics.asp?FID=19 for specific questions, etc.Anonymous
August 27, 2009
Thanks Molotov - after 1hr20minutes of purely watching for activity on a specific users ntuser.dat the server crashed and rebooted :-( I'll drop into the forum when i have some more info - thanks for the help and pointers.Anonymous
August 28, 2009
Hullo i've been visiting the website for awhile Finally needed to say how much i treasure this place:)Anonymous
August 28, 2009
Its a blog, not a book, stop picking on typos people.Anonymous
September 01, 2009
I have the same issue and I think it it Symantec that causing it. Similar to Andy. I reached out the Symantec and they don't have any idea. I don't have version 11 to upgrade and test. Workaround for me is to install UPHClean-Setup.msiAnonymous
September 06, 2009
I've seen the same: unable to mount user hive => temporary profile => user very confused On four machines now. I also used boot logging to track it down. But I didn't look at the call stacks. In my cases it was Live Mesh and uninstalling it fixed it. Perhaps it was also the prefetcher though I believe two of the machines were running Vista, one Server 2008, one XP, and the article says this work better in Vista..Anonymous
September 10, 2009
At my college we have a lab full of WinXP. We could never access our profiles, always getting the temps. Admins just shrugged. We just figured profile support was really bad under WinXP. This for abour 3 years and ongoing.Anonymous
September 11, 2009
This kind of "error" had happened to me after I have installed and uninstalled my Kaspersky IS 2009 for many times.Anonymous
September 14, 2009
A lot of these issues stem from the fact that we've lost the plot with desktop PC's, in that we've forgotten what the P stands for -and that is IS a P, and not M for mainframe.Anonymous
September 14, 2009
It does look like winlogon is saying "something else (prefetch) has the file open, so I can't get exclusive access to it ... fatal error". I suppose this wouldn't happen if prefetch used something like VSS to access the data, so the file doesn't appear to be in use at all to regular processess. I'm surprised that prefetch is trying to read ntuser.dat at all. You'd think ntuser.dat (and possibly other files involved in authentication and policy enforcement, or which are data files that might change regularly) would need to be permanently exempted from prefetch.Anonymous
September 15, 2009
Like several people that have posted here I want to know why Microsoft did not come up with a prefetching fix that prevent this type of sharing violation in XP? In this article Mark does a great job of explaining what's going on wtih Citrix and how their company developed a fix for their client however what about all the other applications that may have this problem on XP? I work for a company that has 1000's of computers and we support about 2500 applications, migrating to a later OS is not an easy option and can take a over year to do so. We see this problem on a daily basis however it is very difficult to predict when and what computer it will occur so setting up the procmon to capture the event has proven very difficult. Setting up procmon after it has happened will not work because the computer requires a reboot for boot logging to begin and rebooting casues the problem to go away. Unless someone knows how to force the procmon to begin boot logging by only logging out and logging back on?Anonymous
September 15, 2009
I have the same issue and I think it it Symantec that causing it. Similar to Andy. I reached out the Symantec and they don't have any idea. I don't have version 11 to upgrade and test. Workaround for me is to install UPHClean-Setup.msi This is not working for me. Any more ideas? Thanks a lot.Anonymous
September 17, 2009
Thanx Mark for sharing this with us.Anonymous
September 17, 2009
The comment has been removedAnonymous
September 17, 2009
The comment has been removedAnonymous
September 30, 2009
The comment has been removedAnonymous
October 02, 2009
This issue also occurred on one of our machines with GoogleUpdater enabled. Google's updating process is especially insidious as in order to fully disable it, one must disable services, delete registry entries and disable or delete scheduled tasks. Plus it contributes to this Temp Registry Profile problem! Garbageware.Anonymous
October 03, 2009
The comment has been removedAnonymous
October 03, 2009
@Loni Hamilton "Get help from Microsoft Get online support (or toll-free telephone support in the U.S. and Canada) for security-related issues such as viruses and security updates." http://www.microsoft.com/athome/security/protect/support.mspxAnonymous
October 27, 2009
I have this problem too at my computer at home. If my wife has been logged on to her account and I log on to mine this happens ~50% of the time. ASFAIK we don't have any Citrix stuff installed so there's no fix for us. It's a bit weak by MS to not solve it properly themselves, since it's obviously a bug in how the cache manager interacts with the rest of the system at logon. At least now I know how to find out what application the prefetcher will think was associated with the registry read so I could write a script tot delete those pf-files at logoff.Anonymous
November 04, 2009
Several comments suggested a flaw in the file system regarding access sharing and file locks and targeted the Logical Prefetcher (LP) as the problem. However, these seem to miss the point, as the LP already utilizes read-only access and specifies full sharing. The problem in this case really lies with Winlogon because it requires exclusive access. The article does identify a weakness of the LP in that 1) it cannot distinguish between simultaneous System processes that are non-related (such as the cached IO file operations) from those initiated by the launching process and 2) future LP activity can initiate unnecessary reads, specifically those from the previous unrelated System processes, which could cause collisions with Winlogon. The LP has been modified in Vista and Windows 7 to work around this issue as it pertains to the LP. I wonder if the LP can be reengineered to only associate the simultaneous System processes that are actually initiated or indeed related to a launching process and also if Winlogon should be modified in a way to play more nicely? In the meantime, using the tools and debugging techniques outlined can help identify troublesome startup processes and a log-off script deleting the offending prefetch files can create a work around. This is a very interesting and informative article, none the less.Anonymous
November 12, 2009
We encounterd a similiar problem with our Antivirus. The Realtime Scanner accesses all ntuser.dat when the computer starts. When the user logs on quickly, nothing is reported. When the user logs on after some time, there is a sharing violation from Rtvscan.exe on the users ntuser.dat. When the user logs on exactly when Rtvscan access his ntuser.dat, the Temporary Registry Profile problem occurs. I sent procmon.log to the MS Engineers, but in my opinion they where not able to interpret the log file...they should be more engineers like Mark understanding the Windows logon process...Anonymous
November 28, 2009
Yes, yes. The google Updater is the cause. I have this problem with Windows 7. when uninstalling Google updater I could go to a "termporary profile" normally in real time. Thanks. Mark superhero.Anonymous
January 16, 2010
I can't believe no one has mentioned this yet... Was the official solution (or workaround) to this problem in the new client really to just sit there delaying the user's boot for 10 seconds while nothing happens? As someone who was forced for several years to use a networked Windows system that had hideously slow logins (we're talking several minutes minimum and up to 10-15 minutes and sometimes more during peak times), I shudder to think that software may be deliberately delaying this to an even further extent.Anonymous
January 16, 2010
Or did I read it wrong and it's the program in the new thread which waits 10 seconds? Still seems a bit of a kludge because on systems where the login has different timing, this could cause services provided by the app to be unavailable for a few seconds after login apears to have finished. Fine for a human who can't react that fast, but I wonder how long it'll take for a company to file a bug along the lines of "Our script which does X and Y after [or during] boot using operations enabled by your software no longer works on 30% of our computers."Anonymous
January 18, 2010
The comment has been removedAnonymous
January 29, 2010
The comment has been removedAnonymous
February 25, 2010
The comment has been removedAnonymous
April 27, 2010
Interesting artical and thanks for sharing!