Pricing: Azure Security Center is offered in two tiers: Free and Standard. The Standard tier is free for the first 60 days. Any usage beyond 60 days will be automatically charged as per the pricing scheme below. Pricing Details: https://azure.microsoft.com/en-us/pricing/details/security-center/ Benefits & Reference All About ASC, PDF: Link Benefits | Features | Understand security state across on-premises and cloud workloads Get a unified view of security across all of your on-premises and cloud workloads. Automatically discover and onboard new Azure resources, and apply security policies across your hybrid cloud workloads to ensure compliance with security standards. Collect, search, and analyze security data from a variety of sources, including firewalls and other partner solutions. Find vulnerabilities and remediate quickly Continuously monitor the security of your machines, networks, and Azure services using hundreds of built-in security assessments or create your own. Use actionable security recommendations to remediate issues before they can be exploited.
Limit your exposure to threats Enable adaptive threat protections to reduce exposure to attacks. Block malware and other unwanted code by applying application controls adapted to your specific workloads and powered by machine learning. Enable just-in-time, controlled access to management ports on Azure VMs to drastically reduce surface area exposed to brute force and other network attacks.
Detect and respond swiftly to attacks Use advanced analytics and the Microsoft Intelligent Security Graph to get an edge over evolving cyber-attacks. Leverage built-in behavioral analytics and machine learning to identify attacks and zero-day exploits. Monitor networks, machines, and cloud services for incoming attacks and post-breach activity. Streamline investigation with interactive tools and contextual threat intelligence.
| - Centralized policy management – Ensure compliance with company or regulatory security requirements by centrally managing security policies across all your hybrid cloud workloads.
- Continuous security assessment – Monitor the security posture of machines, networks, storage and data services, and applications to discover potential security issues.
- Actionable recommendations – Remediate security vulnerabilities before they can be exploited by attackers with prioritized and actionable security recommendations.
- Prioritized alerts and incidents - Focus on the most critical threats first with prioritized security alerts and incidents.
- Advanced cloud defenses – Reduce threats with just in time access to management ports and adaptive application controls running on your VMs.
- Integrated security solutions - Collect, search, and analyze security data from a variety of sources, including connected partner solutions.
| | | | Built-in intelligence and advanced analytics | 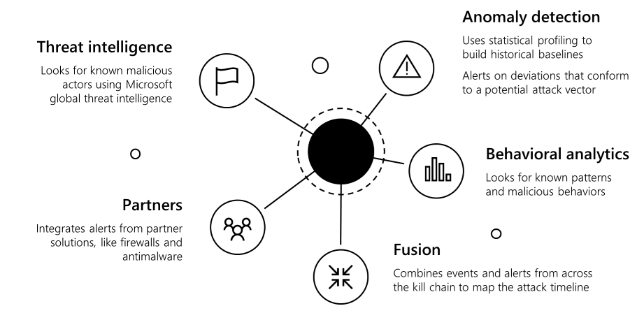
| | | Respond Quickly To Threats | Automate and orchestrate common security workflows Create playbooks with integration of Azure Logic Apps Trigger workflows from any alert to enable conditional actions | Common workflows - Route alerts to a ticketing system
- Gather additional information
- Apply additional security controls
- Ask a user to validate an action
- Block a suspicious user account
- Restrict traffic from an IP address
|
Architecture 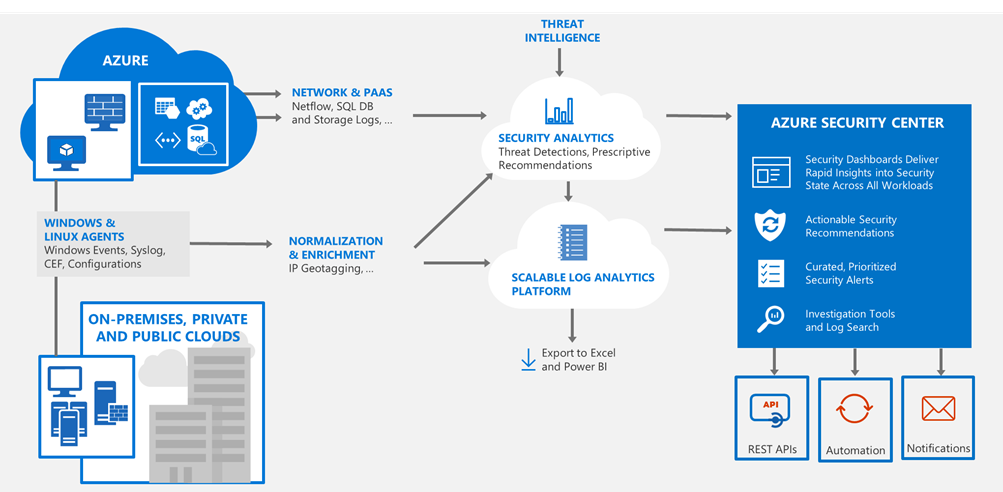
|
Features Overview |
Understand security state across hybrid workloads |
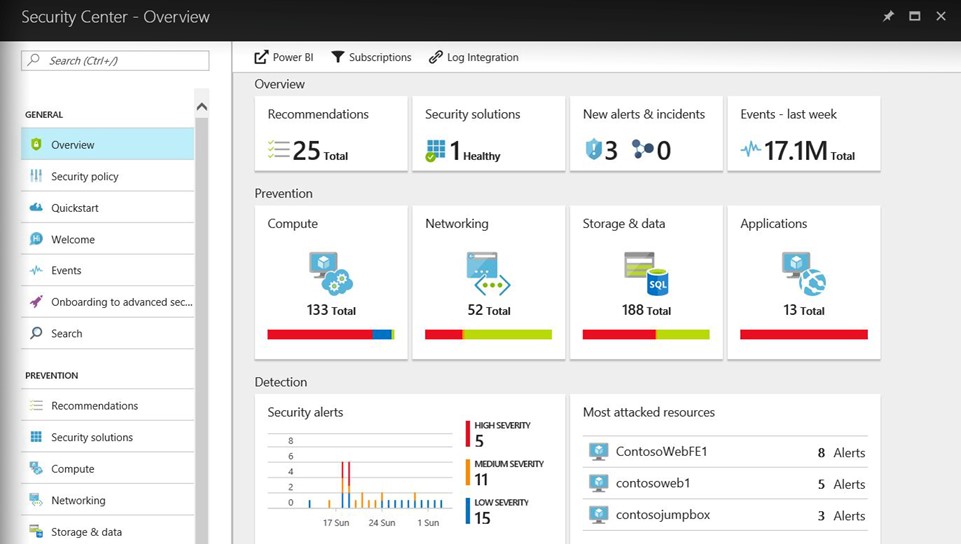
|
Built-in Azure, no setup required Automatically discover and monitor security of Azure resources Gain insights for hybrid resources Easily onboard resources running in other clouds and on-premises |
| |
Ensure compliance with policy management |
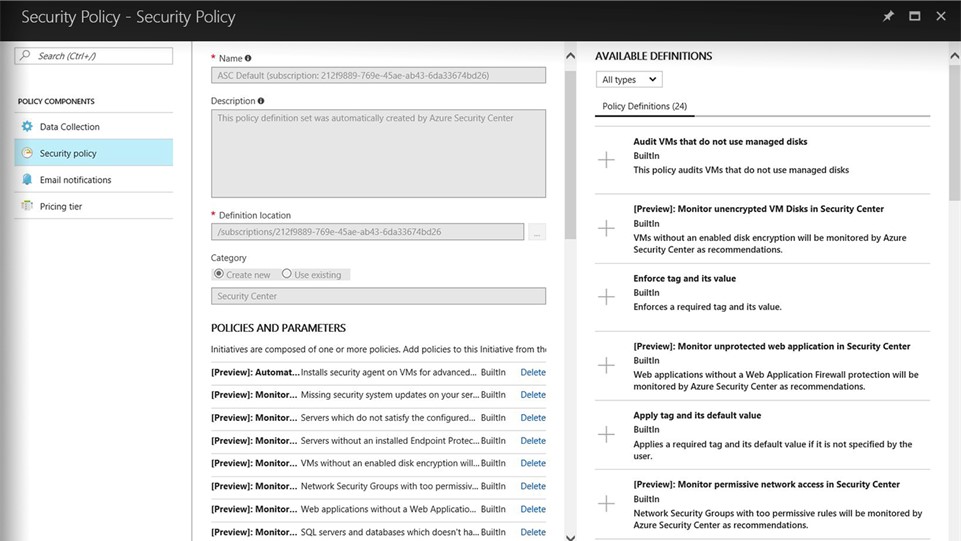
|
Central policy management Define a security policy for each subscription in Security Center Apply across multiple subscriptions using Azure Management Groups |
| |
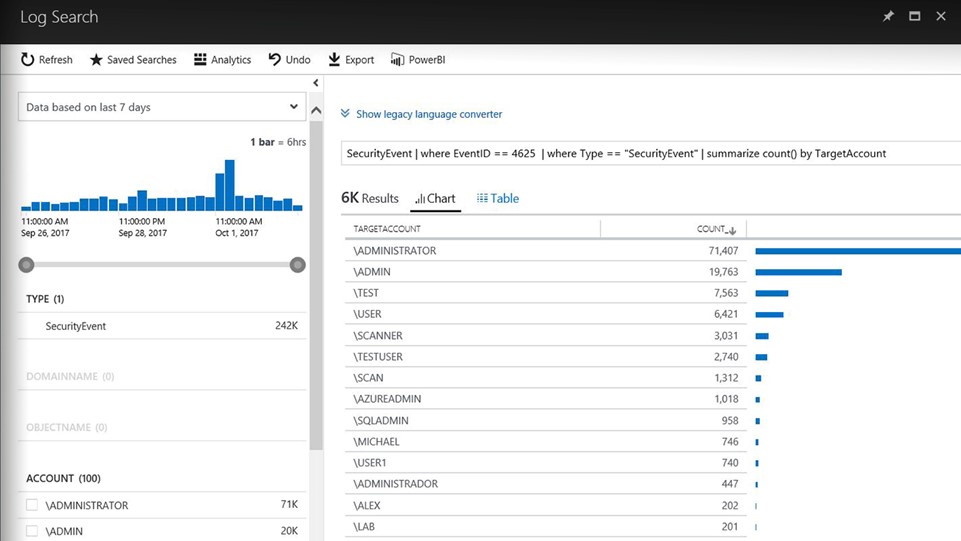
Gain deeper insights with integrated log analytics |
|
Quickly identify list of notable events that require your attention Out of the box notable events in dashboard or create custom queries Search and analyze security data using a flexible query language Use built-in or custom queries with Log Analytics search |
| |
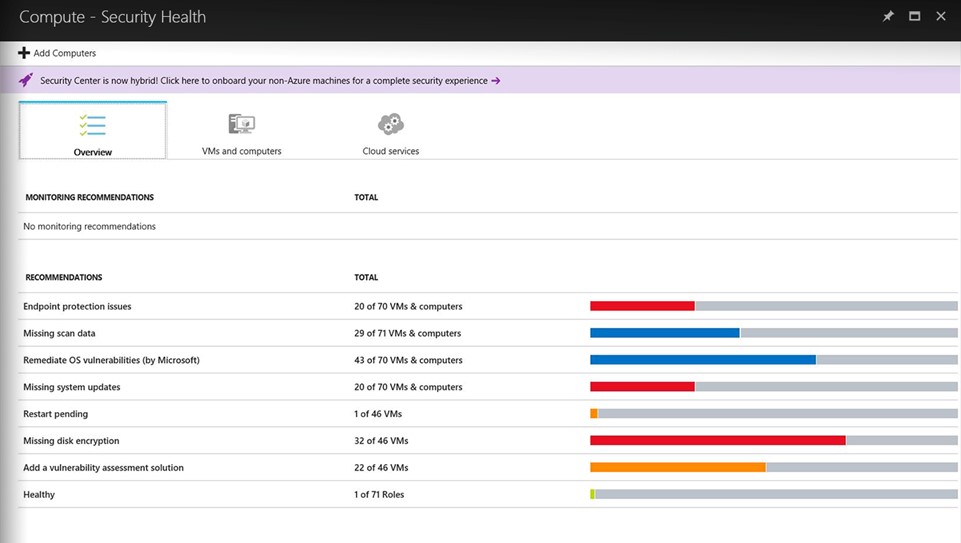
Identify and remediate vulnerabilities quickly |
|
Continuous assessment of machines, networks, and Azure services Hundreds of built-in security assessments, or create your own Fix vulnerabilities quickly Prioritized, actionable security recommendations |
| |
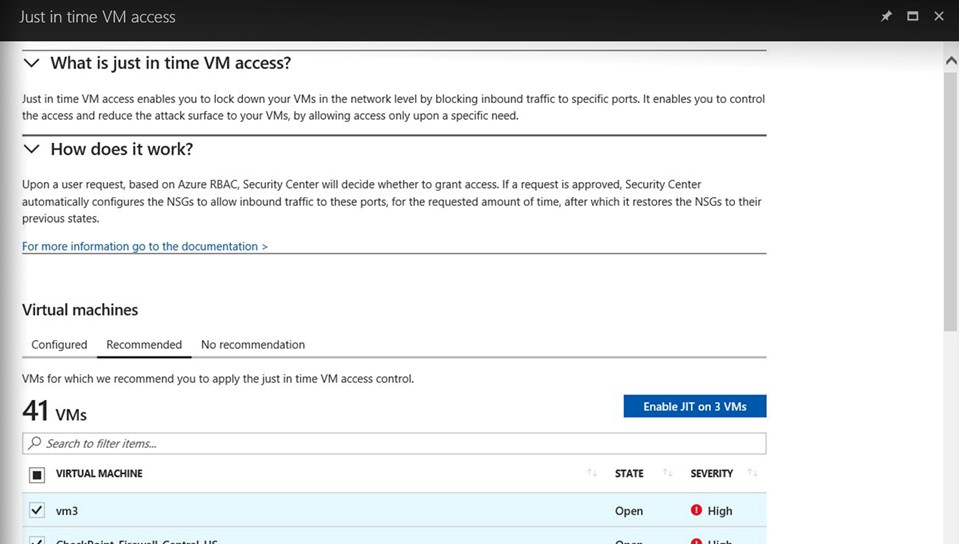
Limit exposure to brute- force attacks |
|
Lock down ports on virtual machines Enable just-in-time access to virtual machines Access automatically granted for limited time |
| |
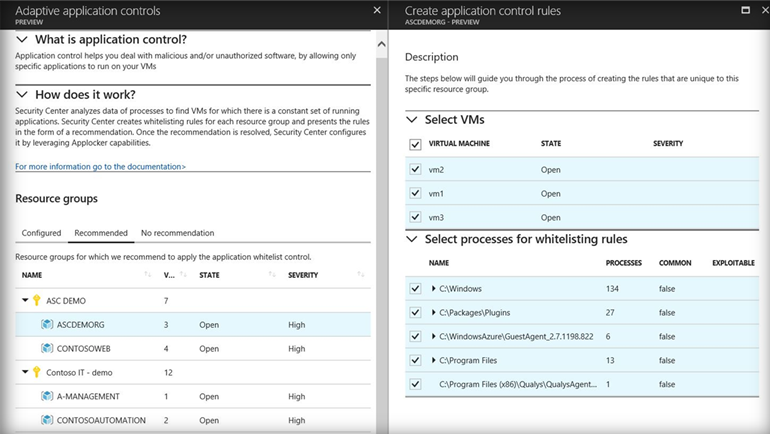
Block malware and other unwanted applications |
|
Allow safe applications only Adaptive whitelisting learns application patterns Simplified management with recommended whitelists |
| |
Focus on the most critical threats |
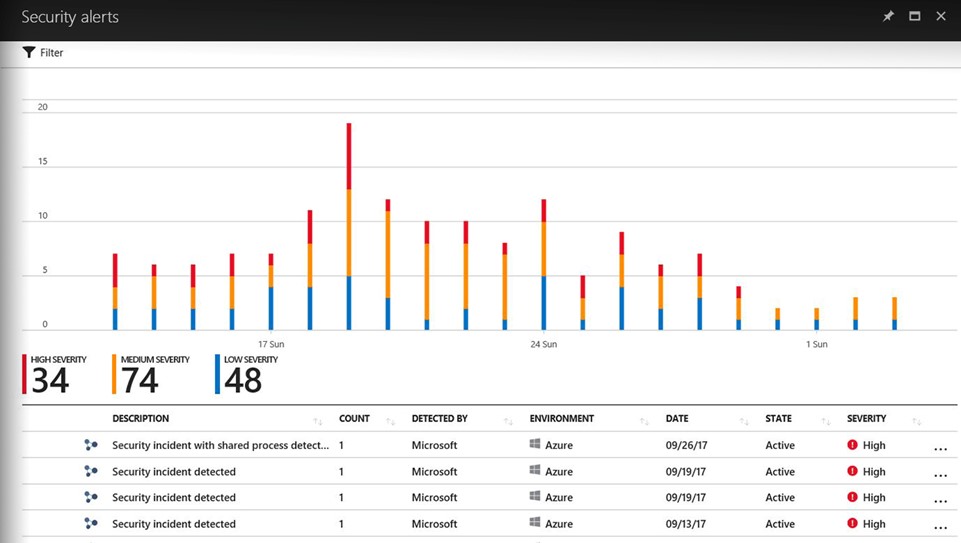
|
Get prioritized security alerts Details about detected threats and recommendations Detect threats across the kill chain Alerts that conform to kill chain patterns are fused into a single incident |
| |
Gain valuable insights about attackers |
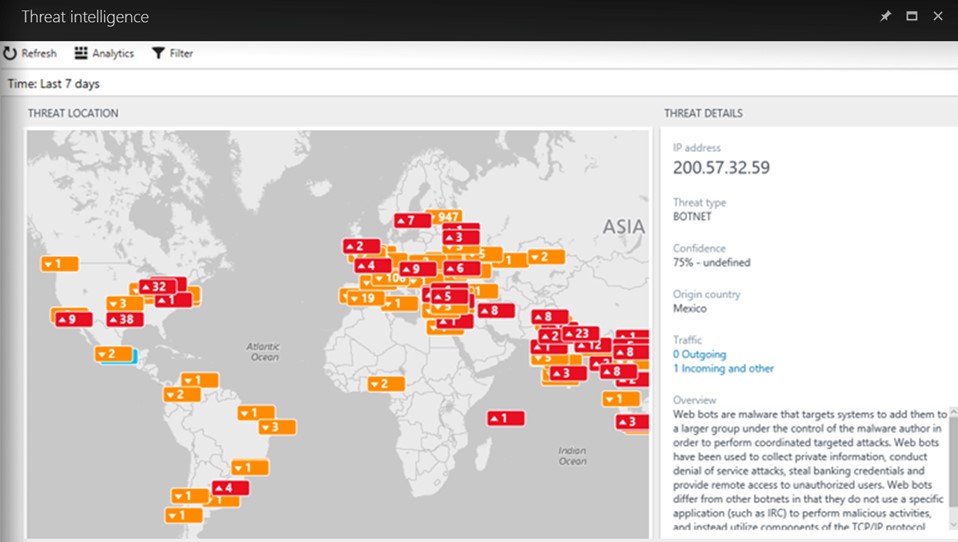
|
Visualize source of attacks with interactive map Analyzes data from your computers and firewalls logs Gain insights through threat reports Attacker's known objectives, tactics, and techniques |
| |
Simplify security operations and investigation |
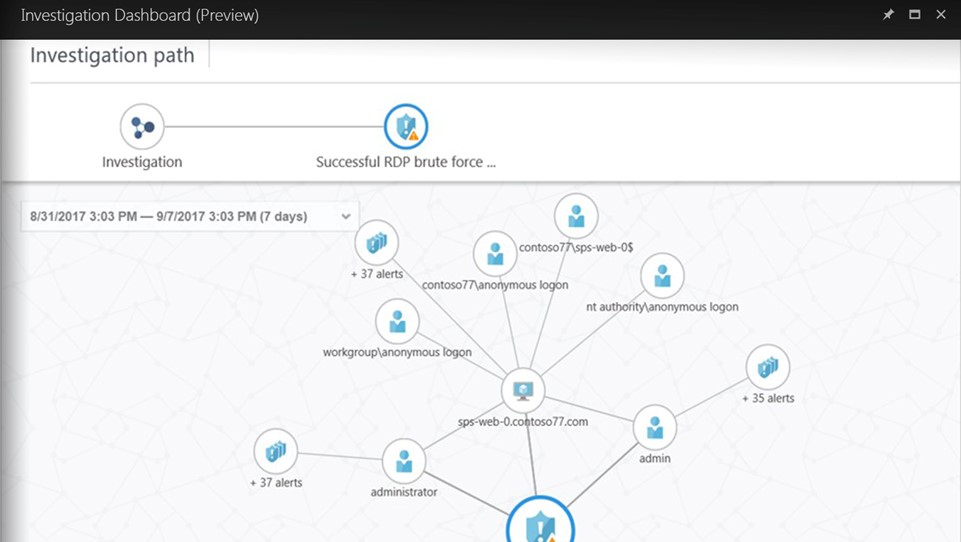
|
Quickly assess the scope and impact of an attack Interactive experience to explore links across alerts, computers and users Use predefined or ad hoc queries for deeper examination |
| |










