How to make use of a custom IP-STS with SharePoint 2010? (Part 1)
I know there have already been many articles about how to make SharePoint work with ADFS 2.0, like the one from SPIdentity team blog and the one by Eric Kraus. What I want to do is to create a simple IP-STS and make use of it in SharePoint 2010 rather than ADFS 2.0, so that when I show customers the whole idea of claim based authentication in SharePoint 2010, I can focus on SharePoint itself instead of introducing them how ADFS 2.0 works.
So here comes the whole story of what I have done.
Preparing IP-STS
First of all, I created a very simple IP-STS web site based on the Asp.Net Security Token Service Web Site template which came from WIF SDK. I didn’t even make any change to its out-of-box code. The only thing I added was the certificate information in web.config.
A normal IP-STS usually needs two certs, signing cert and encrypting cert. The encrypting cert is used to encrypt the security token issued by the STS. In web.config of the STS web site, they are defined by the following app settings.
<appSettings>
<add key="IssuerName" value="SimpleSTS"/>
<add key="SigningCertificateName" value="CN=DevBox"/>
<add key="EncryptingCertificateName" value="CN=DevBox"/>
</appSettings>
To make things simple, I used a single cert here for both signing and encrypting. If you want to build a production level STS, you should use different certs for them.
To make sure the IP-STS works normally, I also built a simple Asp.Net web site to use its claims. The Url of my STS is: https://devbox/simplests/.
Make use of my IP-STS in SharePoint 2010
I used the following PowerShell commands to register my IP-STS as a trusted identity provider in SharePoint 2010. They are almost the same with the commands used in ADFS 2.0 samples.
$cert = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2("c:\signing.cer")
$map1 = New-SPClaimTypeMapping -IncomingClaimType "https://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress" -IncomingClaimTypeDisplayName "EmailAddress" –SameAsIncoming
$map2=New-SPClaimTypeMapping -IncomingClaimType "https://schemas.microsoft.com/ws/2008/06/identity/claims/role" -IncomingClaimTypeDisplayName "Role" –SameAsIncoming
$realm=”https://claimauthweb/_trust/default.aspx”
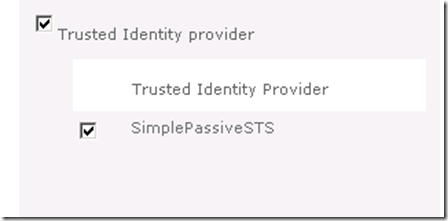
$ap=New-SPTrustedIdentityTokenIssuer -Name "SimplePassiveSTS" -Description "A simple Asp.Net STS on DevBox." –Realm $realm -ClaimsMappings $map1,$map2 -ImportTrustCertificate $cert -SignInUrl "https://devbox/SimpleSTS/default.aspx" -IdentifierClaim $map1.InputClaimType
The default Asp.Net STS template generates the following two types of claims.
- https://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
- https://schemas.microsoft.com/ws/2008/06/identity/claims/role
The first one cannot be mapped in SharePoint 2010 because it is a reserved claim type. That is why I modified the output claims of my STS and used the very common emailaddress type.
Another thing worth mentioning is the $realm. This field is used by STS to determine the ReplayToAddress of the Relying Party. In ADFS 2.0 samples, usually this field was set to: $realm = "urn:" + $env:ComputerName + ":Geneva". I believe ADFS 2.0 knows how to handle this realm if it comes from SharePoint 2010. My STS does not understand the realm like this. So I simply used https://claimauthweb/_trust/default.aspx for realm so that my STS can reply to this address directly.
https://claimauthweb/ was an existing SharePoint web app with Claim mode authentication enabled. Now I can simply choose to use the trusted identity provider I registered in Central Administration.
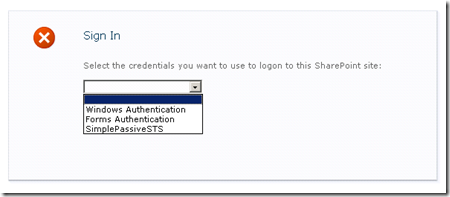
Now everything looks good. When I browse to https://claimauthweb, I can see the following sign-in options.
Guess what will happen if I choose SimplePassiveSTS? Can I pass the authentication and access the SharePoint site? The answer will in the Part 2 of this series.
Comments
Anonymous
May 25, 2010
I'm trying to set up a passive STS for one of my SP 2010 sites. I was able to get my STS working for a claims-aware ASP.NET site that I was initially testing with. Then when I switched to SP, I did see the STS show up as a trusted identity provider and I've now got my SP site configured to use it (via your PowerShell cmdlets). I can see users from the STS in the people picker in the SP 2010 site. And when I navigate to the SP 2010 site, it correctly redirects me to my passive STS login page. So far so good...However, when I enter my credentials on the STS login page, one of the following (bad!) things occurs (depending on different configuration tweaks I have attempted):The browser seems to go in an infinite redirection loop. The following link seems to have some useful info on that problem: msdn.microsoft.com/.../ee517298.aspxThe browser just gets redirected back to the STS login page and you have to type in your credentials again, over and over again to no avail. I get an HTTP 500 internal server error, but I don't see any more details in the SP logs or Windows Event Log. Questions for you:Do you have any more guidance on how to troubleshoot these issues (and/or do any of these issues sound familiar)?Where do I look for error log messages or what other diagnostic tools would you recommend? Did you add anything else to the SP site besides issuing the PowerShell cmdlets you list in this blog?(e.g. did you make any changes to the site's web.config, did you add any code/pages into the _trust folder for the SP site, etc) If you did, can you provide a copy of your web.config or code/pages? In general, any help would be greatly appreciated!Thanks,MichaelAnonymous
June 04, 2010
The comment has been removedAnonymous
June 05, 2010
I find an evet raised during this error in Application Events, the event is : An exception occurred when trying to issue security token: The trusted login provider did not supply a token accepted by this farm.Still couldn't find the reason.Note: I am usign SharePoint foundation 2010Anonymous
July 14, 2010
@Michael Tonderum - i had the same problem. Try changing the token cache timeout:#Token Cache Expiration Work-Around :$stsc = Get-SPSecurityTokenServiceConfig$stsc.LogonTokenCacheExpirationWindow = (New-TimeSpan -second 300)$stsc.Update()Anonymous
July 14, 2010
The comment has been removedAnonymous
September 02, 2010
Madnik7 did you got the solution for error you mentioned. I am still struggling with this. Please help me with this.Operation is not valid due to the current state of the objectException Details: System.InvalidOperationException: Operation is not valid due to the current state of the object.Anonymous
September 06, 2010
Madnik7 can you please help me on this?Anonymous
September 13, 2010
Can someone explain what "_trust/Default.aspx" does? Why does this return a 404 when the user is already logged in?Anonymous
December 03, 2010
Thanks for your post!Does anyone have any information on people picker search issues with claims auth?Searching for identities or roles is not working, or perhaps it's working too well (feature?). The people picker returns whatever query was typed in as both a role and a claim. This means that an email search returns both a claim result (c:0-.t|customsts|emailaddress) and an identity result (i:05.t|customsts|emailaddress).Furthermore, there is no verification done, so an incorrect or partial search query will be returned just fine.I know I'm not the only person to have experienced this, but I haven't found any answers from the community.Any ideas? Thanks.Anonymous
December 05, 2010
Yes, by default people picker just returns what you input. You need a custom claims provider to make people picker work for your claims. Please refer to: blogs.technet.com/.../writing-a-custom-claims-provider-for-sharepoint-2010-part-1.aspxAnonymous
July 02, 2011
Very nice post. You can find similar details here alsowww.anmolrehan-sharepointconsultant.com/.../security-token-service-sts-and.htmlAnonymous
July 10, 2011
Thanks for your post. I created my custom IP-STS and it works. My SharePoint site uses both Windows Authentication and Trusted Identity provider. Sometime I need to skip "sign-in options" dialog and automatically choose Trusted Identity provider (SimplePassiveSTS).Is this possible?User will use token parameter in this case: e.g. https://sharepointmachine/default.aspx?token=XL1uRVuvuozpETuWSCdtcQ==Anonymous
June 24, 2014
so. before going into sharepoint you have an asp sts website and asp site to test? asp sts made of the asp sts template and asp site made out of a simple asp site template, right? how do you test you IP-STS is working with the https://devbox/simplests/? what is the url of the asp sts site?