Examine the principles and components of the Zero Trust model
Zero Trust is a security strategy. Instead of assuming everything behind the corporate firewall is safe, the Zero Trust model assumes every request is a potential breach. As such, organizations must verify every request as though it originates from an open network. Regardless of where the request originates or what resource it accesses, Zero Trust teaches us to “never trust, always verify.” Every access request is fully authenticated, authorized, and encrypted before granting access. The Zero Trust model applies microsegmentation and least privileged access principles to minimize lateral movement. It uses rich intelligence and analytics to detect and respond to anomalies in real time.
Zero Trust principles
The underlying principles that provide the foundation of the Zero Trust model include:
- Verify explicitly. Always authenticate and authorize based on all available data points. For example, user identity, location, device health, service or workload, data classification, and anomalies.
- Use least privileged access. Limit user access with just-in-time (JIT) and just-enough-access (JEA), risk-based adaptive policies, and data protection to help secure both data and productivity.
- Assume breach. Minimize blast radius for breaches and prevent lateral movement by segmenting access by network, user, devices, and app awareness. Verify all sessions are encrypted from start to finish. Use analytics to get visibility and drive threat detection and improve defenses.
Zero Trust components
The Zero Trust security model adapts to the complexities of the modern work environment. It embraces the mobile workforce and protects people, devices, applications, and data, regardless of location. A Zero Trust approach should extend throughout the entire digital estate. It should also serve as an integrated security philosophy and end-to-end strategy. The Zero Trust model accomplishes these goals by implementing controls and technologies across six foundational elements. Each of these elements is a source of signal, a control plane for enforcement, and a critical resource. Given the importance of these foundational elements, it's essential that organizations defend them.
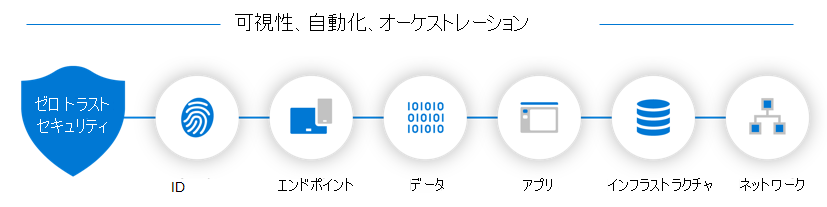
Different organizational requirements, existing technology implementations, and security stages all affect how an organization should plan its Zero Trust security model implementation. Microsoft developed the Zero Trust model based on its experience in helping customers secure their organizations, and after implementing the Zero Trust model throughout its entire enterprise. In doing so, Microsoft developed the following guidance to help organizations assess their readiness and build a plan to get to Zero Trust:
Secure identities with Zero Trust. Identities—whether they represent people, services, or IoT devices—define the Zero Trust control plane. When an identity attempts to access a resource, verify that identity with strong authentication, and ensure access is compliant and typical for that identity. Follow least privilege access principles.
Secure endpoints with Zero Trust. Once an identity obtains access to a resource, data can flow to various different endpoints, from:
- IoT devices to smartphones
- BYOD to partner-managed devices
- on-premises workloads to cloud-hosted servers
This diversity creates a massive attack surface area. Monitor and enforce device health and compliance for secure access.
Secure applications with Zero Trust. Applications and APIs provide the interface by which organizations consume data. These applications and APIs might be legacy on-premises, lifted-and-shifted to cloud workloads, or modern SaaS applications. Organizations should apply controls and technologies to:
- discover shadow IT
- ensure appropriate in-app permissions
- ensure gate access based on real-time analytics
- monitor for abnormal behavior
- control user actions
- validate secure configuration options
Secure data with Zero Trust. Ultimately, security teams protect data. Where possible, data should remain safe even if it leaves the devices, apps, infrastructure, and networks the organization controls. Classify, label, and encrypt data, and restrict access based on those attributes.
Secure infrastructure with Zero Trust. Infrastructure—whether on-premises servers, cloud-based VMs, containers, or micro-services—represents a critical threat vector. Assess for version, configuration, and JIT access to harden defense. Use telemetry to detect attacks and anomalies, and automatically block and flag risky behavior and take protective actions.
Secure networks with Zero Trust. Organizations ultimately access all data over their network infrastructure. Networking controls provide critical controls to enhance visibility and help prevent attackers from moving laterally across the network. Segment networks (and do deeper in-network micro-segmentation) deploy real-time threat protection, end-to-end encryption, monitoring, and analytics.
With Zero Trust, organizations move away from a trust-by-default perspective to a trust-by-exception one. An integrated capability to automatically manage those exceptions and alerts is important. It enables organizations to more easily:
- find and detect threats
- respond to them
- prevent or block undesired events across their business
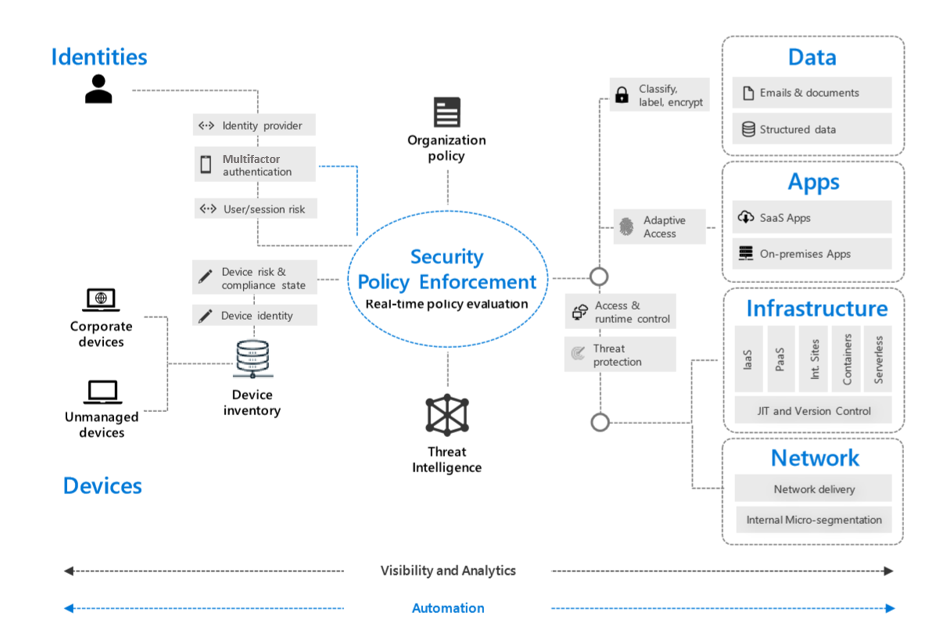
Additional reading. For more information on Zero Trust security, see the Zero Trust maturity model.
Knowledge check
Choose the best response for the following question. Then select “Check your answers.”