练习 - 管理 Node.js 项目中的依赖项更新
Tailwind Traders 要求你处理某个具有过时依赖项的应用。 该应用很小,只有几个依赖项。 更新代码应该非常简单。 查看是否可以更新应用以利用最新功能。 如果发现任何漏洞,请趁此机会修复。
开始使用
在新的终端窗口中(Ctrl + Shift + `),切换到包含本练习的文件的文件夹:
cd ../7-exercise-dependency-management通过运行以下命令安装依赖项:
npm install应会看到有关已安装的包和任何漏洞的输出。
打开 package.json 文件,查看
dependencies部分:"lodash": "^1.1.0", "node-fetch": "^1.0.2"请注意,模式指定插入 (^) 符,该字符指示对次要版本的更新以支持依赖项:
1.x。打开 index.js 文件,了解如何在应用中使用包依赖项:
const fetch = require('node-fetch') const _ = require('lodash'); const path = require('path'); const fs = require('fs'); async function run() { const response = await fetch("https://dev.to/api/articles?state=rising"); const json = await response.json(); const sorted = _.sortBy(json, ["public_reactions_count"], ['desc']); const top3 = _.take(sorted, 3); const filePrefix = new Date().toISOString().split('T')[0]; fs.writeFileSync(path.join(__dirname, `${filePrefix}-feed.json`), JSON.stringify(top3, null, 2)); } run();此代码使用
node-fetch包从 REST API 中拉取数据。 它会处理响应,先对其进行排序,然后使用lodash包取前三个结果。 结果存储在文件中。
npm 审核
要了解是否存在任何漏洞,请运行以下命令:
npm audit
此时应会看到如下例所示的输出:
# npm audit report
lodash <=4.17.20
Severity: critical
Regular Expression Denial of Service (ReDoS) in lodash - https://github.com/advisories/GHSA-x5rq-j2xg-h7qm
Prototype Pollution in lodash - https://github.com/advisories/GHSA-fvqr-27wr-82fm
Prototype Pollution in lodash - https://github.com/advisories/GHSA-jf85-cpcp-j695
Command Injection in lodash - https://github.com/advisories/GHSA-35jh-r3h4-6jhm
Prototype Pollution in lodash - https://github.com/advisories/GHSA-4xc9-xhrj-v574
Regular Expression Denial of Service (ReDoS) in lodash - https://github.com/advisories/GHSA-29mw-wpgm-hmr9
fix available via `npm audit fix --force`
Will install lodash@4.17.21, which is a breaking change
node_modules/lodash
node-fetch <=2.6.6
Severity: high
The `size` option isn't honored after following a redirect in node-fetch - https://github.com/advisories/GHSA-w7rc-rwvf-8q5r
node-fetch forwards secure headers to untrusted sites - https://github.com/advisories/GHSA-r683-j2x4-v87g
fix available via `npm audit fix --force`
Will install node-fetch@3.3.2, which is a breaking change
node_modules/node-fetch
2 vulnerabilities (1 high, 1 critical)
To address all issues (including breaking changes), run:
npm audit fix --force
输出指出了漏洞和修复问题的包的版本。
Will install lodash@4.17.21, which is a breaking change
Will install node-fetch@3.3.2, which is a breaking change
npm 已过时
在终端中,运行此命令来检查过时的依赖项:
npm outdated
此时应会看到如下例所示的输出:
Package Current Wanted Latest Location Depended by
lodash 1.3.1 1.3.1 4.17.21 node_modules/lodash 7-exercise-dependency-management
node-fetch 1.7.3 1.7.3 3.3.2 node_modules/node-fetch 7-exercise-dependency-management
当前版本和所需版本相同,但最新版本不同。 已满足package.json中指定的语义更新策略,但仍存在漏洞。
npm 更新
编辑
package.json文件以显式允许重大更改修复漏洞,从更重要的包开始:"node-fetch": "^2.6.6"运行以下命令以查看更新将执行的操作:
npm update --dry-runadded 3 packages, removed 4 packages, and changed 1 package in 508ms运行以下命令以基于
package.json更新项目:npm update运行以下命令以查看已修复的
node-fetch的漏洞:npm audit# npm audit report lodash <=4.17.20 Severity: critical Regular Expression Denial of Service (ReDoS) in lodash - https://github.com/advisories/GHSA-x5rq-j2xg-h7qm Prototype Pollution in lodash - https://github.com/advisories/GHSA-fvqr-27wr-82fm Prototype Pollution in lodash - https://github.com/advisories/GHSA-jf85-cpcp-j695 Command Injection in lodash - https://github.com/advisories/GHSA-35jh-r3h4-6jhm Prototype Pollution in lodash - https://github.com/advisories/GHSA-4xc9-xhrj-v574 Regular Expression Denial of Service (ReDoS) in lodash - https://github.com/advisories/GHSA-29mw-wpgm-hmr9 fix available via `npm audit fix --force` Will install lodash@4.17.21, which is a breaking change node_modules/lodash 1 critical severity vulnerability To address all issues (including breaking changes), run: npm audit fix --force如果项目有任何测试,请运行它们以验证更新未中断任何内容。
使用相同的步骤将
lo-dash更新到4.17.20版本,而不会造成漏洞。漏洞已修复,但
node-fetch版本仍然是落后的主要版本。 如果所有测试都通过,请将package.json文件中指定的版本更正为最新版本:"node-fetch": "^3.3.2"然后运行以下命令更新项目:
npm update项目现在应没有 npm 漏洞,并且位于当前主版本上。
签入
package.json和package-lock.json文件。祝贺你! 已更新依赖项并修复项目中的漏洞。
清理开发容器
完成项目后,你可能希望清理开发环境或将其返回到其典型状态。
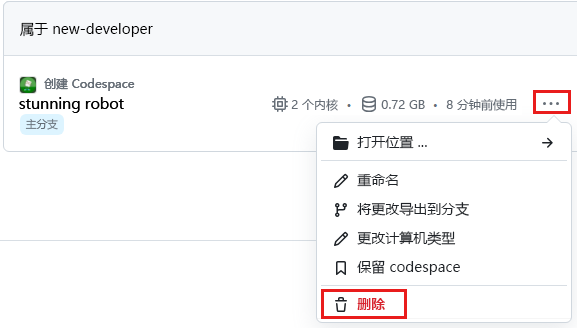
删除 GitHub Codespaces 环境可确保可以最大程度地提高帐户获得的每核心免费小时数权利。
重要
有关 GitHub 帐户权利的详细信息,请参阅 GitHub Codespaces 每月包含的存储和核心小时数。
登录到 GitHub Codespaces 仪表板 (https://github.com/codespaces)。
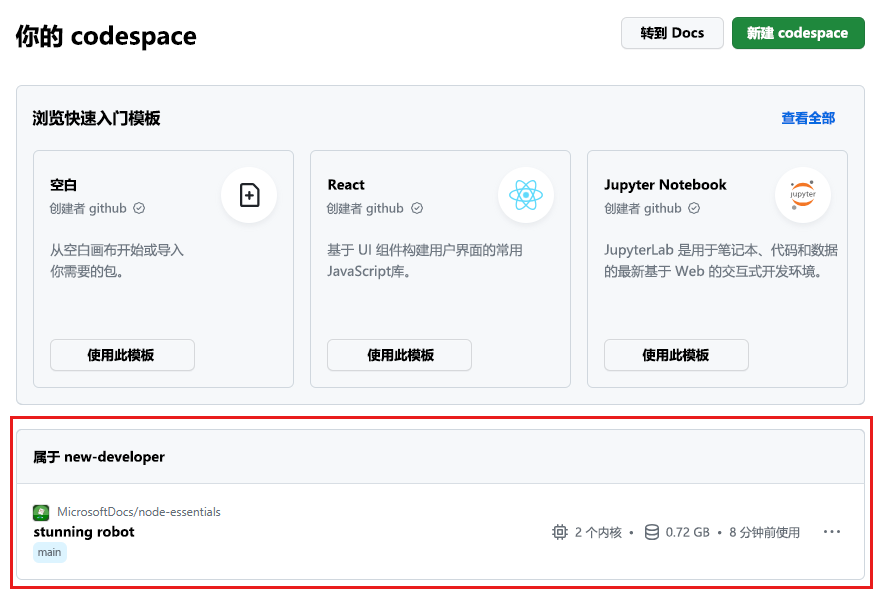
打开 codespace 的上下文菜单,然后选择“删除”。