Finally – SMTP Authentication included with SharePoint 2019
Summary
On July 24, 2018 Microsoft has announced the availability of both SharePoint Server 2019 Preview and Project Server 2019 Preview.
One of the features I'm excited about is SMTP Authentication directly from SharePoint. This means, there is no need to setup a standalone SMTP relay just for SharePoint to send outgoing e-mail when authentication is required.
Example: 
Configuration
SMTP Authentication can be configured from Central Admin within the outgoing mail settings.
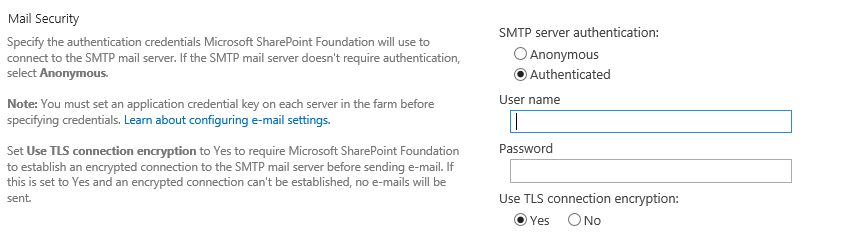
Note: It's recommended to use account credentials that match the From address. If you wish to use credentials for a different account, ensure that account has "Send As" permission to impersonate the From address. Also, if you're using a Windows account to authenticate to the SMTP server, you can specify the user name using either the Universal Principal Name (UPN) format (user@domain.com) or the NT4 login format (DOMAIN\user). If you're using a non-Windows account to authenticate to the SMTP server, contact your email administrator to determine the correct user name format.
However, before storing the password, SMTP authentication requires an application credential key on each SharePoint server in the farm. If the key is not set before attempting to set the authentication, the following error will occur.

To set the application credential key, run the following command on each SharePoint server, where "application credential key" is the password to be used to encrypt and decrypt the SMTP password.
PowerShell Example:
$key = ConvertTo-SecureString -AsPlainText -Force "application credential key"
Set-SPApplicationCredentialKey $key
Repeat the command on each additional SharePoint server in the farm, using the same application credential key.
If you want to remove the application credential key from the local server, use the Remove-SPApplicationCredentialKey cmdlet.
Health Monitoring
Along with the new support for SMTP Authentication, there is also a new Health Rule which check each server (at the server level) to ensure the outgoing email credentials are identical between all servers. If the credential hash is different the following health alert will be displayed.
One or more servers can't retrieve the outgoing email credentials (SharePoint Server 2019)
SharePoint Server 2019
Applies to: SharePoint Server 2019
Summary: Learn how to resolve the SharePoint Health Analyzer rule "One or more servers can't retrieve the outgoing email credentials" for SharePoint Server 2019.
Rule Name: One or more servers can't retrieve the outgoing email credentials.
Summary: At least one web application is configured to use authentication when sending email. There are one or more servers in this farm that can't retrieve the credentials used to authenticate to the outgoing email server. Without credentials, these servers can only send email anonymously.
Cause: The application credential key wasn't found on these servers or they don't have the same application credential key originally used to store the SMTP password. Every server in the farm must have an application credential key to store and retrieve the SMTP password. The application credential key must be identical on each server.
Resolution: Use the Set-SPApplicationCredentialKey command on each failing server to set the application credential key. If the current SMTP password was stored using a different application credential key, you must set the new application credential key on every server in the farm and then save the SMTP credentials again.
Testing Outgoing E-Mail with Authentication
In one my previous blogs, I provided a script to test outgoing e-mail from SharePoint using PowerShell.
Once SMTP Authentication is configured from outgoing e-mail, the script will use authentication.
If the script just reports "It Worked..Congrats! " , how can one be sure it really worked?

One easy method is to use a network trace tool and analyze the SMTP conversation.
Note: If you are using TLS to encrypt the traffic, this will not work unless you can decrypt from the tool.
Let's see how it looks on the wire:

Oh Wait! Why am I using NTLM? We should be using Kerberos!
Let's look at my outgoing e-mail settings:
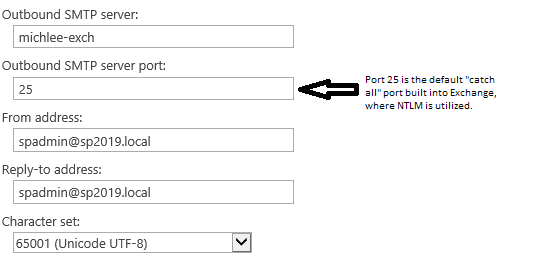
Let's see what the server is telling us when connecting to port 25:

As you can see from above, only NTLM and Anonymous is advertised.
Since Kerberos is more secure and recommend, we should use port 587 from SharePoint, this is where anonymous is disabled, authentication is required and Kerberos is preferred.

Now let's look at what the server advertises from port 587:

As you can see, GSSAPI (Kerberos) is offered with NTLM and Anonymous is no longer displayed.
Now Let's see how it looks on the wire:

Great News! Now we have proved that SharePoint is using SMTP Auth and Kerberos, all looks good!
Bonus Reading for Exchange Online Users
Since many customers use Exchange Online as their primary E-mail Server now, you may no longer have an on-prem Exchange Server. If this is the case, you in luck because SharePoint 2019 Server will support sending outgoing e-mail to your Exchange Online tenant using the "smtp.office365.com" relay.
Let's see how to the outgoing e-mail config will look in this case.

There are a few different ways to make this work. Please see the following article for more options if the recommended scenario does not work.
How to set up a multifunction device or application to send email using Office 365
Comments
- Anonymous
July 26, 2018
thank you - Anonymous
August 09, 2018
Some background on those ports-the default SMTP port 25 is used for server to server SMTP traffic which is usually anonymousthe port 587 is an authenticated mail submission port made for client to server submission of SMTP emailThe authentication methods advertised are configurable although the ones shown above are the default. - Anonymous
February 06, 2019
Thanks very much :))