Client Certificates V/s Server Certificates
In the past I have blogged about various certificate file extensions along with their usage. Here is the link: https://blogs.msdn.com/b/kaushal/archive/2010/11/05/ssl-certificates.aspx
I use blogs as reference so that they can refer the content and I need not repeat the same thing every time. Saves time and helps others too.
This time I thought of writing another blog explaining the difference between Client Certificates and Server Certificates. Something which is not clearly understood by everyone. I will be discussing this strictly in context of IIS only. (There are several types of certificates)
One of my colleagues, David Dietz has already published a KB article relating to this:
IIS and client certificates: https://support.microsoft.com/kb/907274
The above documentation is good enough to understand the difference between client and server certificates along with error messages associated with them.
Lets start off in an Layman’s language and then I’ll discuss it in complete depth.
- How are Client and Server Certificates different?
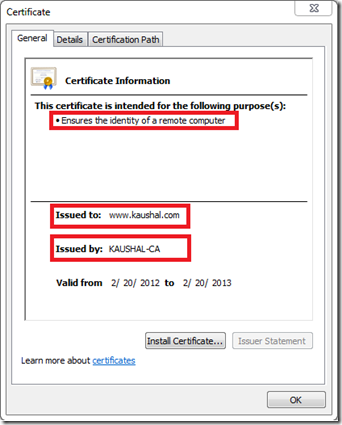
Server Certificates: Server Certificates are used to identify a server. Typically they are issued to hostnames, which could be a machine name (like “PIIS-SVR01”) or a host-header (like “www.Microsoft.com”). Both client and server certificates have the “Issued to” section. For a server certificate the “Issued to” section’s value would specify the hostname for which it has been issued.
Server Certificates serve the purpose of encrypting and decrypting the content.
Read the highlighted text in the above certificate, it says “Ensures the identity of a remote computer” i.e., “localhost”. This is a self-signed certificate i.e., one issued a certificate to itself. (To be precise where the “Issued to” and the “Issued by” value is same. In the real world only Root-CA’s have self-signed certificates).
Server certificates are stored in the Personal store of the “Local Computer” account.
Note: Certificates can be put in the personal store of a user account. However IIS will always search for the server certificate in the personal store of computer account.
Client Certificates: Client certificates as the name indicates are used to identify a client or a user. They are meant for authenticating the client to the server. In case of a client certificate the value of this field would be set to a users name.
Yes, I know it is a certificate too, but it is not used for encryption or decryption of data, but represents a user identity. ![]() Below is a Client Certificate which I issued to myself using my CA (KAUSHAL-CA).
Below is a Client Certificate which I issued to myself using my CA (KAUSHAL-CA).
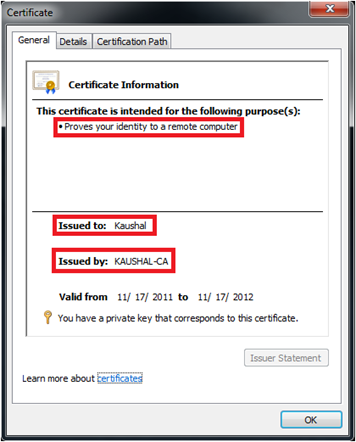 Client Certificate Client Certificate |
As seen above, the line is more than enough to inform you about the purpose of the certificate. It reads “Proves your identity to a remote computer”. Here ‘your’ means the user (Kaushal in this context).
- How are Client and Server Certificates Similar?
The only similarity between them is the keyword “Certificate”. They both contain public and private keys. For that matter, every certificate contains a public and a private key.
- How does IIS distinguish between Client and Server Certificates?
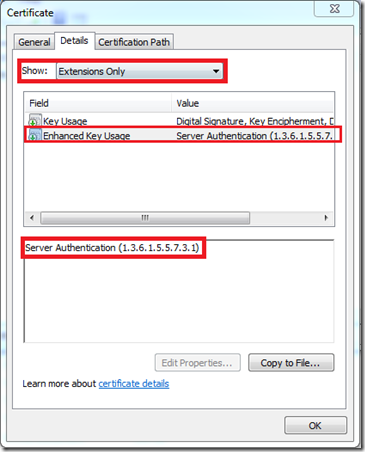
The above explanation was good enough to explain a user on how to identify client and server certificates. However, this is not how IIS determines it. The best way of determining the purpose of a certificate is to look at its “Enhanced Key Usage” field. (this is a optional field and may not be seen for all the certificate types).
The Enhanced Key Usage field specifies what can the public key of the certificate be used for. If the value is set to “Client Authentication(1.3.6.1.5.5.7.3.2) ”then you know what it is used for. ![]()
For Server Certificates the value of this filed would be set to:
“Server Authentication (1.3.6.1.5.5.7.3.1) ”.’
Every certificate has a Object Identifier (OID) associated with it. If you observed the OID for server certificate is “1.3.6.1.5.5.7.3.1” and for Client Certificate it is “1.3.6.1.5.5.7.3.2”.
Here is a snippet from RFC 3280
Housley, et. al. Standards Track [Page 40] RFC 3280 Internet X.509 Public Key Infrastructure April 2002 id-ce-extKeyUsage OBJECT IDENTIFIER ::= { id-ce 37 } ExtKeyUsageSyntax ::= SEQUENCE SIZE (1..MAX) OF KeyPurposeId KeyPurposeId ::= OBJECT IDENTIFIER Key purposes may be defined by any organization with a need. Object identifiers used to identify key purposes MUST be assigned in accordance with IANA or ITU-T Recommendation X.660 [X.660]. This extension MAY, at the option of the certificate issuer, be either critical or non-critical. If the extension is present, then the certificate MUST only be used for one of the purposes indicated. If multiple purposes are indicated the application need not recognize all purposes indicated, as long as the intended purpose is present. Certificate using applications MAY require that a particular purpose be indicated in order for the certificate to be acceptable to that application. If a CA includes extended key usages to satisfy such applications, but does not wish to restrict usages of the key, the CA can include the special keyPurposeID anyExtendedKeyUsage. If the anyExtendedKeyUsage keyPurposeID is present, the extension SHOULD NOT be critical. If a certificate contains both a key usage extension and an extended key usage extension, then both extensions MUST be processed independently and the certificate MUST only be used for a purpose consistent with both extensions. If there is no purpose consistent with both extensions, then the certificate MUST NOT be used for any purpose. The following key usage purposes are defined: anyExtendedKeyUsage OBJECT IDENTIFIER ::= { id-ce-extKeyUsage 0 } id-kp OBJECT IDENTIFIER ::= { id-pkix 3 } id-kp-serverAuth OBJECT IDENTIFIER ::= { id-kp 1 } -- TLS WWW server authentication -- Key usage bits that may be consistent: digitalSignature, -- keyEncipherment or keyAgreement id-kp-clientAuth OBJECT IDENTIFIER ::= { id-kp 2 } -- TLS WWW client authentication -- Key usage bits that may be consistent: digitalSignature -- and/or keyAgreement id-kp-codeSigning OBJECT IDENTIFIER ::= { id-kp 3 } -- Signing of downloadable executable code -- Key usage bits that may be consistent: digitalSignature id-kp-emailProtection OBJECT IDENTIFIER ::= { id-kp 4 } -- E-mail protection -- Key usage bits that may be consistent: digitalSignature, -- nonRepudiation, and/or (keyEncipherment or keyAgreement) id-kp-timeStamping OBJECT IDENTIFIER ::= { id-kp 8 } -- Binding the hash of an object to a time -- Key usage bits that may be consistent: digitalSignature -- and/or nonRepudiation id-kp-OCSPSigning OBJECT IDENTIFIER ::= { id-kp 9 } -- Signing OCSP responses -- Key usage bits that may be consistent: digitalSignature -- and/or nonRepudiation |
snippet of RFC describing the various Object ID’s associated with certificates.
- How do I know what is the Enhanced Key Usage value for that certificate?
Double click on the certificate to view it. FYI, it opens with “Crypto Shell Extensions”.
Go to the Details tab and select “Extension Only” from the “Show” drop down box as shown below:
This is a clear indication of the intended purpose of the certificate.
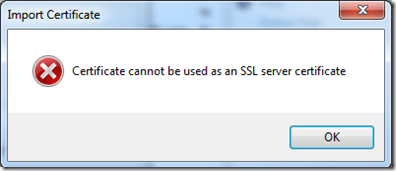
- Can I use a Server Certificate as a Client Certificate or Vice-Versa?
NO is the answer to this question and its very obvious. If you try importing a client certificate to the IIS 7/7.5 you will receive the following error:
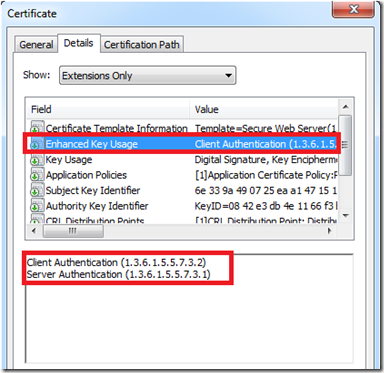
Note: There are certificates which can be issued for multiple purposes like the one shown below. This is meant for both Client and Server Authentication.
Hope this cleared some doubts! ![]()
Comments
Anonymous
February 18, 2012
Great post. you should create a Wiki page with all of these resources for easier discovery by newbies to TLS like me. But you said something about the account to whose store a certificate has to be imported into based on its purpose. What if the IIS computer isn't joined to a domain, therefore there are no computer accounts, but only user accounts? Then?Anonymous
February 19, 2012
Very nice article Kaushal. Good workAnonymous
April 27, 2012
excellent explanation. Cleared all my doubts.Anonymous
April 28, 2012
Hi Cron, Sorry for the late reply. I have been very busy with other stuff and didn't find time to review my blogging space. I didn't understand your question completely. But I will try to clear your doubt. So, it doesn't matter whether a certificate is part of a domain or not. Certificates don't require the computer to be part of a domain. You can continue to have certs even if they are not part of any domain. To be clear, certificates are just files, which contain some data which is consumed by the crypto services of the OS (Windows/Unix/others) Hope this clears. :)Anonymous
July 10, 2012
Every certificate contains a public and a private key? Really? I thought that private keys are private....Anonymous
July 11, 2012
Yes! Certificates implement Public Key Cryptography. SO they are bound to have Private and public keys. But, yes the private keys are private and only known to one person who owns the certificate. For example in case of Server certificate, the private key is present on the server only and in case of Client Private key is present only on Client. Public key is distributed or is available as part of the certificate.- Anonymous
December 30, 2016
i just accessed google.com in my browser and ssl certificate for google.com domain is enabled with both client and server authentication.Server Authentication (1.3.6.1.5.5.7.3.1)Client Authentication (1.3.6.1.5.5.7.3.2)Ensures the identity of a remote computerProves your identity to a remote computer1.3.6.1.4.1.11129.2.5.1as per my knowledge the browser/client will provide its own certificate to prove its identity to server when client authentication is enabled and server wants to authenticate a client.. so in this scenario while accessing google.com are we presented with any certificate for proving our identity? i guess its not. can you please clarify this thing?
- Anonymous
Anonymous
October 15, 2012
great explanation. looking for this since a long timeAnonymous
January 13, 2013
very nice post. very good explanation. detailed and comprehensive. Thanks heaps.Anonymous
June 25, 2013
Hello Kaushal, Its good see all the details about certificate, thanks. I am facing one problem with certificate, I could install certificate thru MMC but I can implement it, bcoz I can see the certificate in Webserver console, RDP console Plz help Thank youAnonymous
July 30, 2013
Hi Anirudha, I don't understand the question. Could you provide more details on the problem?Anonymous
August 01, 2013
Hi Kaushal, Thank you for the nice and simple post :)Anonymous
November 11, 2013
Great detail post! I have some questions. What is the purpose of the certificate with both Server and Client Authentication? Do you know how to create this type of certificate? Thanks.Anonymous
November 13, 2013
I am not a big fan of having both for the same certificate as they are quite a conflict. But if you try to submit a custom certificate request then you could select both client and server authentication form the dropdown.Anonymous
December 04, 2013
I knew about 90% of that, but was happy to learn the other 10% that is hard to come by in brief form. What resources can you suggest for someone who wants to go further into understanding what all those parts of a certificate do and how they fit together? I am currently writing a PowerShell script for an installer to use to creaet a self-signed certificate for SAML token En/Decryption. (Independent of the SSL cert.) The latest APIs, supporting bigger keys, have many parts to them that I really should understand better. Like, why do we lump so much functionality into a process or program called Certreq.exe? What exactly is a certificate request that makes it a likely foundation for doing all those other things it can do? See what I mean? I just need to understand the mechanics better and I do not know where to start. It is complexity built on complexity, but I am ready for that.Anonymous
December 21, 2013
Good article Bro! Thanks for sharing...Anonymous
January 26, 2014
Awesome blog! Solved the mystery in a matter of seconds! Thanks a lot :)Anonymous
February 02, 2014
Glad that it helped a lotta folks.. :)Anonymous
March 10, 2014
Firstly thanks for your informative blog posts. I have been debugging a problem where IE would not allow a client certificate to be used even though the Enhanced Key usage was correct (1.3.6.1.5.5.7.3.2). Eventually I stumbled across the KeySpec using CertUtil and it appeared to be set to "KeySpec = 1" which in my understanding is "Key Exchange" which should also include use for "Signature" purposes. However IE would not accept the certificate. I solved the problem by requesting a new certificate specifically for "Signature" with "KeySpec = 2" and also including the Enhanced Key usage of (1.3.6.1.5.5.7.3.2). I am confused as to how these two properties related and exactly what the Keyspec of exchange means. When you use certificate services to request a certificate and the CSP is set to "Microsoft Enhanced Cryptographic Provider" you can choose a KeySpec of "both" however if the provider is "Microsoft RSA SChannerl Cryptographic Provider" then only "Exchange" is selectable. Any explanation you can offer for keyspec and how it is used would be very welcome as I have done a lot of research on this area and come up mostly blank.Anonymous
March 27, 2014
@reidca the keyspec property governs the usage of the private key associated with the certificate. It plays a trivial role in deciding the fate of the certificate. It can have 3 values as shown below
Value Meaning
XCN_AT_NONE (0) The intended use is not identified. This value should be used if the provider is a Cryptography API: Next Generation (CNG) key storage provider (KSP).
XCN_AT_KEYEXCHANGE (1) The key can be used for encryption or key exchange.
XCN_AT_SIGNATURE (2) The key can be used for signing
The corresponding value of keyspec decides what purpose the private key can be used for. Here is the MSDN documentation for this: msdn.microsoft.com/.../aa379020(v=vs.85).aspx HTH
- Anonymous
March 27, 2014
@reidca the keyspec property governs the usage of the private key associated with the certificate. It plays a trivial role in deciding the fate of the certificate. It can have 3 values as shown below
Value Meaning
XCN_AT_NONE (0) The intended use is not identified. This value should be used if the provider is a Cryptography API: Next Generation (CNG) key storage provider (KSP).
XCN_AT_KEYEXCHANGE (1) The key can be used for encryption or key exchange.
XCN_AT_SIGNATURE (2) The key can be used for signing
The corresponding value of keyspec decides what purpose the private key can be used for. Here is the MSDN documentation for this: msdn.microsoft.com/.../aa379020(v=vs.85).aspx HTH
Anonymous
March 27, 2014
Is it possible to create a client authentication certificate which is used to authenticate to say a web service on IIS that can be shared among clients? I would like to issue a single certificate that is loaded during application installation which can be leveraged by any number of machines for authentication to a web service. Something like a generic client authentication certificate used by many clients. Is this possible?Anonymous
March 27, 2014
Yes that is possible. You need to distribute the client certificate along with the private key to all the clients. I am not sure on how you planning to do this, but it is possible.Anonymous
April 02, 2014
Hi Kaushal, How would I go about authenticating a Microsoft client certificate from a java application running on tomcat, ideally from the application level. How can I authenticate against the CA server or do I need to to check the authenticity of the client certification? RegardsAnonymous
April 04, 2014
Hi Syed, I'm not sure if I understood your question correctly. What exactly do you mean when you say "Microsoft Client Certificate" Are you trying to implement Client Certificate Authentication?Anonymous
April 09, 2014
Hi Kaushal, We have Microsoft CA server to issue certificates locally. We have been asked to generate three files for the requester: a root , an intermediate, and user certificates files. Is this possible ?. We usually issue one per CSR request. How can we do this knowing the server is Unix and Application is Oracle App. Thanks alotAnonymous
April 10, 2014
@Aradi You need not generate the Root CA and the Intermediate CA certs. If you have a CA hosted then they are already present. However depends on whether you have a Root CA or a Intermediate CA. There is a download link provided within the certsrv app to download the certificate chain which consists the CA certificates. This is what you need to send to the users.Anonymous
April 11, 2014
Very useful information. Please keep it up.Anonymous
April 21, 2014
Thanks Kaushal , appreciate your answer.Anonymous
May 13, 2014
@Kaushal Thanks for the reply and sorry for the late reply - for some reason i do not get notified when people reply on this which means i have to remember to check it regularly to see whether there has been any updates. Anyway, regarding your explanation for KeySpec, am I right in thinking that a KeySpec of 1 should be valid for client authentication or must it be 2? I have mixed experiences getting IE to allow you to choose a certificate for Client Auth with some working OK with KeySpec 1 and some needing 2. The EKU has always been correct. I have tried to setup a test certificate template using "Microsoft Enhanced Cryptographic Provider" that allows us to request a KeySpec of Both but have been unable to do so. The "Both" option is never presented and one must always choose between Exchange and Signature. The blog post here: blogs.msdn.com/.../troubleshooting-403-7-client-certificate-required-errors-amp-step-by-step-to-make-sure-your-client-certificate-is-displayed-and-selected.aspx shows that this is required. Thanks for your continued help. CarlAnonymous
May 21, 2014
Hi Kaushal, I have created SSL mutual certificate for client and server in one machine. Whn i tried to access or to consume that service in another machine, I am getting "The page requires a client certificate " error. can you please guide me in this. Thank You! RajeevAnonymous
May 22, 2014
The comment has been removedAnonymous
June 01, 2014
@Kaushal, in respect of your answer to the Rajeev you can have an SSL certificate that has both EKUs. Nothing I am aware of says this is not possible. In fact the SSL certificate we use on our main web site (issued by a trusted CA has both these uses) Server Authentication (1.3.6.1.5.5.7.3.1) Client Authentication (1.3.6.1.5.5.7.3.2) We have successfully done this many times in the past. Are you able to advise regarding my KeySpec question? Thanks CarlAnonymous
June 01, 2014
Hi Kaushal, From one of your replies -- "Kaushal Kumar Panday 13 Nov 2013 12:20 PM # I am not a big fan of having both for the same certificate as they are quite a conflict. But if you try to submit a custom certificate request then you could select both client and server authentication form the dropdown." Can you be a bit more elaborate on the procedure to get such combi certificate. Thanks in advance.Anonymous
June 04, 2014
@reidca You can get certificate for multiple EKU's and still use it. This would work fine for a Server Certificate. Not diverting from the topic further. The KeySpec should be set to 1 and not 2. We set it 2 during signing of assemblies. Look at this: msdn.microsoft.com/.../aa379020(v=vs.85).aspx KeySpec is not the only deciding factor though. While generating a client cert the EKU should only be set to Client Authentication (1.3.6.1.5.5.7.3.2). Also pay attention to the Key Usage fields. @Mahesh See this: technet.microsoft.com/.../ff625722(v=ws.10).aspxAnonymous
June 10, 2014
How to get only CA certified certificate on store ? when we use certificate for Login or any other purpose then it can show ca certified certificate as well as system generated certificate then how can we allow only USB Token Certificates will available ?? Heeradhar DhiwarAnonymous
June 11, 2014
The client will always provide you options via a prompt to choose the required certificate. The authentication/authorization piece could be done at the web server or the application level. In IIS this is done via mappings. You could allow specific certificate only (this is one to one mapping) or allow a certificate from a specific CA (Many to one mapping) In application you could do the above yourself, by verifying either the thumbprint or the issuer field or both for the provided certificate. The choice is always yours.Anonymous
December 18, 2014
what are the certificate purposes for a LDAP SSL certificate?Anonymous
December 18, 2014
@Selami.. What is the certificate being used for.. There is nothing as "LDA Certificate" What are you using the certificate here for? Is it for authentication/Digital Signature or others? This article lists out couple of OOID's: support.microsoft.com/.../287547 See this wiki article: en.wikipedia.org/.../X.509Anonymous
January 07, 2015
Hi Kausal, For digital signature and encryption, are we using server certificate as well? anything extra need to be done in order to enable the server certificate for digital signature or encryption? Server certificate is the one we used for SSL channel?Anonymous
January 22, 2015
The only part of the document I disagree with is the following statement "The only similarity between them is the keyword “Certificate”. They both contain public and private keys. For that matter, every certificate contains a public and a private key. " --- Certificates are used to validate the public portion of a public/private key pair -- A certificate does not contain a private key -- it contains the public portion of the pair -- At least that is my understandingAnonymous
January 27, 2015
@Douglas Certificates are implementation of PKI which invovles Public & private keys. If a Certificate has a puiblic key, it is bound to have a private key. However when the certificates are clubbed with their private keys the file extension changes. I have explained it here: blogs.msdn.com/.../ssl-certificates.aspxAnonymous
February 09, 2015
There are two ways we use certificate - One is importing in keystore using keytool command , other is server dynamically download the certificate, technically how the the latter part happens?Anonymous
February 10, 2015
@Kabir: What certificate re you referring to? I am not aware of mechanism where the Server will download a cert.Anonymous
February 27, 2015
=>I am seeing list of certificates while i browse the website. I am using client certificate. =>Checked configuration editor in that system.webServer/security/authentication/iisClientCertificateMappingAuthentication-> webconfig Settings are as follows: many to one enable=true count =0 one to one enable=true count=0 =>We are getting list of certificates only when we browse website for first time not for subsequent/all pages.Anonymous
February 27, 2015
Hi Kaushal Kumar , The description what you are sharing regarding digital certificates is fantastic and clear to understand for the newbies like me. I have a question to ask , please help me. I am trying to generate a new Digital Certificate using Elliptic Curve Cryptography by revisiting through the OpenSSL Libraries. The question(s) am writing here :
- How can i know to change what piece of code from what file to achieve some task, for example i want to make the generated digital certificate should be ecc signed means ecdsa signed instead of rsa ,, for these kind of kinds how can i recognize the file name/piece of code within the stipulated time ? 2.How can i sign an email using pgp and how can i replace the sha-1 to sha-3 algorithm.I mean which file to modify ?
- I have a bit confusion about the three self-signed certificate , client certificate and server certificate from the document ecc-certgen.sh ? Please explain as soon as possible :-)
Anonymous
February 27, 2015
Sorry to write one more question : I want to download a CA free version certificate for an academic project purpose .I found that without a domain name the CA's like comodo, etc.. are not suppose to issue the certificate , If i want to download that Do i have to create a domain name and then download it or Is there any way to download that as a normal user ?Anonymous
April 13, 2015
Hi Kushal, I have a certificate that has both "Server Authentication" and "Client Authentication" purposes in the Enhanced Key Usage. Can I use this cert for client authentication even if I dont have the private key associated with it. My problem is - I added the cert to the store using certuitl commands. But still it won't show up in the list when chromium / chrome wants to send the client auth cert to the server. Thank you for your help DivyaAnonymous
May 10, 2015
I amtrying to implement client certificate authentication in IIS, its not happening can someone help me with the step by step process or a video recording with 1 working example.Anonymous
May 10, 2015
@Mitchel I don't have any post on configuring Client Certificates. You may refer the following article on IIS.NET: www.iis.net/.../iisclientcertificatemappingauthentication www.iis.net/.../clientCertificateMappingAuthenticationAnonymous
May 24, 2015
Does client certificate requires server certificate? say for example, my server wants to validate only clients. Clients does not need to worry about they are talking to correct server. So I require only client authentication. In this case, only client certificate is enough?Anonymous
July 01, 2015
In conventional client/server environment (2-tier), can we use / embed digital certificates in application to secure the communication, in addition to application layer security? Please guide.Anonymous
July 06, 2015
@Seema.. yes you could.. This is also known as Mutual Auth or Client Certificate Auth. See this: www.iis.net/.../iisclientcertificatemappingauthenticationAnonymous
September 29, 2015
Does Microsoft have any data on percentage of Client Authentication Certificates that break or become corrupt in a Large Organization (10, 000 users to 20,000 users). Currently we have issues with about 1 percent of our user population of about 17, 000 users.Anonymous
April 12, 2016
Thanks@! very usefulAnonymous
September 29, 2016
This helped resolve an issue I was debugging for hours with openssl.Thank you.Anonymous
October 19, 2016
Just awesome topic! Thanks for the info, super helpful. BTW, there is an online service through which you can fill out a TX TREC 37-5, the fillable blank is herehttps://goo.gl/eSDRO6Anonymous
November 30, 2016
Hi and thanks for this article. Old but useful. I would like to extend the question asked by Shah by saying that we have digicert installed on server and i wish to use 1to1 client server mapping. My client is android on which i can embed the client cert in application. How can i get client certificate using digicert. ThanksAnonymous
December 01, 2016
Thanks, nice postAnonymous
February 02, 2017
Very good post Kaushal, thank you very much for sharing.Just one thing isn't clear for me. You told that Enhanced Key Usage is an optional filed. If I have a certificate that does not have this field, is there any problem to use it as a client certificate? Nowadays I use this cert as server certificate, but I also want to use it as Client certificate for some applications.Thanks.Anonymous
March 02, 2017
If i got a normal server ssl certificate for a domain name from AstraGate Domain Services (AGDS), then can I use that certificate as an intermediate certificate and write some of my own certificates for other domain names? Also AGDS provide's an intermediate certificate of their own along with the certificate delivery, and so would I be able to provide the AGDS intermediate cert, the AGDS issued cert (but used as an intermediate also), and the cert I issued for the 2nd domain name to another hosting server where another website is?Anonymous
April 26, 2017
Very well explained about the differences. Thank you Kaushal.Anonymous
July 26, 2017
The comment has been removed