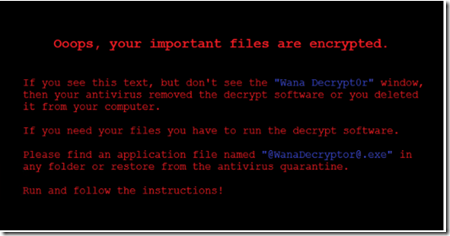
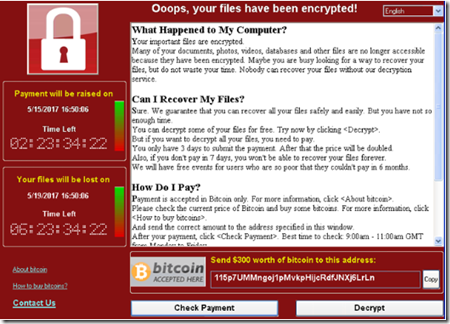
“WannaCrypt”–Patch first and then verify depreciation of SMBv1
Due to ongoing “WannaCrypt” attacks highly recommended to review if you rely on SMBv1, this feature is installed by default but mostly not in use anymore. WannaCrypt threat uses publicly available exploit code for the patched SMB vulnerability, CVE-2017-0145, which can be triggered by sending a specially crafted packet to a targeted SMBv1 server. The exploit code used is designed to work only against unpatched Windows 7 and Windows Server 2008 (or earlier OS) systems, so Windows 10 PCs are not affected by this exploit attack. The said vulnerability was fixed in security bulletin MS17-010, which was released on March 14, 2017
“WannaCrypt” Attacks - If you have automatic updates enabled or have installed the update, your systems are protected against this attack. We encourage to install the update as soon as possible
Please check out below guidelines:
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
https://blogs.technet.microsoft.com/mmpc/2016/05/18/the-5ws-and-1h-of-ransomware/
MS17-010 for Windows 2012 R2 – KB4012216 direct download here
MS17-010 for Windows 2016 – KB4013429 direct download here
You can verify what SMB version your servers are using with “Get-SmbConnection | fl Servername,Dialect”
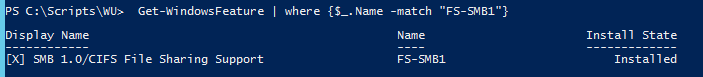
if you want to uninstall SMBv1 you can do this by running below command but you should verify first
Get-WindowsFeature | where {$_.Name -match "FS-SMB1"} | Remove-WindowsFeature
if you want to remove that on a bunch of servers a.e. in a cluster you do something like this
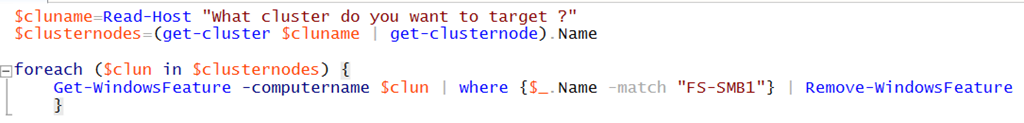
Here is some more guidance on how to enable/disable a specific SMB version –> https://support.microsoft.com/en-us/help/2696547/how-to-enable-and-disable-smbv1,-smbv2,-and-smbv3-in-windows-vista,-windows-server-2008,-windows-7,-windows-server-2008-r2,-windows-8,-and-windows-server-2012
https://blogs.technet.microsoft.com/filecab/2016/09/16/stop-using-smb1/
Stay secured!
Ramazan