Multi-Factor Authentication (MFA) Setup and End-User Experience with Office 365 and PowerShell
This article is more of a follow up towards an earlier article that I had written for - Enabling/Enforcing Multifactor Authentication for All (Bulk) Users in Office 365.
That article was aimed at IT Professionals who would dive deep into the functionality and are comfortable with PowerShell. This article is aimed at end-users and IT Professionals – to get a glimpse of how would MFA (or multi-factor authentication) experience turn out to be.
Initial Setup (Direct Link to portal: https://account.activedirectory.windowsazure.com/UserManagement/MultifactorVerification.aspx)
Notes: Azure multi-factor authentication is a method of verifying who you are that requires the use of more than just a username and password. Using MFA for Office 365, users are required to acknowledge a phone call, text message, or app notification on their smart phones after correctly entering their passwords. They can sign in only after this second authentication factor has been satisfied.
A form of multi-factor authentication is included with Office 365, but you can also purchase Azure multi-factor authentication that includes extended functionality. For more information, see feature comparison of Azure multi-factor authentication versions.
(Reference article for IT Pros: https://support.office.com/en-us/article/Set-up-multi-factor-authentication-for-Office-365-users-8f0454b2-f51a-4d9c-bcde-2c48e41621c6?ui=en-US&rs=en-US&ad=US)
Set up multi-factor authentication in the Office 365 admin center
Important: All the Office 2016 client applications support multi-factor authentication through the use of the Active Directory Authentication Library (ADAL). This means that app passwords are not required for Office 2016 clients.
- Go to the Office 365 admin center.
- Navigate to Users > Active users. Your screen should look like one of the following:
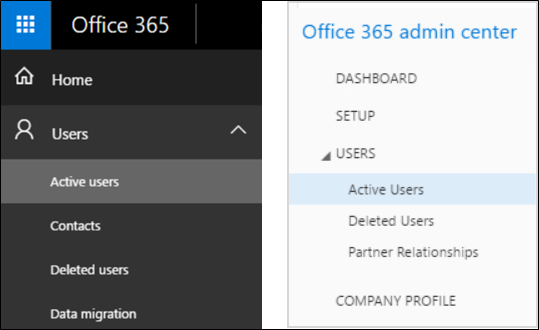
In the Office 365 admin center, click More > Setup azure multi-factor auth.
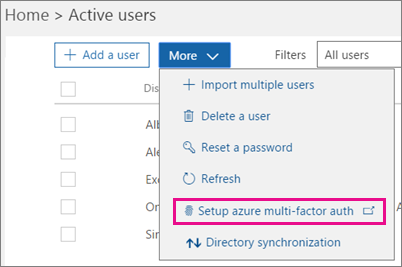
Here is the direct link to the MFA management portal for Office 365:
https://account.activedirectory.windowsazure.com/UserManagement/MultifactorVerification.aspx
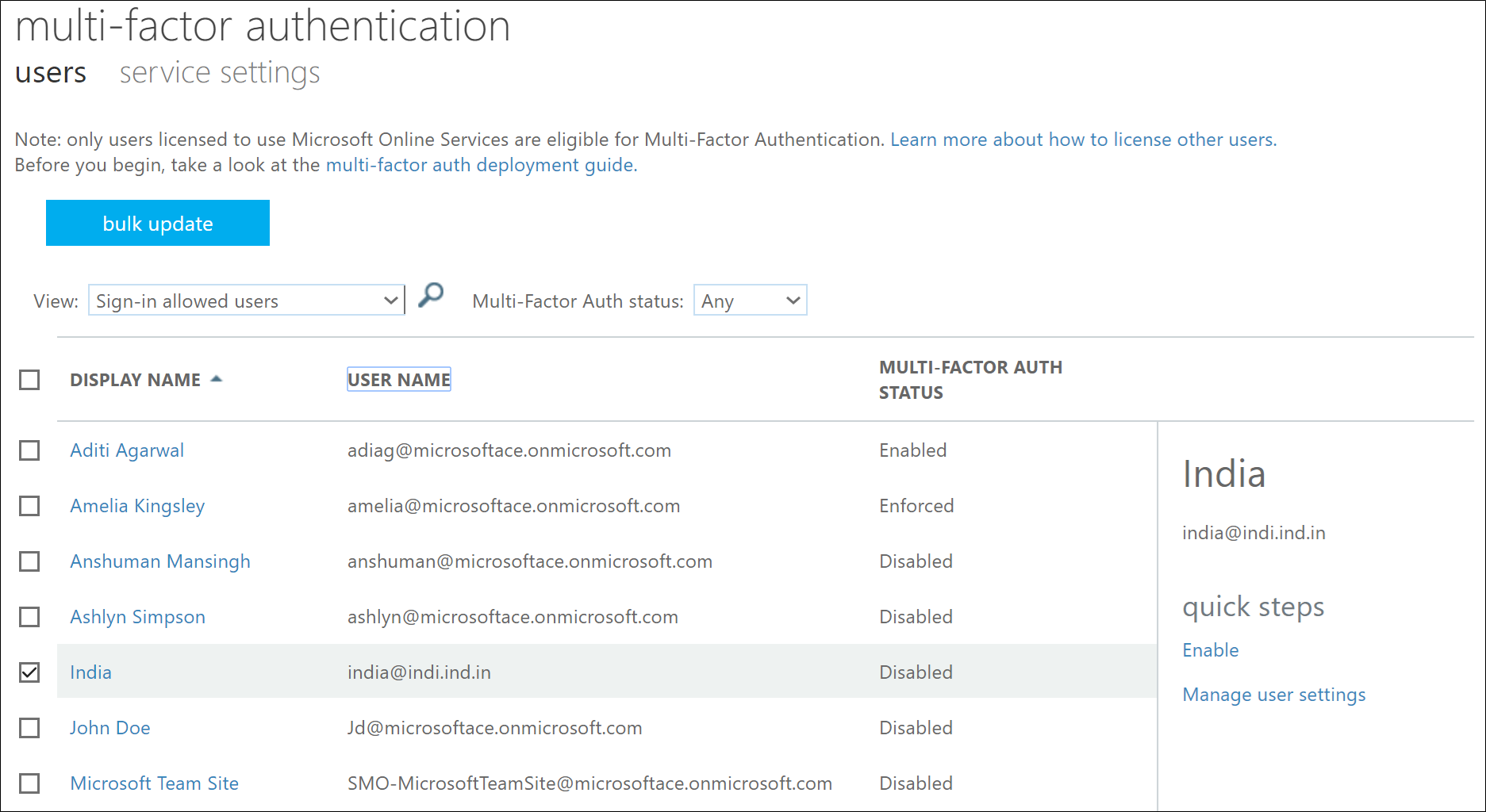
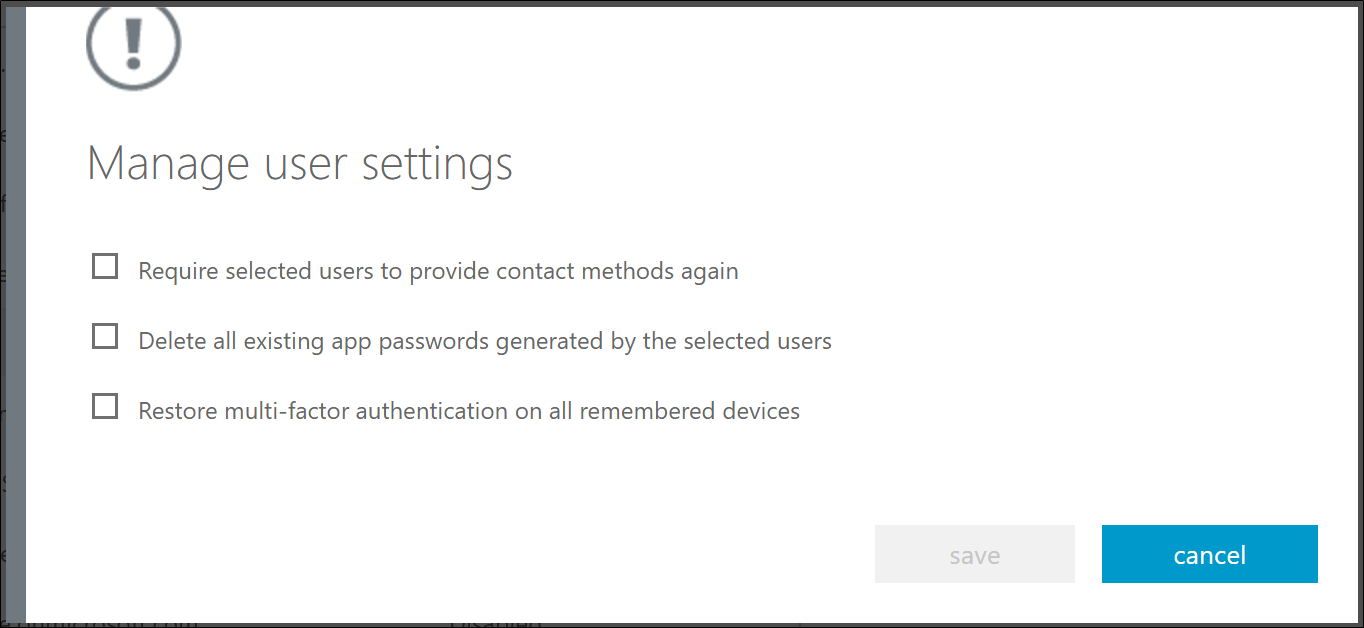
To reset selected users' MFA information.
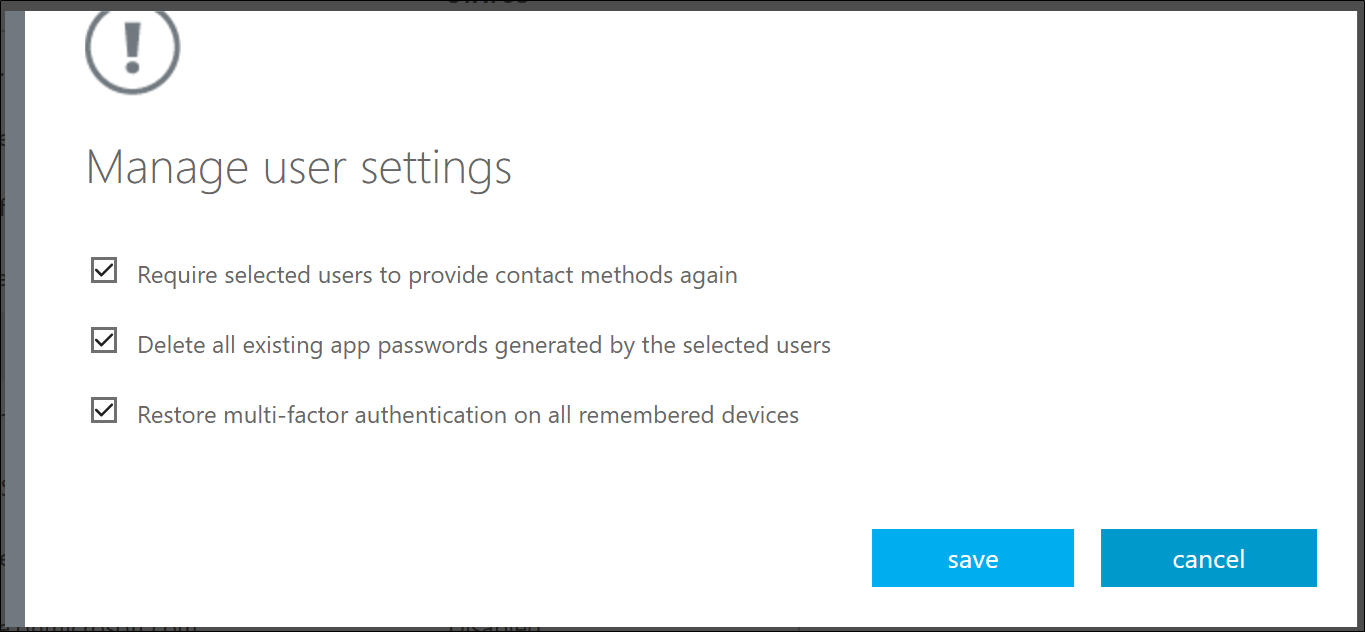
When you hit enable
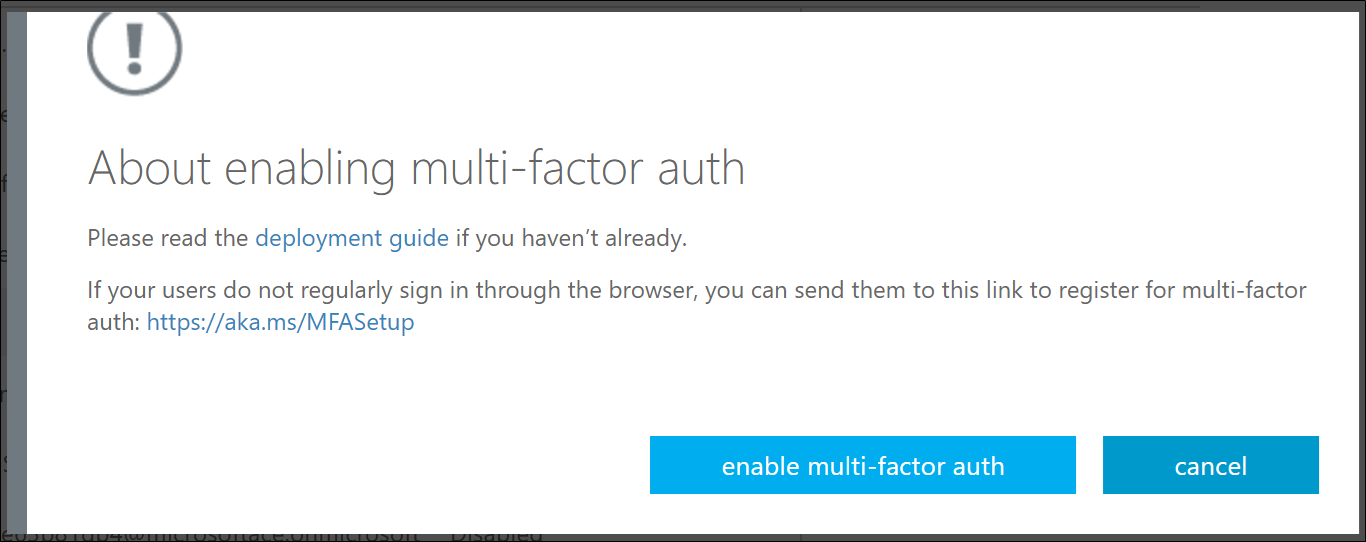
For Reference: About enabling multi-factor authentication
Please read the deployment guide if you haven't already. If your users do not regularly sign in through the browser, you can send them to this link to register for multi-factor auth: https://aka.ms/MFASetup
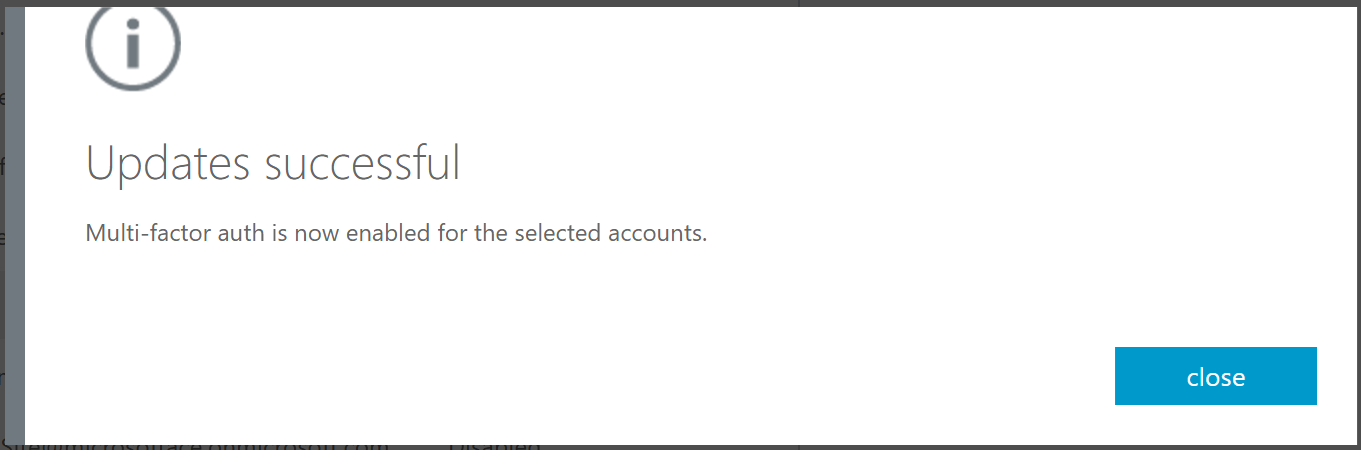

For Reference: How Azure Multi-Factor Authentication works
When you hit "Enforce"

When user attempts to login.
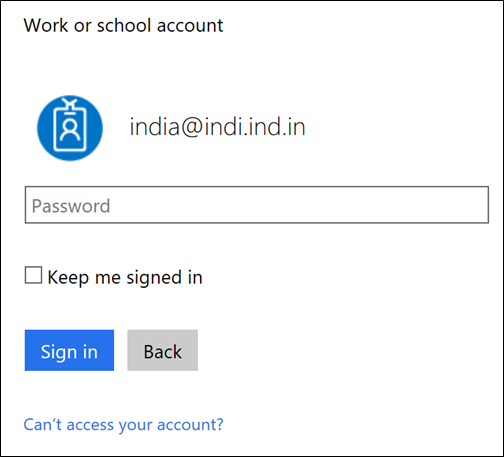
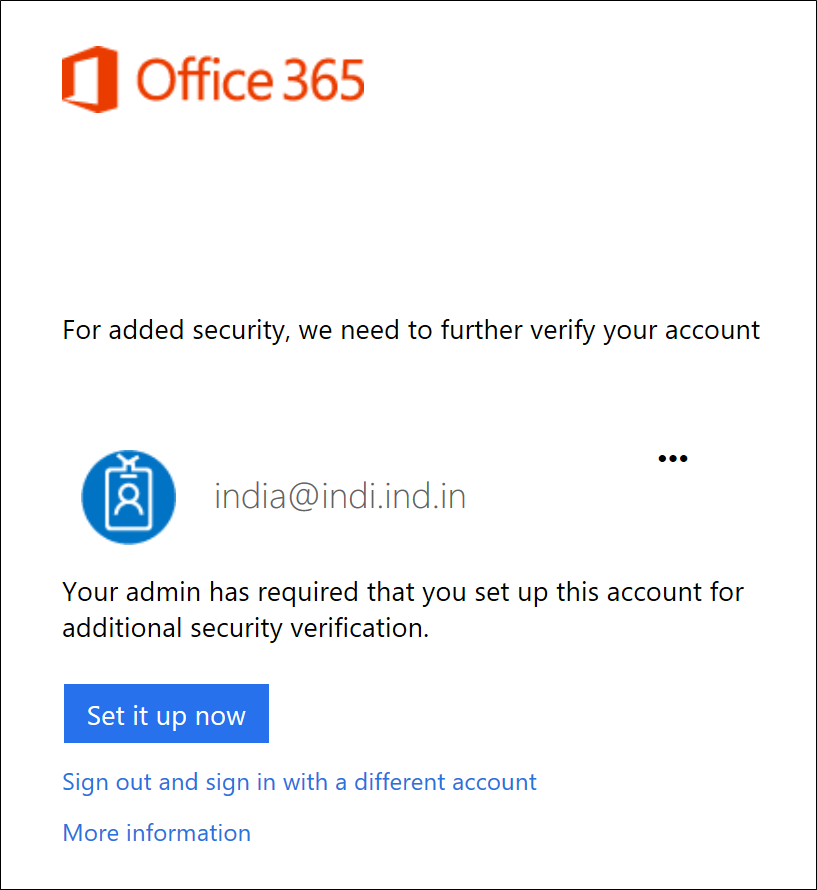
For Reference: Manage your settings for two-step verification
For Reference: How To Set Up Multi-Factor for Your Account
From < https://channel9.msdn.com/posts/Multi-Factor-Account-Setup >
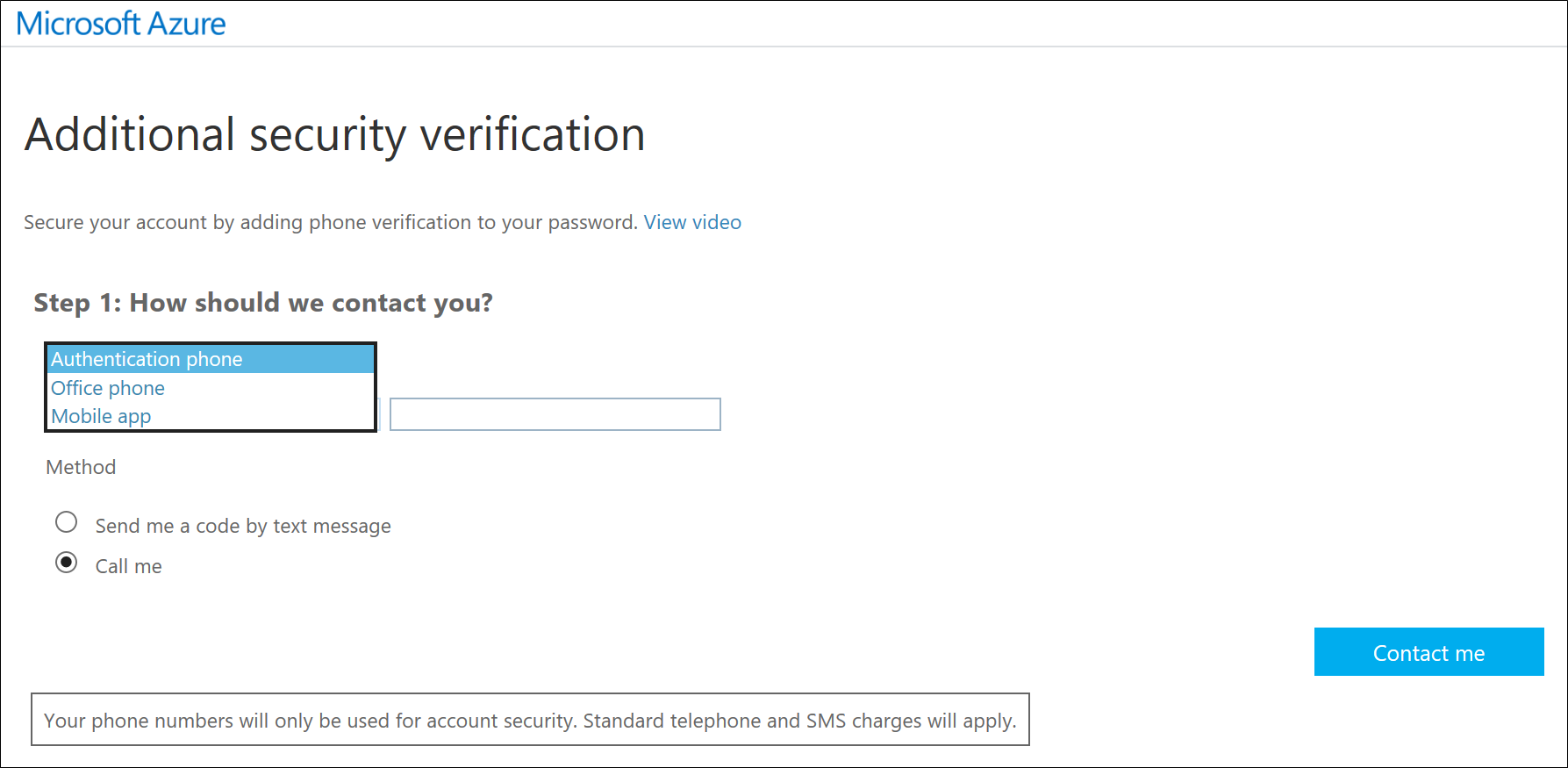
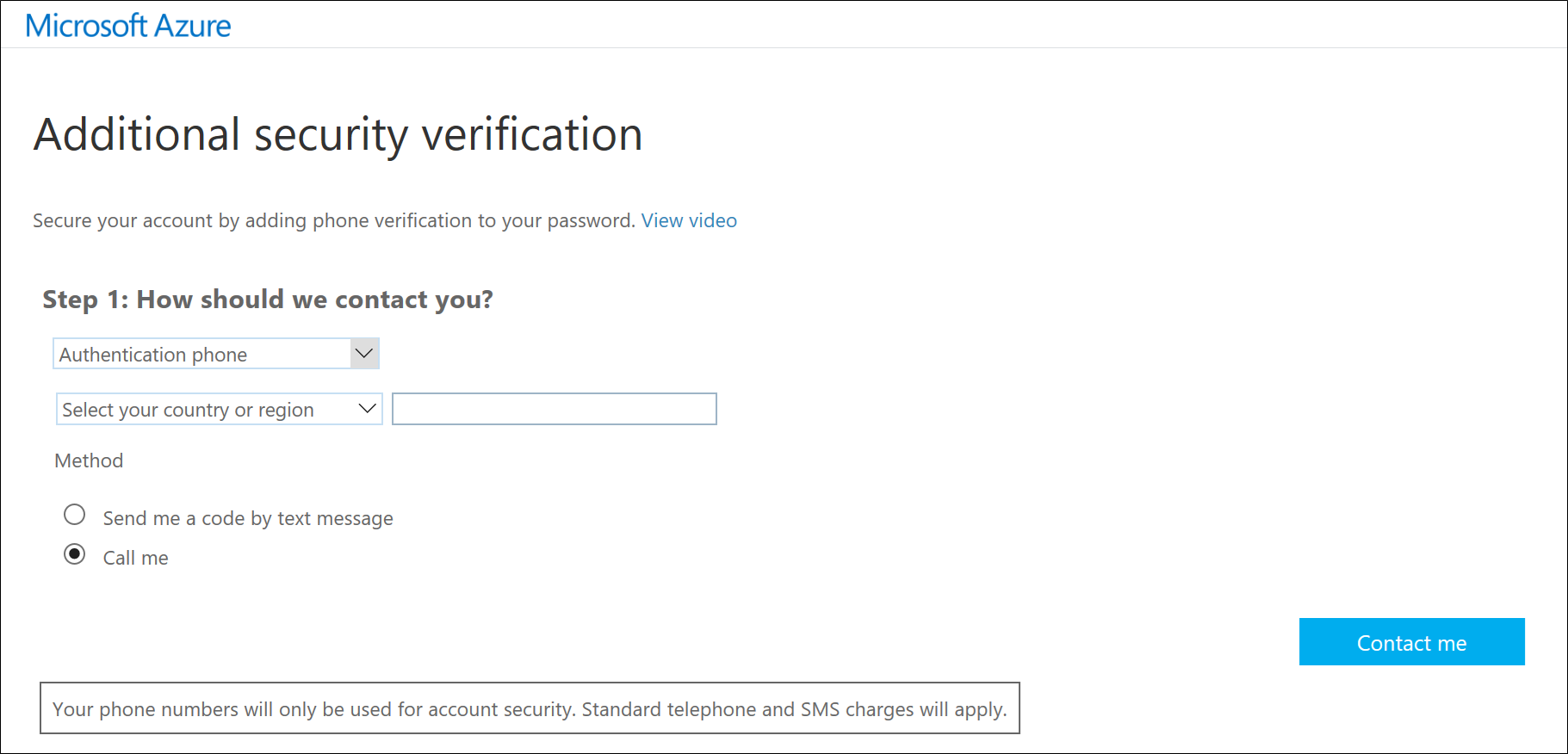
Option 1 - Authentication Phone
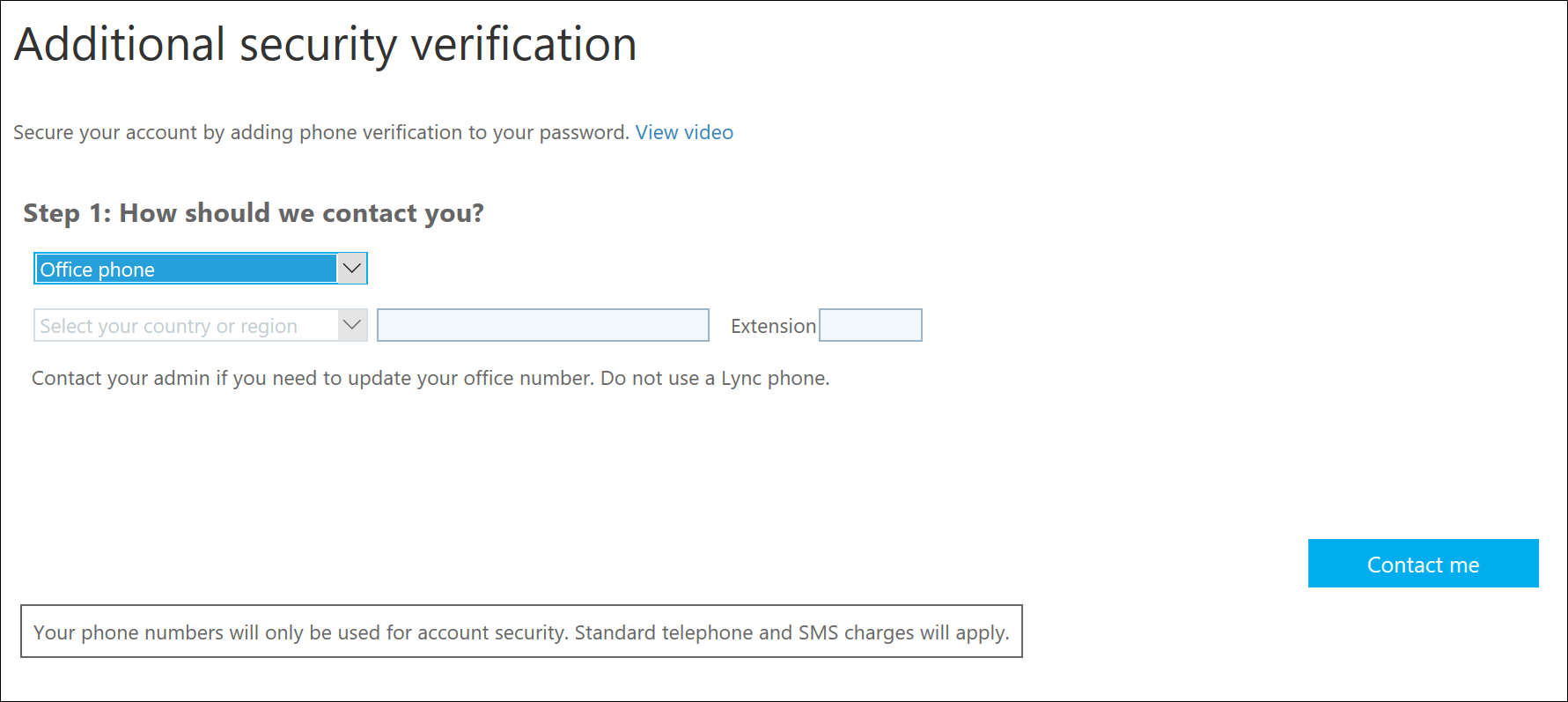
Option 2 - Office Phone
Option 3 - Mobile App
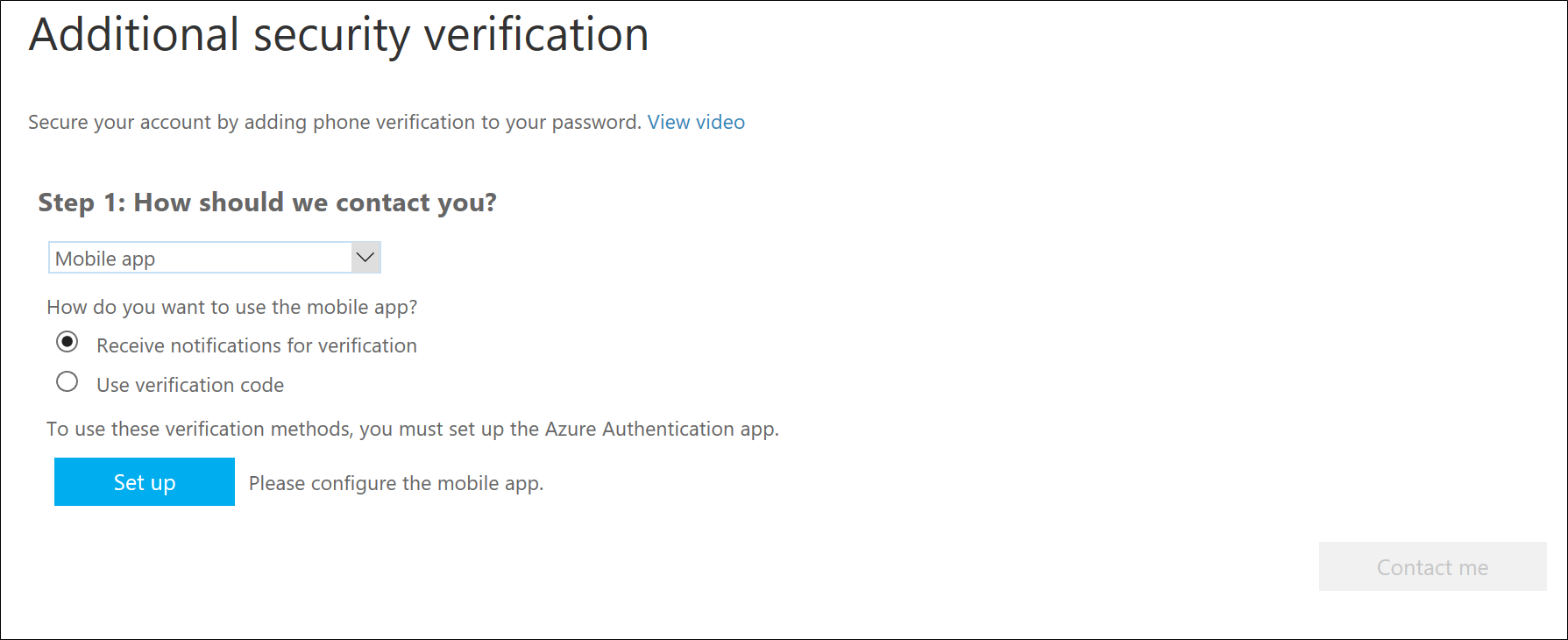
I chose to receive my verification code as a text message on the "Authentication Phone" option.
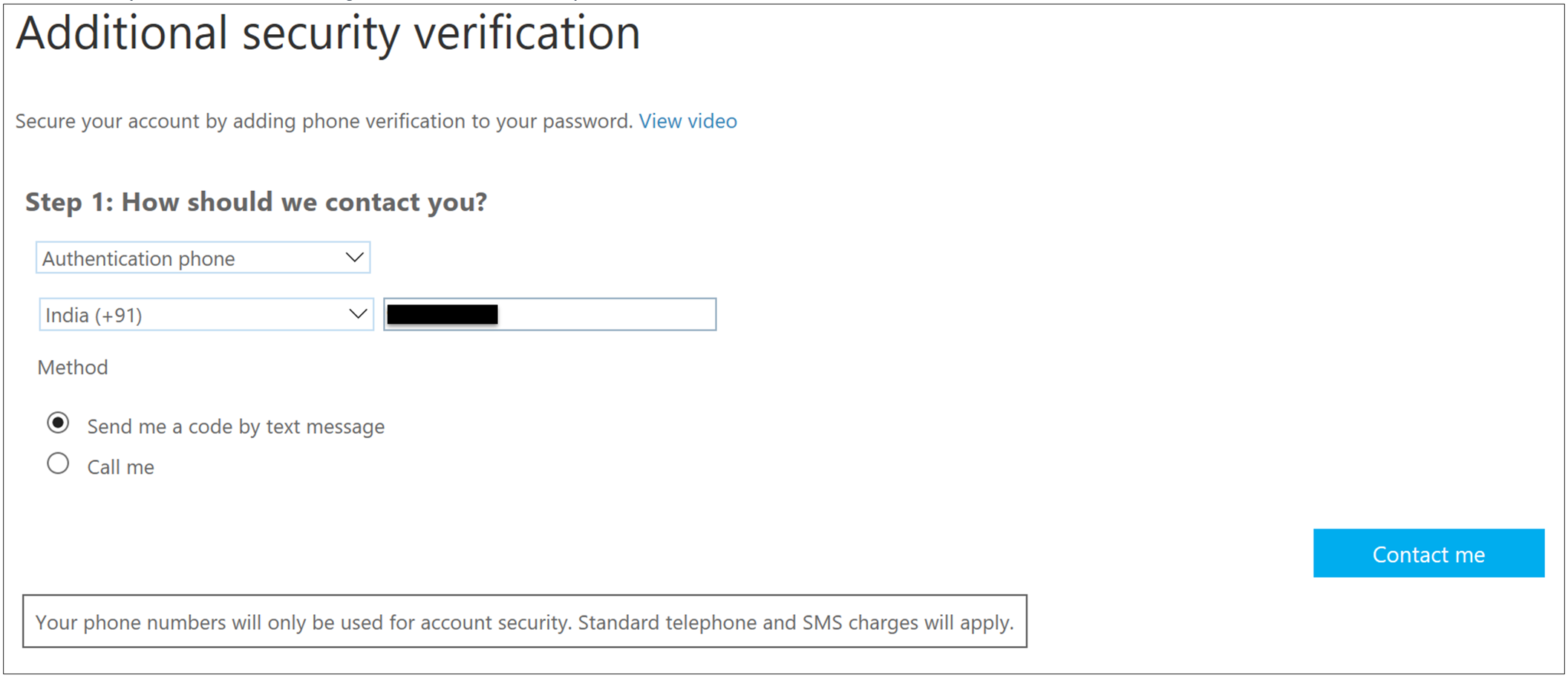

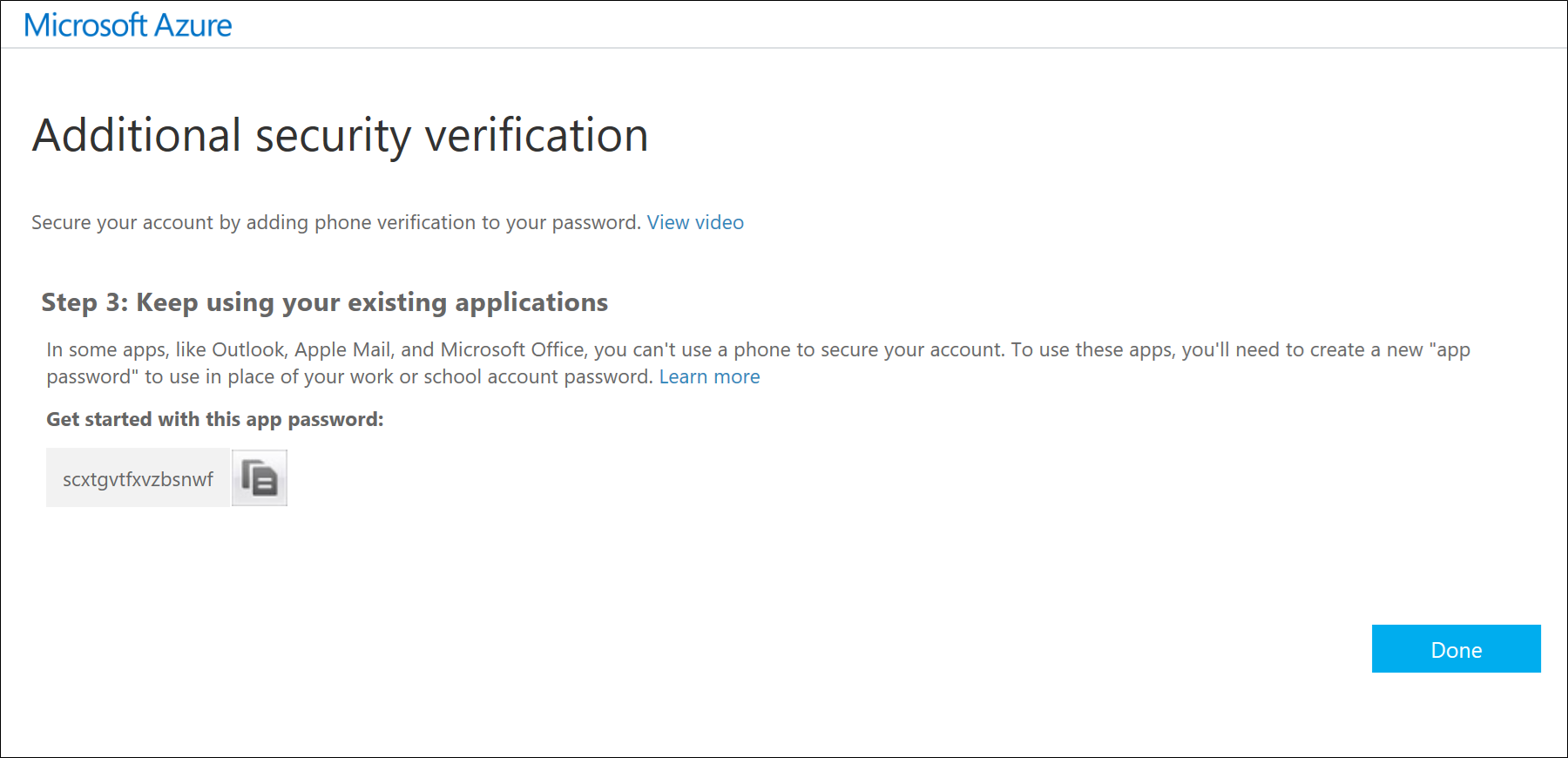
For Reference: Managing your Azure Multi-Factor Authentication User Settings
From < https://technet.microsoft.com/library/en-us/dn270518 >
|
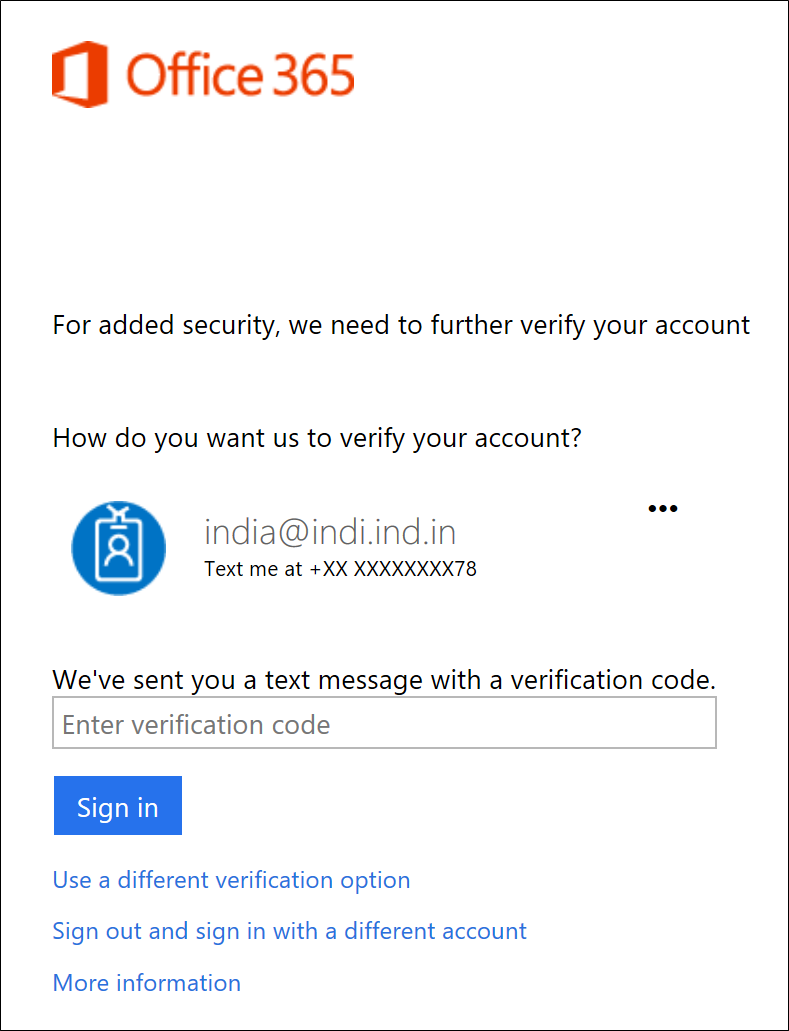
This is my GENERAL login experience.
Login experience through PowerShell

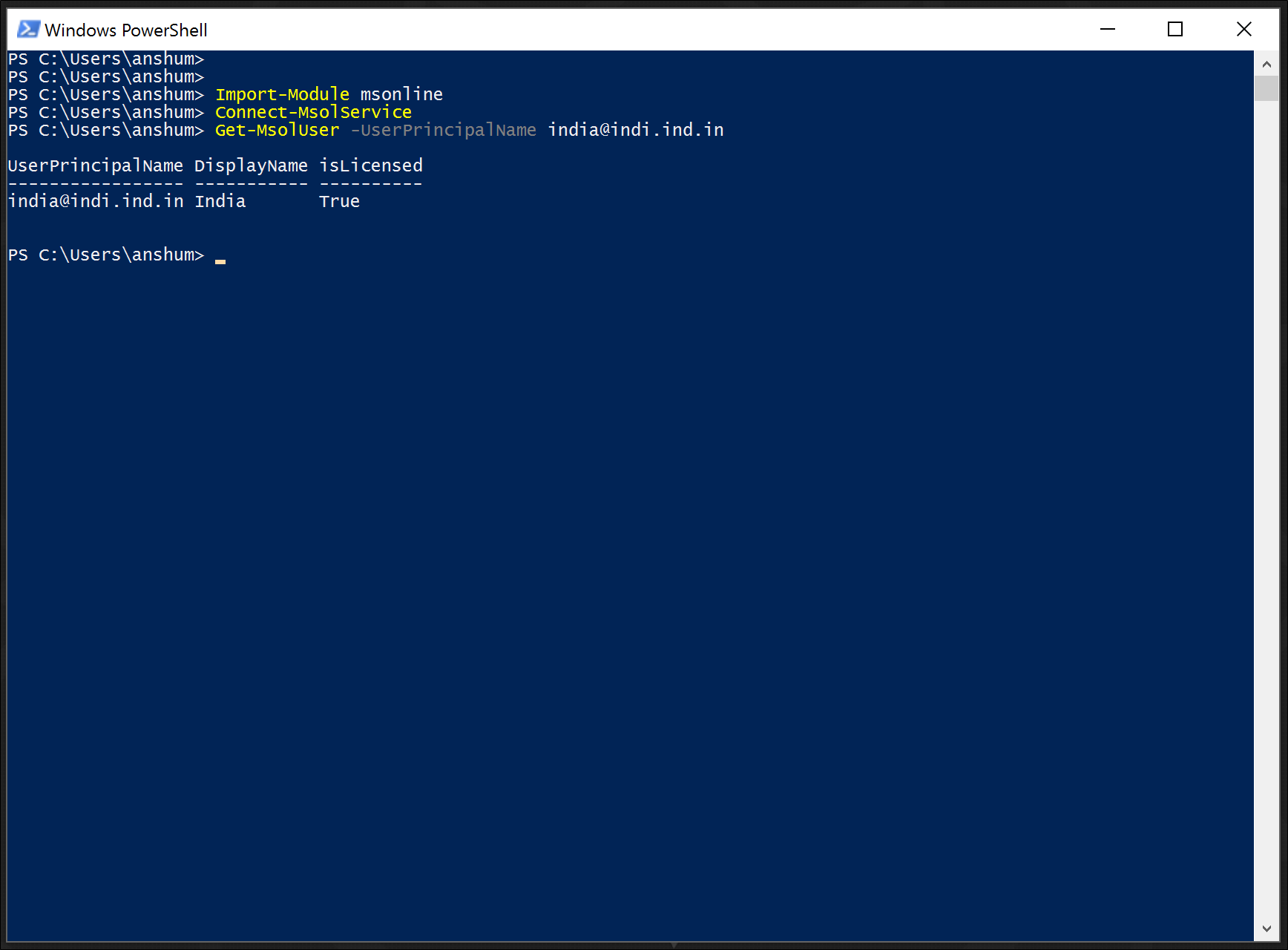
And I am connected
Anshuman Mansingh | ||
Technology Solutions Professional, Microsoft | ||

Comments
- Anonymous
March 17, 2017
We have been going through this and trying to enable MFA for O365 users. That said, we have hit some road block with questions regarding licensing, and our Microsoft representatives are less than clear about it.The way I understood is O365 includes a form of MFA. We own O365 licenses.When we turn on MFA, it also turns on MFA for any application(non O365) that is authenticating against Azure AD. Essentially it is turning on MFA on Azure AD(the identity provider for O365). That is the right way to do.Technically it all works fine. However whether we are allowed to use O365 MFA for non O365 apps, is the question.As you know, O365 MFA comes with limited capability and there is no way to turn it off for non-O365 apps.If we can't use the MFA for non-O365 apps, we can't use it for O365 as well, which makes sense.Microsoft should be more clear about this situation. If we can use O365 MFA for non-O365 apps, we don't want to pay for MFA twice and license again.