Bitlocker Auto-unlock
Hello
Its Rafal Sosnowski from Dubai Microsoft Security PFE Team. I haven't posted much over the past year so let’s roll. Today I want to explain Bitlocker protector called Auto-unlock.
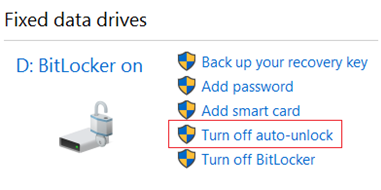
Auto-unlock feature allows a user to access the data and removable data drives without entering the password every time. It works only while OS drive is encrypted with Bitlocker.
You can enable/disable Auto-unlock protector using:
Command line:
Enable-BitLockerAutoUnlock
Disable-BitLockerAutoUnlock
PowerShell:
manage-bde -autounlock -enable D:
manage-bde -autounlock -disable D:
When you enable Auto-unlock, another copy of Volume Master Key (VMK) gets created on the disk and is wrapped by this protector.
If we query status of the volume, Auto-unlock will be indicated by “External Key (Required for automatic unlock) ”. It has the same structure as External Key (another protector which in fact might be placed on USB and loaded from there to unlock the drive – called USB startup key or USB Recovery Key).
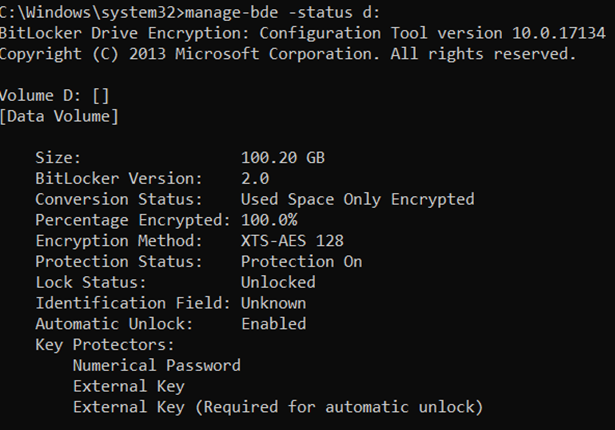
That external key used for automatic unlock is stored in the registry of the Operating System. This explains why it requires Operating System drive to be encrypted (otherwise attacker could have offline access to these keys)
Fixed data drives:
HKLM\SYSTEM\CurrentControlSet\Control\FVEAutoUnlock\*
Removable drives:
HKCU\Software\Microsoft\Windows\CurrentVersion\FveAutoUnlock\*
Keys are bound to specific user/computer, so we cannot copy them to another machine and allow access. Specifically, they are encrypted with DPAPI (Data Protection API) using the combination of user name and user password (or computer credentials). I believe there is additional entropy because I was not able to decrypt them using my DPAPI tools.
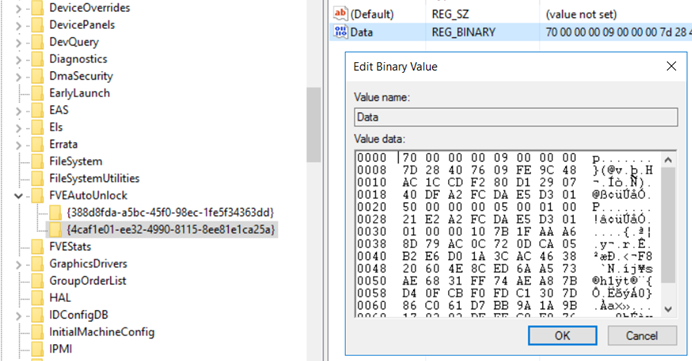
Additionally Auto-unlock keys for fixed drives are stored in protected registry hive, so the only way to analyze them is to export them from the online registry editor and then take ownership of the key and modify ACLs.
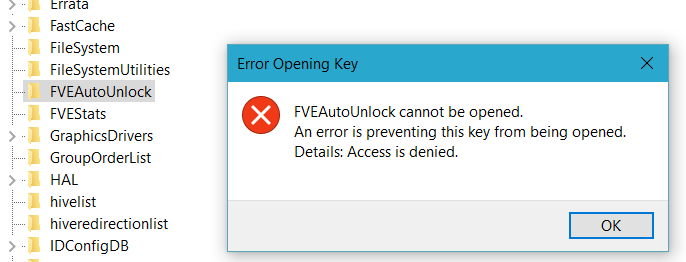
If you want to disable BitLocker on C: drive – system will warn you that all drives that are using auto-unlock need to be decrypted:
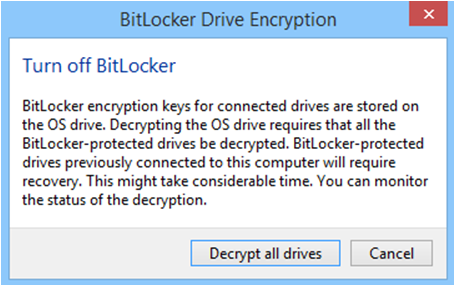
So, I recommend deleting these keys beforehand and adding another protector (password, smartcard certificate) so we are not left with Bitlocker Recovery Password only:
Clear-BitLockerAutoUnlock.htm
manage-bde -autounlock -ClearAllKeys C:
I hope it was informative.
Rafal