Take Control Over AD Permissions and the AD ACL Scanner Tool
What is the state of your delegation?
Have you a documented and recent report over the permissions in your Active Directory?
Have you granted permissions on the relevant OU's in the past and left it like this ever since??
Maybe it’s time to take a look again to see what’s actually delegated in Active Directory?
Things you probably find when re-visiting the permissions:
- Permissions given to users or groups that does not exist anymore.
- Permissions set to high up in the OU structure so users have the possibility to create/delete/modify Active Directory objects in the wrong places.
- The permissions grant the user more than needed e.g. Helpdesk is supposed to reset passwords on user’s accounts in the defined OU but can create\delete any type of objects.
- Same set of permissions delegated to two groups. Usually only one group is needed for one set of permissions.
- Permissions granted to users or groups that is not needed anymore. This can happen when enabling a project to create objects for a limited period of time or if there were a transition between out-sourcing partners.
What to do?
Every Active Directory should have a documented delegation model that includes the permissions set for the data in Active Directory.
I'm not saying you should type down every single permission on every object, but the permissions that is needed for you organization to be able to perform their given tasks.
Here's a simple example of how you could document Helpdesk's permissions in AD:
| Group | Permissions | OU |
| Helpdesk | Reset Passwords | OU=Users,OU=Corp,DC=Contoso,DC=Com |
| Helpdesk | Create/Modify Groups | OU=Groups,OU=Corp,DC=Contoso,DC=Com |
To verify that the permissions in Active Directory is reflecting the need of you organization you have to go through every OU in your Active Directory where permissions is modified.
It's usually a quite daunting task to click your way through the directory tree to get control over the permissions. For every OU or any object for that matter there are at least 4 clicks to reach the Advanced Security Settings tab, which is often the required view, and if you got a large OU structure that could take a while.
To simplify the work of creating and documenting the delegation model in Active Directory I have written a tool in PowerShell with a GUI.
This tool creates reports of the access control list for all of your Active Directory objects. With these reports you can see what/where and when permissions have been set.
To run the script you need at least PowerShell 2.0 and Windows 7/Windows Server 2008, (Windows Server 2003 with Limited functionality).
Enabled unsigned scripting:
Set-ExecutionPolicy Unrestricted
If you are not local admin and cannot set it on your machine you can set it for your profile:
Set-ExecutionPolicy Unrestricted -Scope CurrentUser
You do not need Powershell Module for Active Directory.
To create a report for an OU.
- Click Connect and the tool will connect to your domain.
- The Domain Node will be populated in the large tree view box below and you can click your way to the OU.
- When the OU is selected click Run Scan and you will get a HTML report of the permissions.
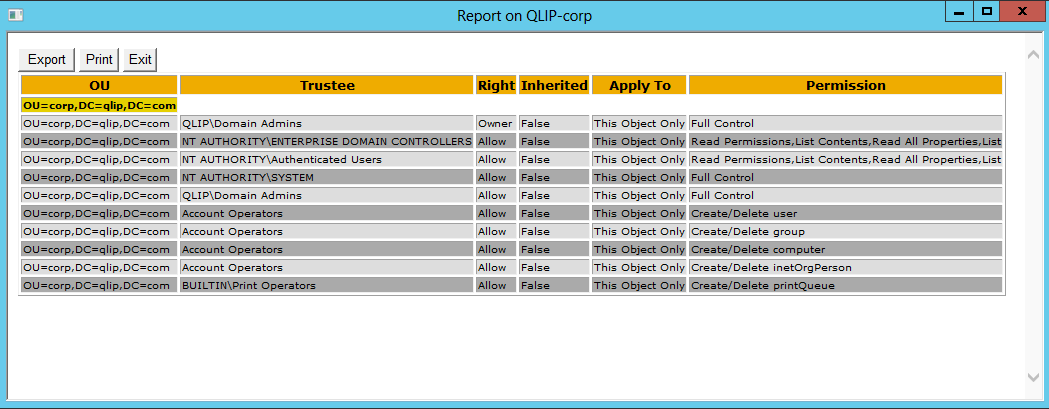
This is an example of a report:
By default you will only get the selected OU, but if you like to list all sub OU's you can clear the One Level check box. Be aware that it can take a long time to though a large OU structure.
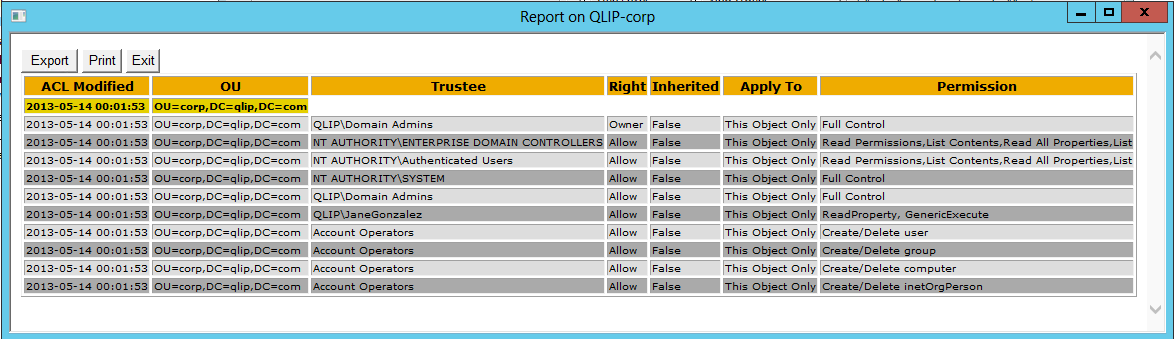
To get the date when the permissions where modified check the Replication Metadata check box. This will add a column to the report with the latest change of the permissions on each object in the report.
This is an example of a report with the date when the access control list was modified.
To browse all objects, click All Objects in the Browse Options box. This is necessary when you would like to get the permissions on another object like a user for example. Then you also have to select All Objects in the Report Objects box too.
If you like to create a report of the whole domain I strongly suggest you select CSV file in the Output Options since it will take a long time to go through all OUs and create a HTML table for it. If you select CSV file it will be much faster and you can convert it to a HTML report afterwards in the Additional Options. You can even use it for comparison.
The Power of AD ACL Scanner
- Comparing
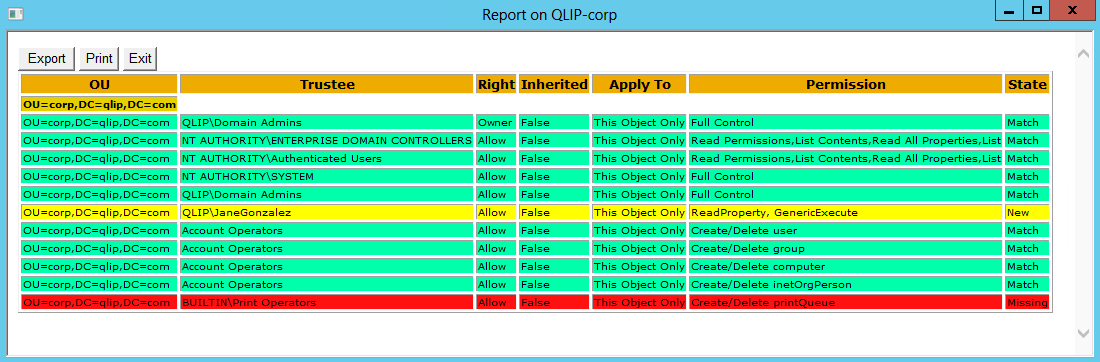
The cool thing with AD ACL Scanner is that you can compare the current state with a previous result. If you select to create a CSV file of the report you can use that to compare the current state with this file and you will get a report of what is missing or what is added.
This is an example of a comparison report:
- Filtering
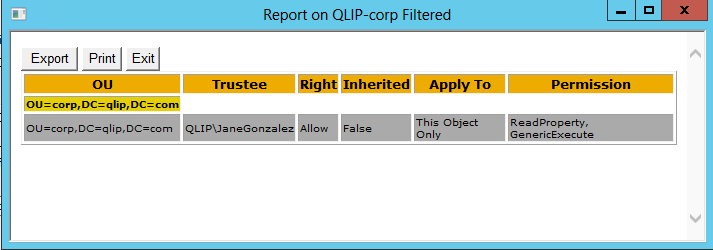
Another nice feature is the filtering feature.
- You can filter on Allow or Deny permissions.
- You can filter on object types, like user or computer.
- You can filter on Trustee, this is a free text field where you can type any kind of name you are looking for. For example: QLIP\JaneGonzalez.
Here's an example of a report with filtering:
Go ahead and download AD ACL Scanner script from Codeplex: https://github.com/canix1/ADACLScanner
Go ahead and explore permissions in AD!
I encourage you to get to know your permissions in AD and starts to document it.
Comments
Anonymous
January 01, 2003
tack så mycketAnonymous
January 01, 2003
WOW, great PS Tool. Thank you so much Robin. RegardsAnonymous
January 01, 2003
Hi Vince, Thanks a lot!Anonymous
January 01, 2003
Hi IanC, Under "Select naming context" select Custom and type the naming context or domain name of your domain in the Naming context field. Then press connect. This requires an incoming trust since you cannot type your credentials anywhere. RobinAnonymous
January 01, 2003
Hi Andy, You need to have at least PowerShell 2.0. Start PowerShell Type $PSVersionTable and press Enter, that will give you the PSVersion. To run scripts you need to modify the ExecutionPolicy: Set-ExecutionPolicy Unrestricted If you are not local admin and cannot set it on your machine you can set it for your profile: Set-ExecutionPolicy Unrestricted -Scope CurrentUser Then run this command in the same folder as the script. .ADACLScan1.2.ps1 /RobinAnonymous
January 01, 2003
Very Nice Robin ! ThanksAnonymous
January 01, 2003
thank youAnonymous
January 01, 2003
AwesomeAnonymous
January 01, 2003
Thank you, this looks like a good AD tool. Have run to look at permissions on 4 OU's, when run on our student OU errors were displayed in the console windowAnonymous
May 14, 2013
ThanksAnonymous
May 27, 2013
Uhm how to start the GUI ? Thx !Anonymous
May 27, 2013
Thanks, Robin for you quick response ! Works fine !!Anonymous
May 30, 2013
Hi Robin, Another great achievement. Amazing stuff :-)Anonymous
September 23, 2013
Hi Robin, is it possible to connect to a remote domain. I am trying but it keeps defaulting back to the domain I am in? CheersAnonymous
October 23, 2013
Hi Robin, Really nice tool...thanks for sharing it with all AD community.Anonymous
December 04, 2013
Hi Robin, I just downloaded your tool and trying to run from my PS version 3.0 but the problem is that when I select "Run Scan" the results opens up in notepad and is blank. I have confirmed the executionpolicy is set to "unrestricted". Only thing I've noticed is that when I run the tool in PS console, I get the option to [D] Do not run [R] Run once [S] Suspend so I selected [R] which is my only obvious option. Can you help?Anonymous
December 04, 2013
Hi H Kang, Do you get any errors in the PS console window? If you have selected HTML report as output the tool will create a .hta file in your profile's %temp% folder. Go to %temp% and see if you have a ACLHTML.hta file and that it's associated with mshta.exe (Microsoft HTML Application host). RobinAnonymous
December 04, 2013
Robin, thank you for your prompt response. To answer your question: No errors in the PS console window. Yes, I had selected HTML report in the tool and cofirmed there is an ACLHTML.hta file created in my profile's %temp% directory. When I double clicked on this file, it opens a blank notepad file... this file is showing as "html application" in the extension column in the directory but still opens up as notepad document. so I reassociated this file to MS Word so now it opens up in MS Word document and the html content is displaying properly. Strange but now I get a readable report.Anonymous
December 09, 2013
Great Tool. I've just noticed one small problem with the 1.3 version using the effective rights tab. If i search for a user, it returns all the effective permission results (in the HTML report) for that users group membership (as it should). However, the problem is it doesn't seem to return results if a user is explictly granted permissions - i.e. DOMAINAUser. Actually, in my case the subOU OUs where that permission has been granted don't show up at all in the report. All other subOU seem to be there. The colour coding works great. Report works fine filtering for user on the Filter option tab - i.e. AUser. Just using the default settings, can this be easily fixed?Anonymous
December 09, 2013
Hi Pete, I've tried to reproduce it but could not find a way. One thing you could check is that the msDS-PrincipalName (DOMAINUSERNAME) in Select Security Principal field is correct ,once you selected your user, and that it’s equal to the value in the report when you run a normal report or using filtering. When nodes or OU's for that matter does not show when using effective rights tab, there's no matching permissions. RobinAnonymous
December 12, 2013
A really Cool Tool, thangsAnonymous
September 24, 2015
The comment has been removedAnonymous
September 29, 2015
Hi Michele,
At the moment this is not possible.
/RobinAnonymous
June 09, 2016
AD ACL Scanner Tool is very helpful to me.Thankyou.....Anonymous
October 17, 2016
Hi Robin,What's the minimum permission to run this script ?or does it have to be executed under DOMAIN\Administrator account ?Thanks for the share.- Anonymous
November 04, 2016
Hi Albert,Normally authenticaticated user can read almost anything. There are scenarios where you have to elevate. For example if you have removed read access somewhere or implemented List Object mode you need to elevate.
- Anonymous
Anonymous
January 26, 2017
Hi, great tool but I have an issue running a Scan with Scan Depth of One Level or Subtree: With Base all is fine but as soon as I select one of the other 2 options I get the following error in the calling PS window and no result:ReverseDNList : Cannot bind argument to parameter 'stringlist' because it is null.At C:\temp\ADACLScan4.7.2.ps1:6460 char:26+ $nodelist = ReverseDNList <<<< $nodelist + CategoryInfo : InvalidData: (:) [ReverseDNList], ParameterBindingValidationException + FullyQualifiedErrorId : ParameterArgumentValidationErrorNullNotAllowed,ReverseDNListException calling "SendRequest" with "1" argument(s): "An operation error occurred."At C:\temp\ADACLScan4.7.2.ps1:10058 char:52+ $response = $LDAPConnection.SendRequest <<<< ($request) + CategoryInfo : NotSpecified: (:) [], MethodInvocationException + FullyQualifiedErrorId : DotNetMethodExceptionAny ideas?- Anonymous
January 28, 2017
Could you provide more info please? Does the error appear all the time and for all levels in your directory?What PowerShell version ( run $PSVersionTable) are you using?- Anonymous
January 30, 2017
CLRVersion 2.0.50727.7071BuildVersion 6.1.7601.17514PSVersion 2.0WSManStackVersion 2.0PSCompatibleVersions {1.0, 2.0}SerializationVersion 1.1.0.1PSRemotingProtocolVersion 2.1It appears on all levels and always as soon as I select as "Scan Depth" an option which goes down the structure. I'm using a standard user account but as I can list the ACL if I select the level below and use the Scan Depth=Base option I don't think that it is a rights issue. The error also happens if I select a leaf of the tree and use Scan Depth=One Level or Subtree (although there is no level below) while Base works well here. The following happens: When I click Run Scan it writes 3 lines into the Log: Scanning / No Permissions found! (in red) / Finished. No result window opens but the messages shown in my original post show up in the PS window from where I started the program with "set-executionpolicy unrestricted -scope currentuser" and "powershell -STA Documents\ADACLScan4.7.2.ps1". I was advised by PS to use -STA cause it did not run without that.Hope this helps...- Anonymous
February 14, 2017
Hi Robin, do you need more info? Would be glad if you can provide some more support on this.
- Anonymous
- Anonymous
- Anonymous
Anonymous
March 30, 2017
Life saver tool when you have to do a quick assesment or delegate this pupropse to SOC operatorsAnonymous
May 03, 2017
Looks like https://adaclscan.codeplex.com/ is no longer valid. Can someone share where I can grab a copy of this script?Anonymous
May 05, 2017
any other locations than codeplex? This one is stopping and i connot finf the tool there.Anonymous
May 10, 2017
Hi Robin, I would like to download the script by codeplex but the link dont work anymoreAnonymous
May 12, 2017
With the demise of codeplex.com, the script now appears to be located at https://github.com/canix1/ADACLScanner.Anonymous
May 15, 2017
Download link is broken right now. Any tips on where I can safely download this? I used it before and found it was really good so I would really like to get hold of it again to play with.Anonymous
May 22, 2017
I have updated the link to AD ACL Scanner, new url is https://github.com/canix1/ADACLScanner.Anonymous
June 27, 2017
The comment has been removed- Anonymous
July 05, 2017
Hi Lee,Did you specify server (-Server) and port (-Port)?
- Anonymous