Configure ADFS and Device Registration service in Windows 2012 R2
Installing ADFS federation server:
In the previous blogs we looked at the different new features in ADFS in Windows 2012 R2 and the installation requirements.
In this article we will look at the installation of ADFS service and enabling Device Registration service in Windows 2012 R2.
Installing ADFS federation server:
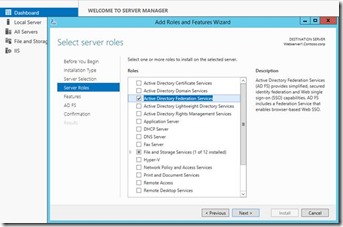
1. Install the ADFS role service from Windows Server manager. In Windows 2012 R2 you can remotely install the roles on server.
2. Click Next > Next > Next > Install to install the ADFS role.
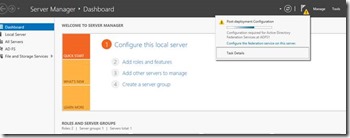
3. Go to the server manager notification and click on Configure the ADFS service
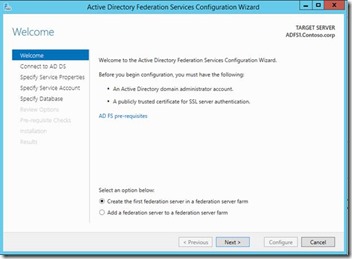
4. Make sure the requirements given in the below screenshot are met before you proceed to next step. Select whether this is the first federation server in a federation server farm or a new server in existing federation farm.
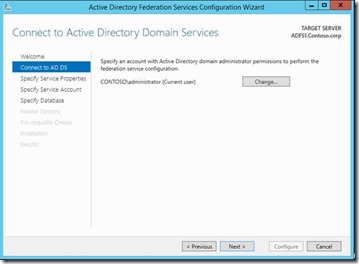
3. Provide the credentials for domain admin account to configure ADFS service as mentioned below:
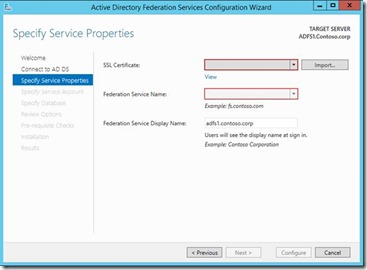
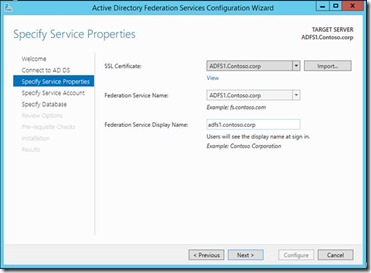
4. Select the ADFS certificate which is installed on the ADFS server. Obviously the federation service name should be same as the name used in the ADFS certificate.
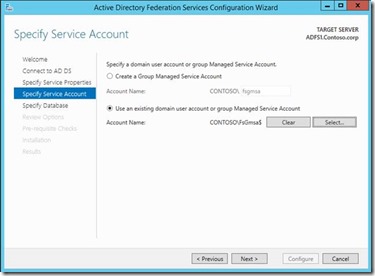
5. Here you can specify a domain user account or Group Managed Service Account. Group Managed Service Account (GMSA) is a new feature in Windows 2012, which is an improvement to the managed service account in Windows 2008 R2. GMSA are managed domain accounts that provide automatic password management and simplified SPN management, including delegation of management to other administrators. The group Managed Service Account provides the same functionality within the domain but also extends that functionality over multiple servers.
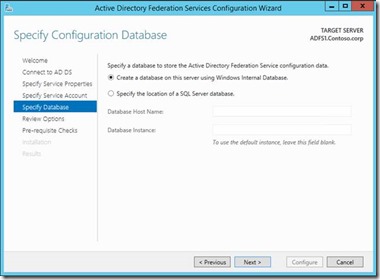
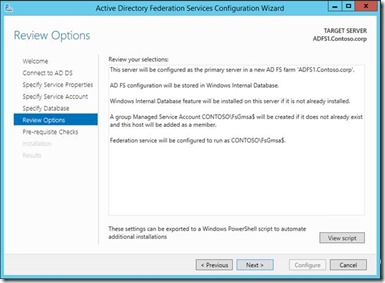
6. You can select a SQL server database or the Windows internal database to host the ADFS configuration database
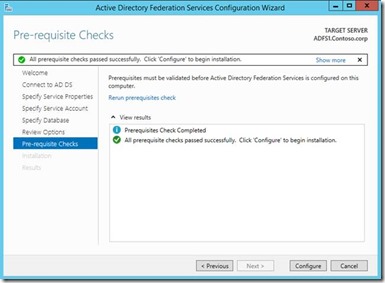
7. Click configure and that finishes the ADFS configuration.
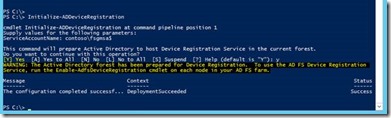
8. There are few additional steps to enable the Device registration service:
Initialize the ADDeviceRegistration service on ADFS server
Enabled the ADFS Device Registration service
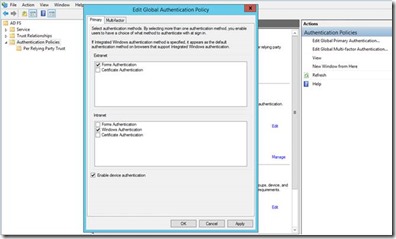
Enable device authentication in ADFS management console:
You can try the following methods to test the functionality of ADFS service:
https://adfs1.contoso.com/federationmetadata/2007-06/federationmetadata.xml - this should return the metadata xml file
https://adfs1.contoso.com/adfs/ls/idpinitiatedsignon.aspx - This should return the ADFS login page
In Next section we will look at the Web Application Proxy which has replaced the ADFS Proxy service role in Windows 2012 R2. We will also look at publishing DRS via WAP.
Comments
- Anonymous
May 07, 2014
screens missing:( - Anonymous
May 08, 2014
Pingback from Configure Web Application Proxy server and publish Device Registration service in Windows 2012 R2 | MS Tech BLOG - Anonymous
May 08, 2014
Pingback from Configure Web Application Proxy server and publish Device Registration service in Windows 2012 R2 | MS Tech BLOG - Anonymous
November 22, 2014
The comment has been removed - Anonymous
November 24, 2014
@Taparshi - thanks for the feedback. Some of the points (CNAME pointing to ADFS server, ADFS / DRS service certificate names ) you highlighted are mentioned in the previous article however I dint add any screenshots for the same as those are pretty generic - http://blogs.technet.com/b/amitd/archive/2014/04/18/adfs-new-features-and-prerequisites-in-windows-2012-r2.aspx. Additionally other points you mentioned are good to know and can really be handy when it comes to troubleshooting. - Anonymous
December 29, 2014
Great Article. Anyone know if we use an ADFS farm based on WID DB replication, can clients authenticate if the primary ADFS server is down for maintenance and none of the secondary's are promoted to primary. I know configuration changes such as adding relying party trusts will not work, but am unsure if normal client authentication is impacted as well? - Anonymous
February 19, 2015
@Amit - In that case Secondary servers will continue to process the requests as normal however as you rightly mentioned you wont be able to make any new changes to the ADFS configuration database unless you designate other server as the Primary or bring back the primary server. Primary server holds the Read / Write copy of the ADFS configuration database in WID farm configuration. Secondary servers hold the read only copy of the database that they synchronize with the primary server. - Anonymous
March 16, 2015
The comment has been removed - Anonymous
March 17, 2015
Hi Isaac - As mentioned here - https://technet.microsoft.com/en-us/library/dn614658.aspx the CNAME record must use the well-known prefix EnterpriseRegistration followed by the UPN suffix used by the user accounts at your organization. All clients are going to use this well known prefix followed by their UPN suffix to discover the service so as long as you have this service published for one of the ADFS farm and containing the client UPN suffixes, clients should be able to discover the service fine. - Anonymous
April 06, 2015
As an Identity PFE I’ve seen my fair share of ADFS Admin logs. In many cases that log is a good - Anonymous
April 07, 2015
As an Identity Hybrid PFE I’ve seen my fair share of ADFS Admin logs. In many cases that log is - Anonymous
December 28, 2015
Hi there
What if i need to configure more than one UPN suffix root domain? by example: i have many upn suffixes with the customers domain:
@company-one.net
@company-two.com
any idea how to handle device registration in this shared environment?
best regards mike