Granting permission to certificate
For the past few days, I’ve been delving really deep into Geneva, though it can be really frustrating at times because it takes awhile to learn the definitions. Although I’m somewhat familiar with terms like Relying Party (RP), Identity Provider (IP), and Security Token Service (STS) due to my little research on Cardspace a couple years ago, it’s still a daunting task when more terms are unravelled before you. So far the best article I’ve read is from the beautiful Michele Leroux Bustamante in her article named “Building a Custom Security Token Service”. I tried out her sample app and it shows how to build a custom active STS. However my aim is to build a custom passive STS because the client is accessing through a web browser and all my RPs are web apps. This article was very informative in explaining the gotcha when authenticating using a passive STS. I’m far from completing my little POC but I feel compelled to write what I’ve learnt before I totally forgot about it.
In order for Michele’s active STS to work you have to import a number of certificates into your LocalComputer cert store. Her Certificates Setup document was pretty good in explaining how to create and install the certificates. However I got lost in her section on Certificates Security. The section talks about private keys installed into the LocalMachine cert store must be accessible at runtime by the host running the RP or STS. Since these are web apps, the ASP.NET account must have access. It then talks about running the Certificate Key File Tool (certkeyfiletool.exe) which is located in the \bin directory of the Windows SDK. After searching high and low, I found a webpage on MSDN that says that this tool no longer exists. To replace it somewhat is a sample app called FindPrivateKey.exe. This sample app has to be extracted from the WCF samples archive in C:\Program Files\Microsoft SDKs\Windows\version\Samples. I trust you do not want to extract all the sample apps in this archive. Since the files in the archive are already sorted by its respective path, look for TechnologySamples\Setup\CS\FindPrivateKey.
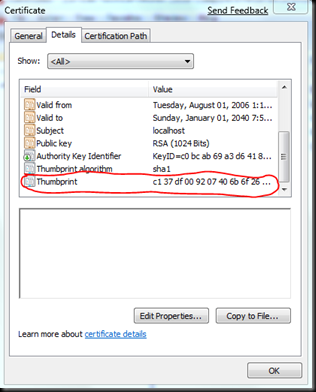
Build the FindPrivateKey project in Visual Studio 2008. In order to find the private key, you need to get the thumbprint of your certificate. Assuming you have a certificate called “localhost” and it is already imported into your LocalComputer’s Personal cert store. Run mmc, add the Certificates snap-in, choose Local Computer Account, and under Personal, open the localhost certificate.
Copy the thumbprint.
Run the Windows SDK CMD Command Shell as Administrator, and type this at the command prompt:
FindPrivateKey.exe My LocalMachine -t "c1 37 df 00 92 07 40 6b 6f 26 20 10 a8 74 57 bb 35 92 e1 3e" –a
(of course replace the string in quotes with the thumbprint of your certificate).
Running this returns the physical location of your certificate. Copy the entire path from the CMD shell and paste it onto Notepad. You will need to remove the leading spaces on the 2nd line of the path.
Next run the cacls.exe utility from the same CMD shell.
cacls "C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys\51fd35739bae502ad67f4
d4086d32400_3271abe4-895a-4463-82fe-267f8027cb2a" /E /G "Users":R
For starters, I just grant permission to User group on my machine. However the permission should be granted to the user account under which the application code may be running. For example, if the ASP.NET application always runs under a dedicated user account, you will use that account. You can determine the name of the account by calling WindowsIdentity.GetCurrent().Name to find what account you need to grant access. You may put this in your web application to find out the account of the IIS default application pool. If all is default, you should see the computer account as IIS APPPOOL\\DefaultAppPool.
Run the following command again:
cacls "C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys\51fd35739bae502ad67f4
d4086d32400_3271abe4-895a-4463-82fe-267f8027cb2a" /E /G "IIS APPPOOL\DefaultAppPool":R
You may also try the steps above if you get this error:
System.Security.Cryptography.CryptographicException: The system cannot find the file specified.
Source Error:
An unhandled exception was generated during the execution of the current web request. Information regarding the origin and location of the exception can be identified using the exception stack trace below.
Comments
- Anonymous
April 16, 2009
PingBack from http://microsoft-sharepoint.simplynetdev.com/granting-permission-to-certificate/