クイック スタート: クラスターを構成する
このクイック スタートでは、Azure IoT Operations クラスターで次のリソースを構成します。
- パン屋のオーブンをシミュレートするシミュレートされた OPC PLC サーバーへの接続を定義する "資産エンドポイント"。
- オーブンを表し、オーブンで公開されるするデータ ポイントを定義する "資産"。
- シミュレートされたオーブンからのメッセージを操作する "データフロー"。
資産とは、物理デバイス、または、デバイス、マシン、システム、またはプロセスを表す論理エンティティです。 たとえば、物理資産には、ポンプ、モーター、タンク、生産ラインなどがあります。 定義する論理資産には、プロパティがあったり、テレメトリをストリーミングしたり、イベントを生成したりする可能性があります。
OPC UA サーバーは、資産と通信するソフトウェア アプリケーションです。 OPC UA タグは、OPC UA サーバーが公開するデータ ポイントです。 OPC UA タグは、資産のステータス、パフォーマンス、品質、状態に関する、リアルタイムまたは履歴データを提供できます。
このクイック スタートでは、Bicep ファイルを使用して Azure IoT Operations インスタンスを構成します。
前提条件
Kubernetes クラスターに展開された Azure IoT Operations のインスタンスがあること。 「クイック スタート: K3s を使用して GitHub Codespaces で Azure IoT Operations を実行する」では、クイックスタートに使用できる Azure IoT Operations インスタンスを展開するシンプルな手順を説明しています。
特に明記されていない限り、このクイックスタートのコンソール コマンドは Bash または PowerShell 環境で実行できます。
どのような問題が解決されますか?
OPC UA サーバーが公開するデータは複雑な構造になっている可能性があり、理解が困難な場合があります。 Azure IoT Operations では、OPC UA 資産をタグ、イベント、プロパティとしてモデル化する方法が提供されます。 このモデル化により、データを理解することと、それを MQTT ブローカーやデータフローなどのダウンストリーム プロセスで使用することがより簡単になります。 データフローを使用すると、データを操作して Azure Event Hubs などのクラウド サービスにルーティングできます。 このクイック スタートでは、データフローでペイロード内の一部のフィールドの名前が変更され、メッセージに資産 ID が追加されます。
OPC PLC シミュレーターをデプロイする
このクイックスタートでは、OPC PLC シミュレーターを使用してサンプル データを生成します。 OPC PLC シミュレーターをデプロイするには、次のコマンドを実行します。
kubectl apply -f https://raw.githubusercontent.com/Azure-Samples/explore-iot-operations/main/samples/quickstarts/opc-plc-deployment.yaml
注意事項
この構成では、自己署名アプリケーション インスタンス証明書を使用します。 運用環境では、この構成を使わないでください。 詳細については、「OPC UA 用コネクタの OPC UA 証明書インフラストラクチャを構成する」を参照してください。
環境変数を設定する
Codespaces 環境を使用している場合は、必要な環境変数は既に設定されているため、この手順をスキップできます。 それ以外の場合、シェルで次の環境変数を設定します。
# Your subscription ID
SUBSCRIPTION_ID=<subscription-id>
# The name of the resource group where your Kubernetes cluster is deployed
RESOURCE_GROUP=<resource-group-name>
# The name of your Kubernetes cluster
CLUSTER_NAME=<kubernetes-cluster-name>
クラスターを構成する
次のコマンドを実行して、Azure IoT Operations インスタンスを構成する Bicep ファイルをダウンロードして実行します。 Bicep ファイル:
- OPC PLC シミュレーターに接続する資産エンドポイントを追加します。
- オーブンを表し、オーブンで公開されるデータ ポイントを定義する資産を追加します。
- シミュレートされたオーブンからのメッセージを操作するデータフローを追加します。
- データを受信する Azure Event Hubs インスタンスを作成します。
wget https://raw.githubusercontent.com/Azure-Samples/explore-iot-operations/main/samples/quickstarts/quickstart.bicep -O quickstart.bicep
AIO_EXTENSION_NAME=$(az k8s-extension list -g $RESOURCE_GROUP --cluster-name $CLUSTER_NAME --cluster-type connectedClusters --query "[?extensionType == 'microsoft.iotoperations'].id" -o tsv | awk -F'/' '{print $NF}')
AIO_INSTANCE_NAME=$(az iot ops list -g $RESOURCE_GROUP --query "[0].name" -o tsv)
CUSTOM_LOCATION_NAME=$(az iot ops list -g $RESOURCE_GROUP --query "[0].extendedLocation.name" -o tsv | awk -F'/' '{print $NF}')
az deployment group create --subscription $SUBSCRIPTION_ID --resource-group $RESOURCE_GROUP --template-file quickstart.bicep --parameters clusterName=$CLUSTER_NAME customLocationName=$CUSTOM_LOCATION_NAME aioExtensionName=$AIO_EXTENSION_NAME aioInstanceName=$AIO_INSTANCE_NAME
構成の確認
Bicep ファイルでは、次のリソースを構成しました。
- OPC PLC シミュレーターに接続する資産エンドポイント。
- オーブンを表し、オーブンで公開されるデータ ポイントを定義する資産。
- シミュレートされたオーブンからのメッセージを処理する 2 つのデータフロー。
- データフローの宛先ハブを含む Azure Event Hubs 名前空間。
資産エンドポイント、資産、およびデータフローを表示するには、ブラウザーで操作エクスペリエンス UI に移動し、Microsoft Entra ID 資格情報でサインインします。 新しい展開を使用しているため、サイトはまだありません。 前のクイックスタートで作成したクラスターは、[View unassigned instances] (未割り当てインスタンスの表示) を選択して見つけることができます。 操作エクスペリエンスで、インスタンスは Azure IoT Operations をデプロイしたクラスターを表します。
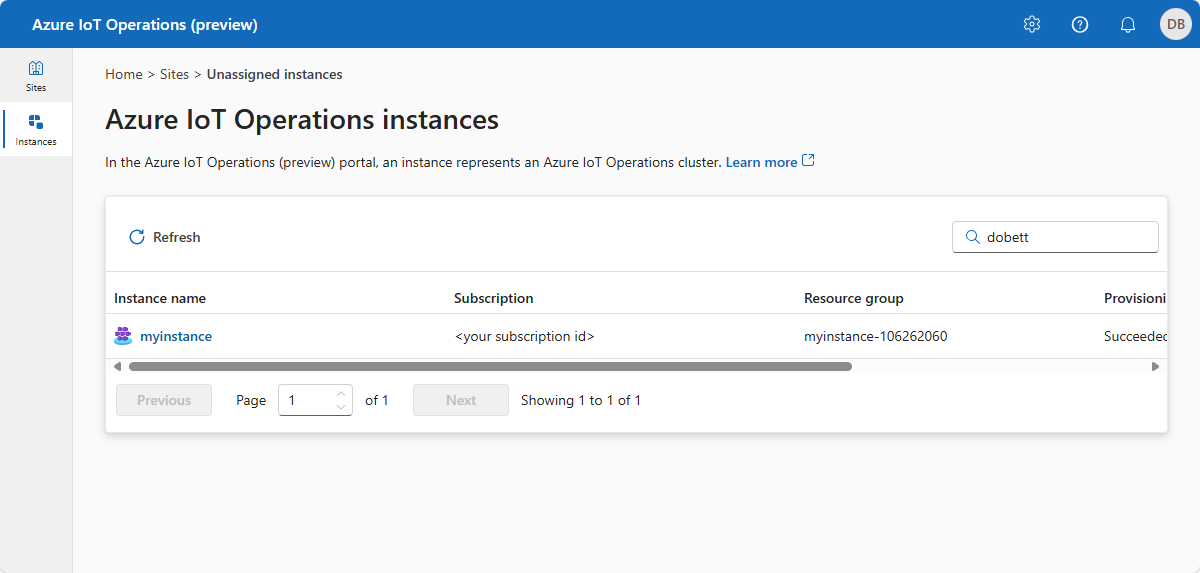
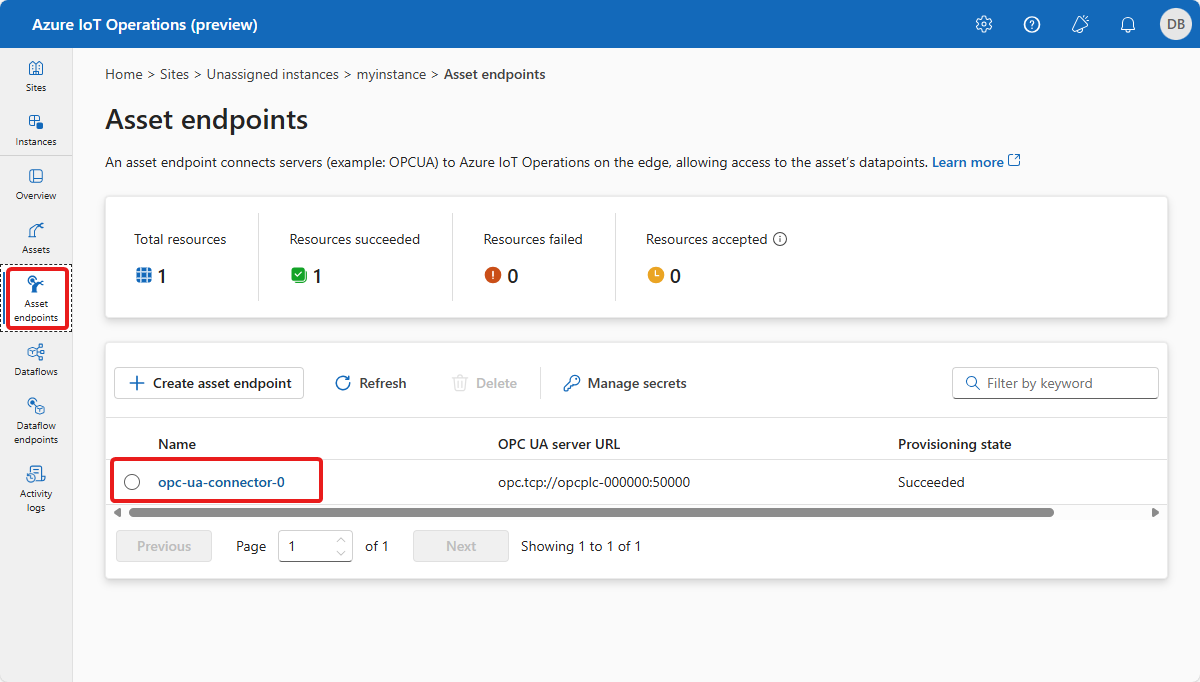
資産エンドポイントでは、OPC PLC シミュレーターへの接続を定義します。
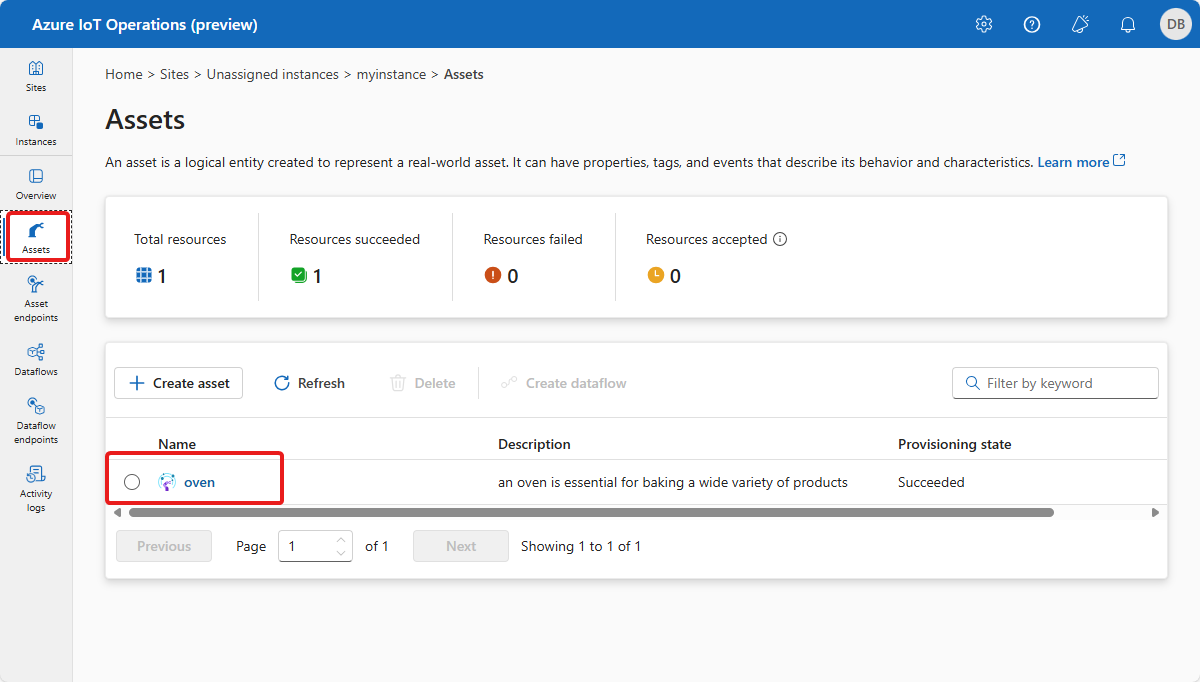
オーブン資産では、オーブンで公開されるデータポイントを定義します。
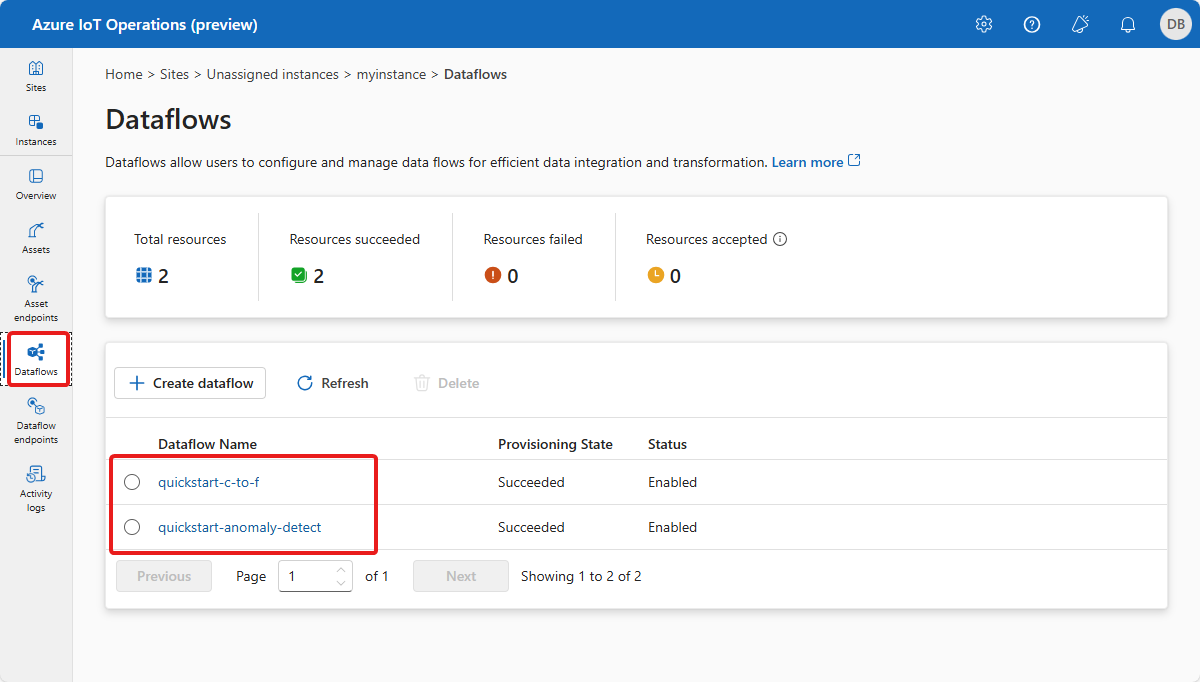
データフローでは、シミュレートされたオーブンからのメッセージを処理し、クラウド内の Event Hubs にルーティングする方法を定義します。
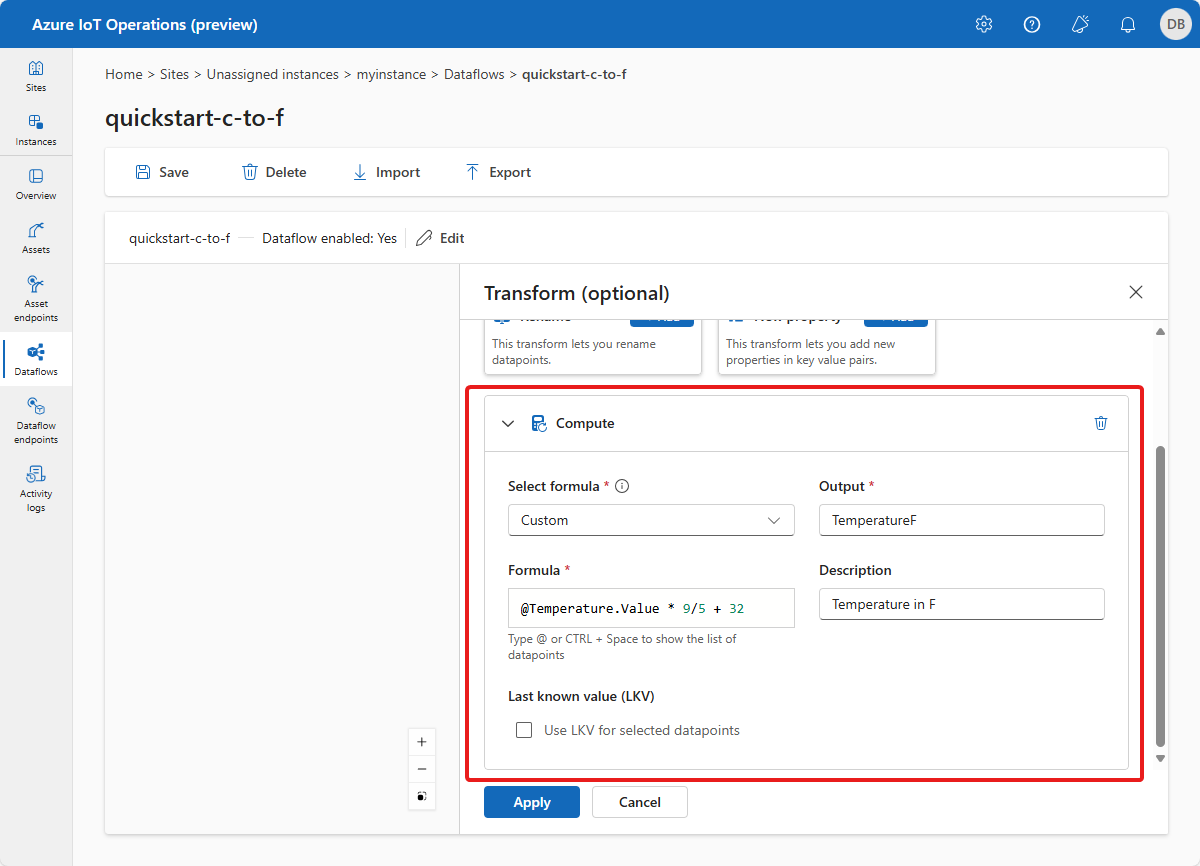
次のスクリーンショットは、温度変換データフローの構成方法を示しています。
データが Event Hubs に送信されていることを確認する
データがクラウドに流れていることを確認するには、Azure portal で Event Hubs インスタンスを表示できます。 データフローが開始され、メッセージがイベント ハブに送信されるまで数分待つことが必要な場合があります。
以前に適用した Bicep 構成では、データフローによって宛先として使用される Event Hubs 名前空間とハブを作成しました。 名前空間とハブを表示するには、Azure portal で、IoT Operations インスタンスを含むリソース グループに移動し、Event Hubs 名前空間を選択します。
メッセージがインスタンスに流れている場合、インスタンスの [概要] ページで受信メッセージの数を確認できます。
![受信メッセージ数が表示された Event Hubs インスタンスの [概要] ページを示すスクリーンショット。](media/quickstart-configure/incoming-messages.png)
メッセージが流れている場合、[データ エクスプローラー] を使用してメッセージを表示できます。
![Event Hubs インスタンスの [データ エクスプローラー] ページのスクリーンショット。](media/quickstart-configure/event-hubs-data-viewer.png)
ヒント
メッセージを表示するには、Event Hubs 名前空間の Azure Event Hubs データ受信者ロールを自分に割り当てる必要があります。
問題をどのように解決したか。
このクイック スタートでは、bicep ファイルを使用し、資産エンドポイント、資産、データフローを使って Azure IoT Operations インスタンスを構成しました。 この構成では、データを処理し、シミュレートされたオーブンからルーティングします。 構成のデータフローでは、メッセージを Azure Event Hubs インスタンスにルーティングします。
リソースをクリーンアップする
次のクイックスタートに進む場合は、すべてのリソースを保持してください。
Azure IoT Operations デプロイは削除するが、クラスターは保持する場合は、az iot ops delete コマンドを使用します。
az iot ops delete --cluster $CLUSTER_NAME --resource-group $RESOURCE_GROUP
このクイックスタート用に作成したすべてのリソースを削除する場合は、Azure IoT Operations をデプロイした Kubernetes クラスターを削除した後、そのクラスターを含んでいた Azure リソース グループを削除します。
これらのクイックスタートで Codespaces を使った場合は、GitHub から Codespace を削除します。
次のステップ
Microsoft Fabric ダッシュボードを構築してオーブン データから分析情報を取得する方法を学習する場合は、「チュートリアル: 処理されたデータから分析情報を取得する」を参照してください。