Rules Extensions –Understanding Date Time Conversion Part 1
Recently I have received several questions and “Ridiculous” Comments on the Posting 2 Way Account Expires Rules Extension , before I continue please understand that this Blog Site is intended to be a guide, and a tool to assist with your Identity Management Solution. But without know what modification, changes or updates that have been applied to your Environment there is NO way the I can guarantee that the information that is provided in this blog will be 100 % correct for you. I can say that every effort has been made to endure that the information is correct and properly tested. For example the posting that seems to be causing the most concern is from an actual working Lab. This leads me to believe that the Blog posting could possibly need some further detail.
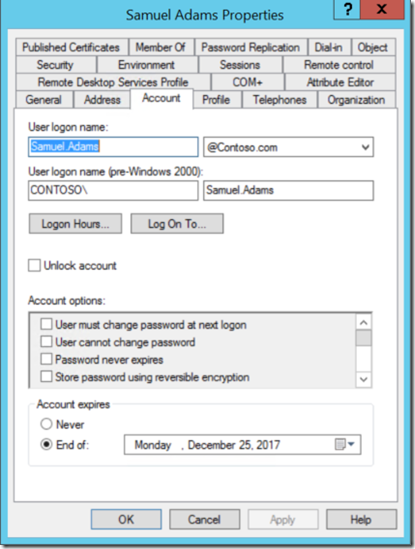
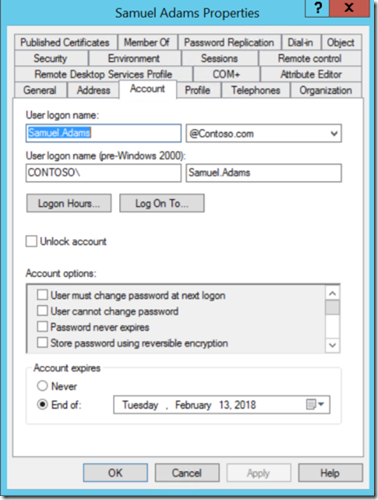
This image shows the account “Samuel Adams” having the “accountExpires” attribute changed to “Monday ,December 25, 2017”
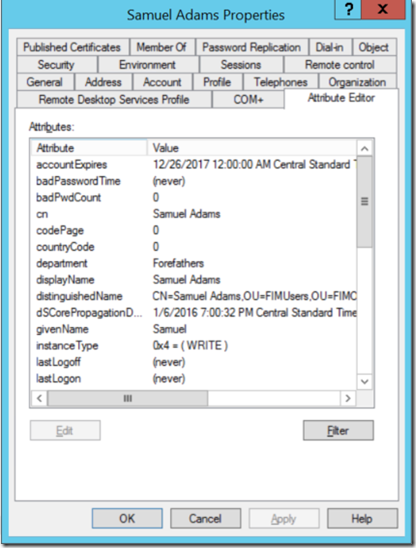
This Next image shows the change within the “Attribute Editor” Tab within ADUC
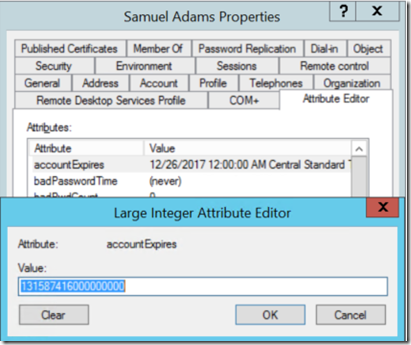
This next image shows what the newly set date of “Monday ,December 25, 2017” looks like under the hood so to speak.
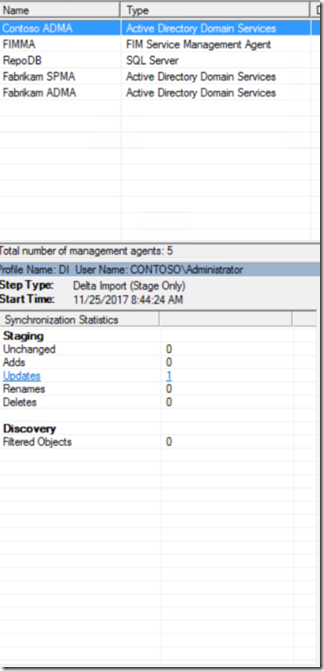
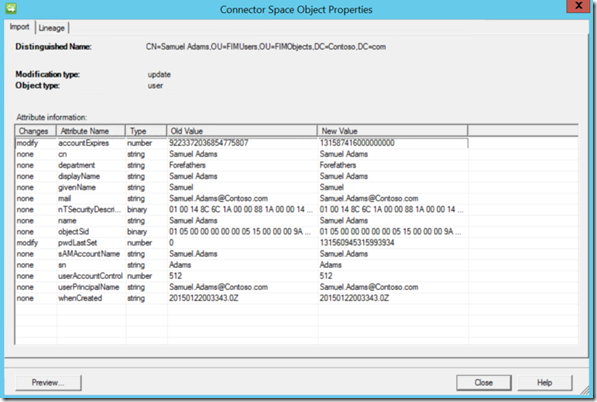
After running an Import on the Management Agent which is connected to the Active Directory Environment that the change was made on we now see an update which is coming into the connector space for that object.
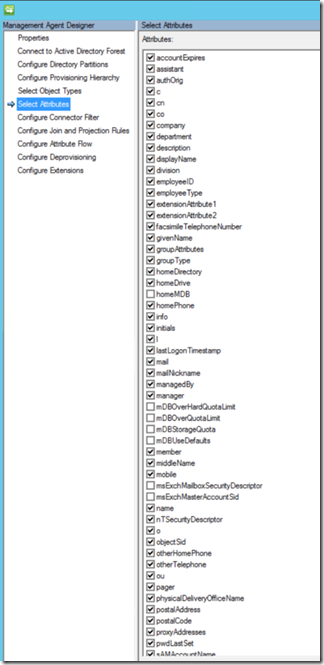
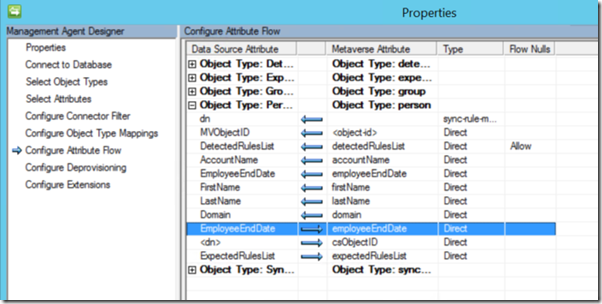
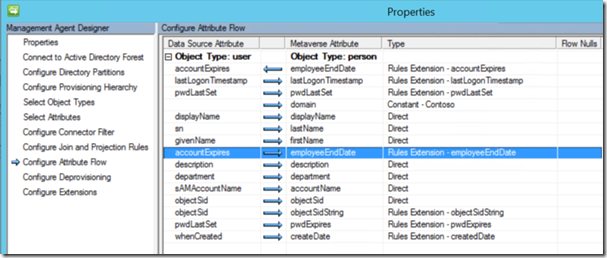
Before we go into the attribute flow of accountExpires to employeeEndDate lets look at the Management Agent that just picked up that change, notice in the Attribute Section I have the following attributes selected accountExpires, lastLogonTimestamp, and pwdLastSet
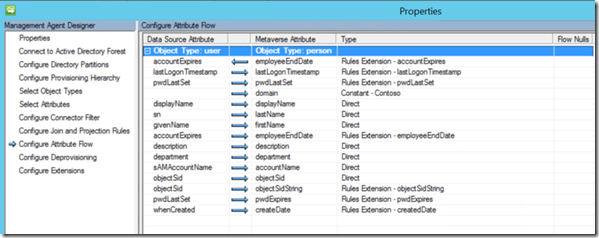
Now lets look at the Attribute Flow Settings
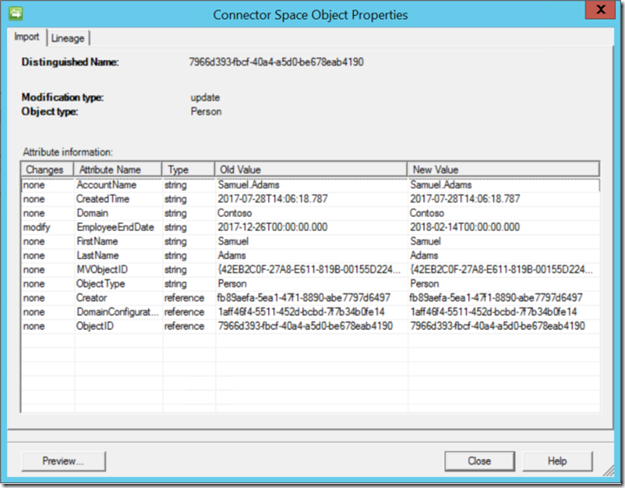
Now lets look at the change that came into the Connector Space for that account we changed the accountExpires Date for.
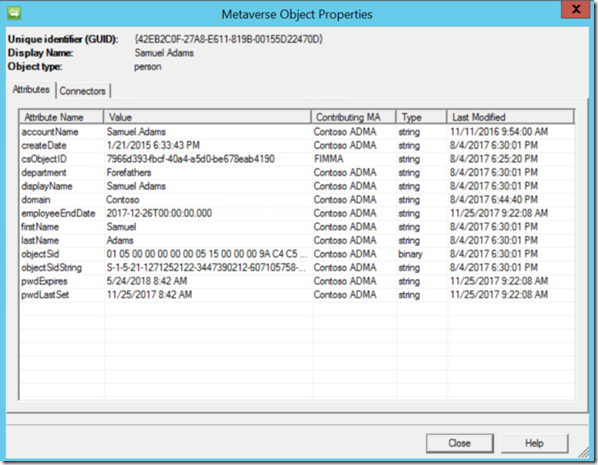
If we look at this object from the Metaverse we will see the value that was inserted via the Inbound Attribute Flow on the MA that connects to our data source.
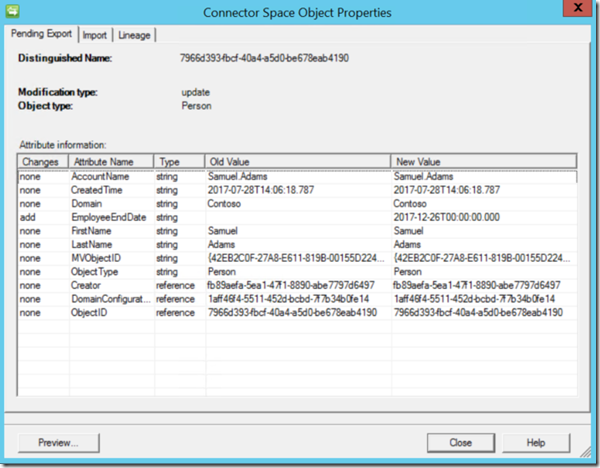
If we navigate back to the Management Agents Tab on the Synchronization Service (Console) and right click on the “FIMMA” or which ever MA that you use to connect to the FIM Service / MIM Service and you select Search Connector Space and for the scope you select “Pending Export” and select the “modify” filter and click on Search, locate the object that represents the object that had the accountExpires attribute changed in Active Directory. Notice that the attribute “EmployeeEndDate” has a value , notice the format, notice the strange format the value is in including the “T” in the middle of the date time. If the “T” is not in the DateTime value FIM / MIM will fail to recognize the Value.
Run on Export on the FIMMA / MIMMA and verify that the object was exported into the FIM / MIM Portal.
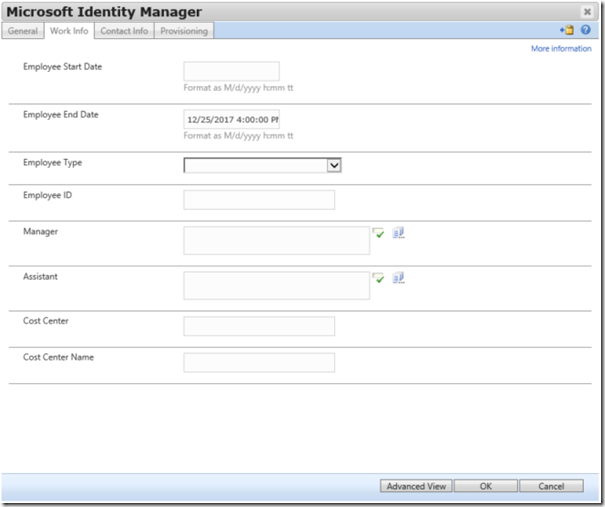
Now locate the object in the FIM / MIM Portal and within the “Work Info” Tab which is the default location you will find the “Employee End Date” attribute and the value should now match the value defined in Active Directory.
If for some reason you can not locate the “Employee End Date” attribute the RCDC may have been modified and the attribute could have been moved to a different TAB or removed from the UI all together. You can always locate the attribute by clicking on the “Advanced View” button at the bottom of the popup window and click on “Extended Attributes”
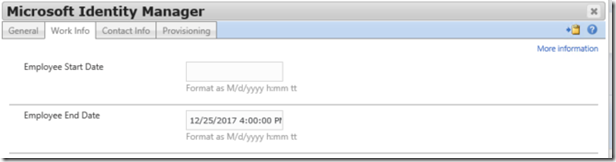
Notice the format of the DateTime now as it is being displayed in the FIM / MIM Portal
Now that we have successfully modified the Employee End Date via the accountExpires attribute in on an object in Active Directory lets demonstrate what happens when we update the same object in the FIM / MIM Portal “Employee End Date”
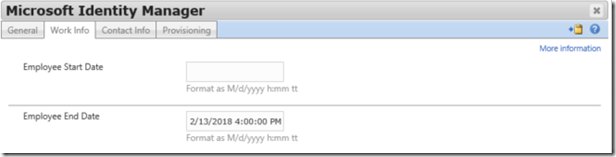
Update the object in the FIM / MIM Portal to a completely new date for the “Employee End Date”, save the change and run an Import on the “FIMMA / MIMMA”
Verify the change has been brought into the Connector Space of the “FIMMA / MIMMA”
Run a sync on the “FIMMA / MIMMA” and verify and run an Export on the “ADMA” or which ever MA that is connected to the Active Directory Source you wish the object to be updated in.
Check the “accountExpires” attribute in Active Directory
If for some reason this doesn’t work verify the following
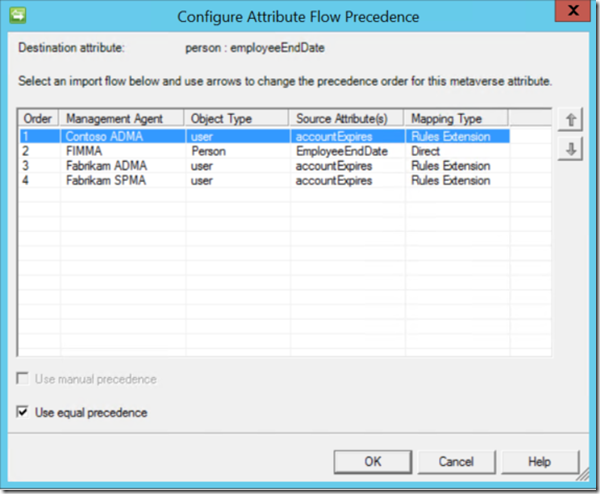
1. "FIMMA / MIMMA” has an Attribute Flow for EmployeeEndDate ---> employeeEndDate Direct Flow
2. Verify that “Use equal precedence” is selected for the “employeeEndDate” attribute in the Metaverse.
3. Verify that the attribute flow on the “ADMA” is set for accountExpires to employeeEndDate like the image below.
4. Verify the rules extension that is used. Rules Extensions –Understanding Date Time Conversion Part 2