Foundations of data security and compliance with Microsoft Purview
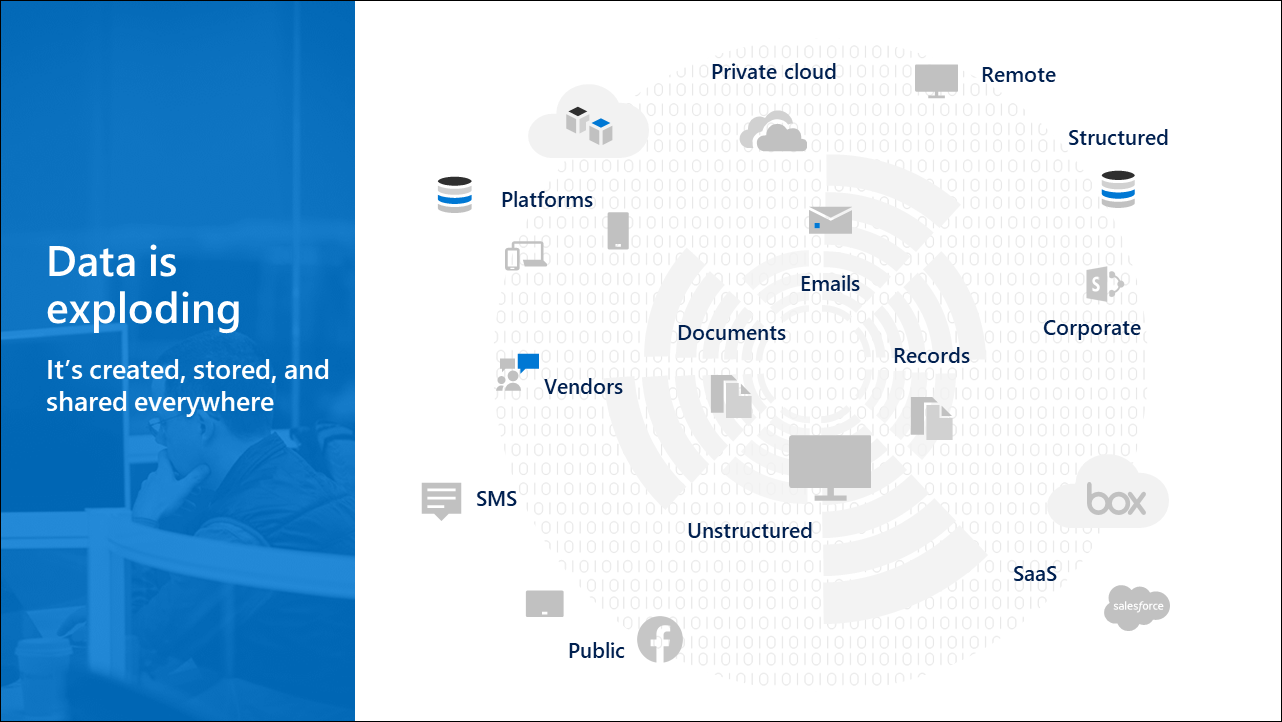
Data is exploding
Data is being created, stored, and shared faster than ever before. By 2025, it's estimated that the world will produce up to 175 zettabytes of data, a tenfold increase from 2016. This rapid growth brings new challenges for organizations trying to manage a wide range of data types, including emails, documents, instant messages, videos, and images. Generative AI adds further complexity by introducing new layers of data and risks like privacy concerns and misinformation.
Organizations must rethink how they manage and secure data to keep up. This involves updating strategies to address the growing volume and complexity of data, and new challenges posed by AI.
Note
1 Zettabyte = 1,000,000 Petabytes
Regulation is increasing
As data grows, so do the demands for protecting it. The need for strong controls around sensitive data is more critical than ever. Without a robust data management strategy, organizations risk financial penalties, reputational damage, and loss of customer trust.
Well-designed data management strategies help reduce these risks and ensure data security in a constantly changing landscape.
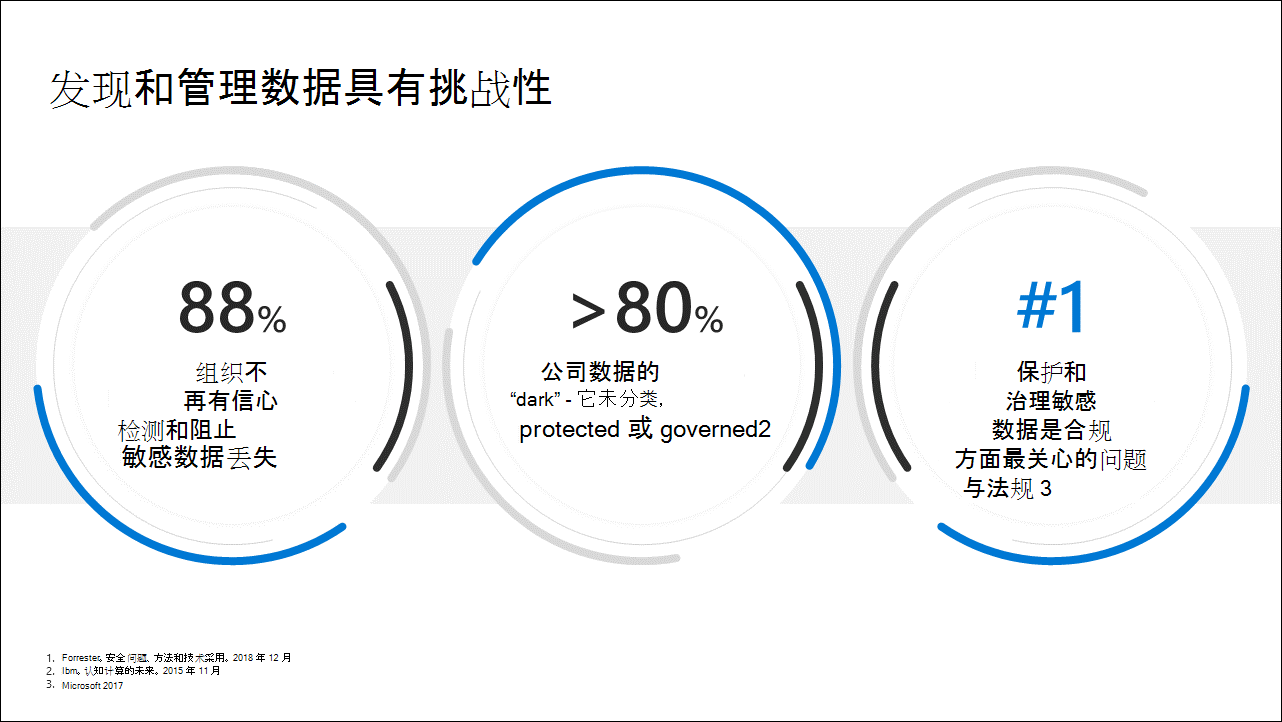
Discovering and managing data is challenging
Managing and protecting data is a growing challenge. Research highlights that:
- 88% of organizations lack confidence in their ability to detect or prevent sensitive data loss.
- More than 80% of corporate data remains "dark", meaning it isn't classified, protected, or governed.
- Protecting and governing sensitive data is one of the biggest challenges for compliance with regulations.
Organizations need to protect sensitive data across devices, SaaS applications, and cloud services. As the environment grows more complex, so do the risks of data breaches and non-compliance.
Defining a data security strategy
Does your organization have a defined strategy for identifying, managing, and securing sensitive data? Many organizations struggle with this, but asking these questions can help set the foundation for success:
- Where is your sensitive data? Understanding where critical data resides often requires a comprehensive review across on-premises and cloud environments.
- Can you control this data wherever it goes? Data often moves across boundaries and is shared with external partners or accessed on personal devices. Ensuring consistent security is key.
- Are you using multiple tools to manage and secure data? Relying on multiple tools can lead to inefficiencies and gaps. A unified approach streamlines data security.
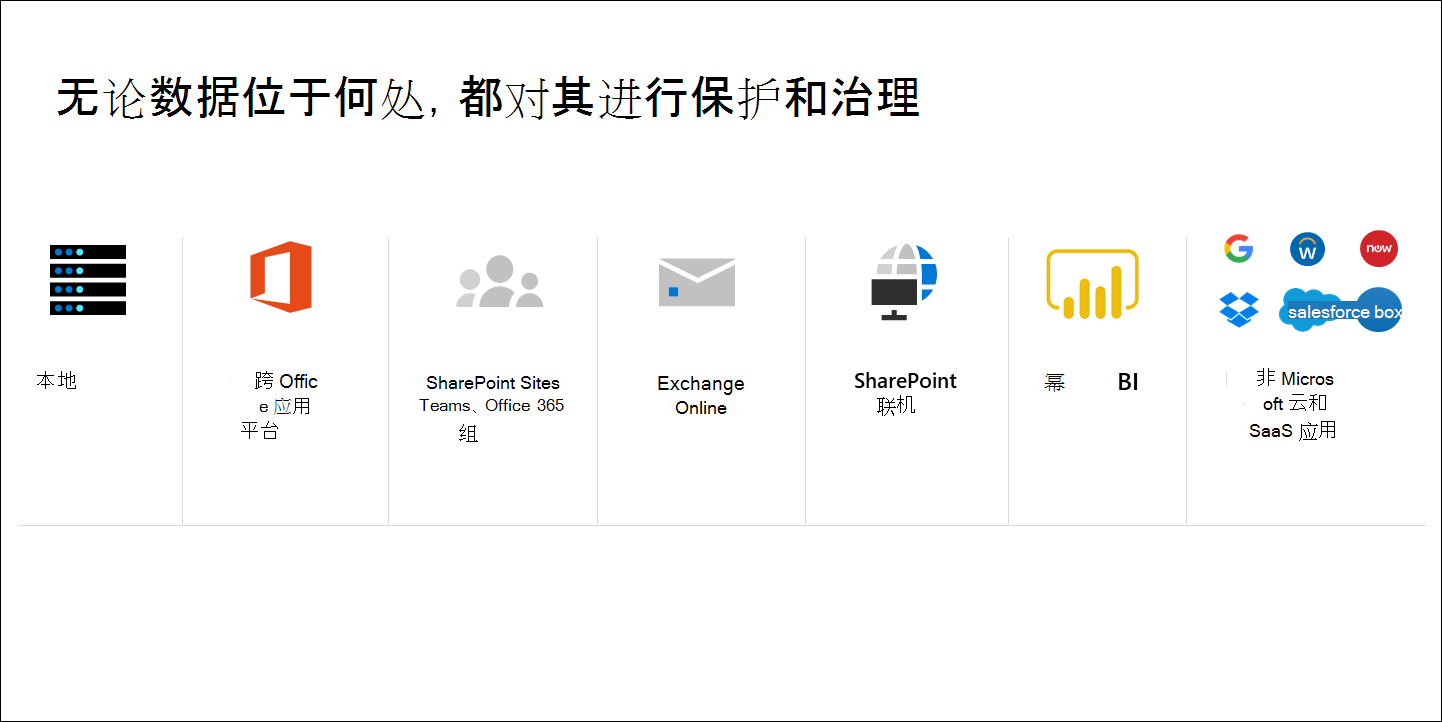
Protect and govern data wherever it lives
Microsoft offers a comprehensive solution for information protection and governance, covering the full data lifecycle across Microsoft 365 services and other environments like non-Microsoft clouds (Dropbox, Salesforce) and on-premises systems. This unified approach ensures consistent classification, labeling, and protection of sensitive data, no matter where it resides.
Unified data discovery and classification
Microsoft takes a unified approach to data discovery and classification across Microsoft 365, Power Platform, non-Microsoft cloud services, and on-premises environments. This offers:
- Consistent classification across devices, apps, and services.
- Deep content scanning with more than 300 built-in sensitive information types.
- Customizable sensitive information types and trainable classifiers for industry-specific needs.
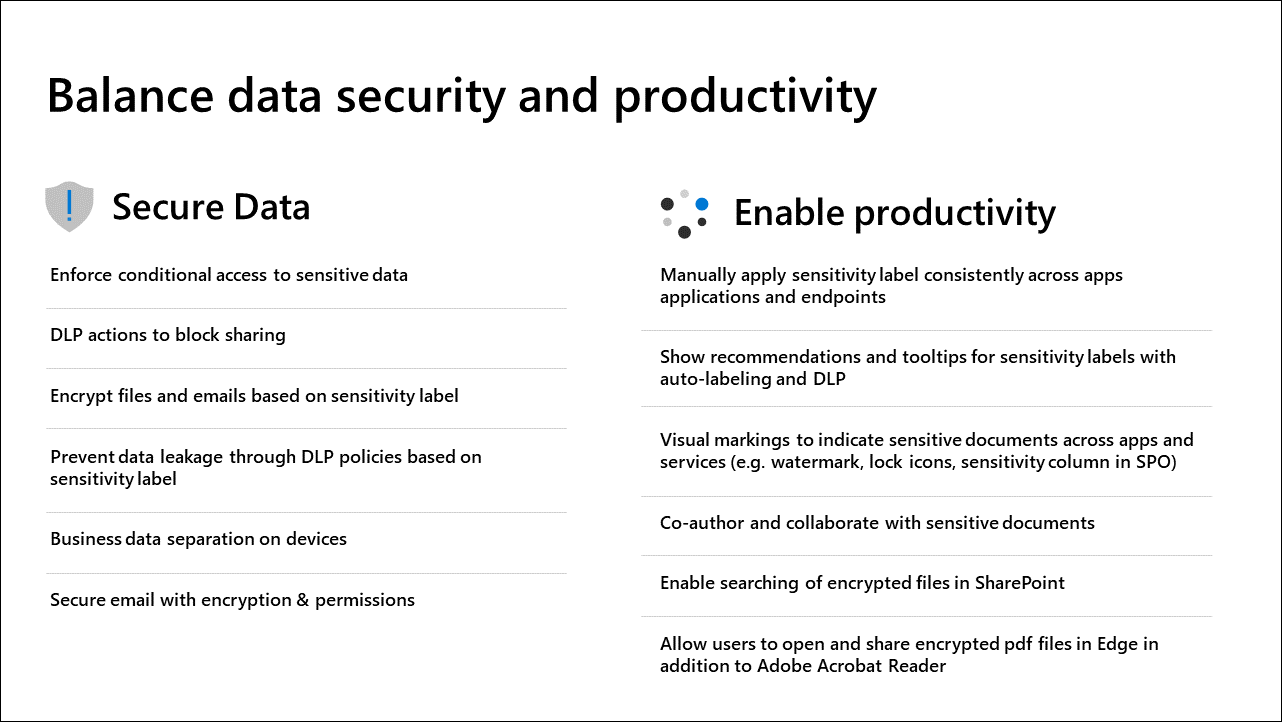
Balance security and productivity
Striking the right balance between security and productivity is essential. While security features like data loss prevention (DLP) and encryption protect sensitive data, users need the ability to collaborate smoothly. Here's how tools support both goals:
Security features:
- Restrict access to sensitive data with conditional access policies based on identity, location, and device compliance.
- Prevent unauthorized sharing with DLP policies across cloud and on-premises platforms.
- Encrypt files and emails based on sensitivity labels, ensuring data protection at rest and in transit.
- DLP to prevent data leakage, ensuring sensitive data isn't accidentally shared or exposed.
- Separate business and personal data on devices, protecting organizational data without intruding on personal data.
- Secure email with encryption and custom permissions to control access and actions like forwarding.
Productivity features:
- Apply sensitivity labels across platforms like Office apps and endpoints for consistent data classification.
- Provide label suggestions and tooltips to help users apply labels appropriately.
- Add visual markings like watermarks and lock icons to indicate sensitive documents.
- Enable secure co-authoring and collaboration across Teams, OneDrive, and SharePoint.
- Search encrypted files within SharePoint without compromising security.
- Open and share encrypted PDFs directly in Microsoft Edge.
The information protection and governance lifecycle
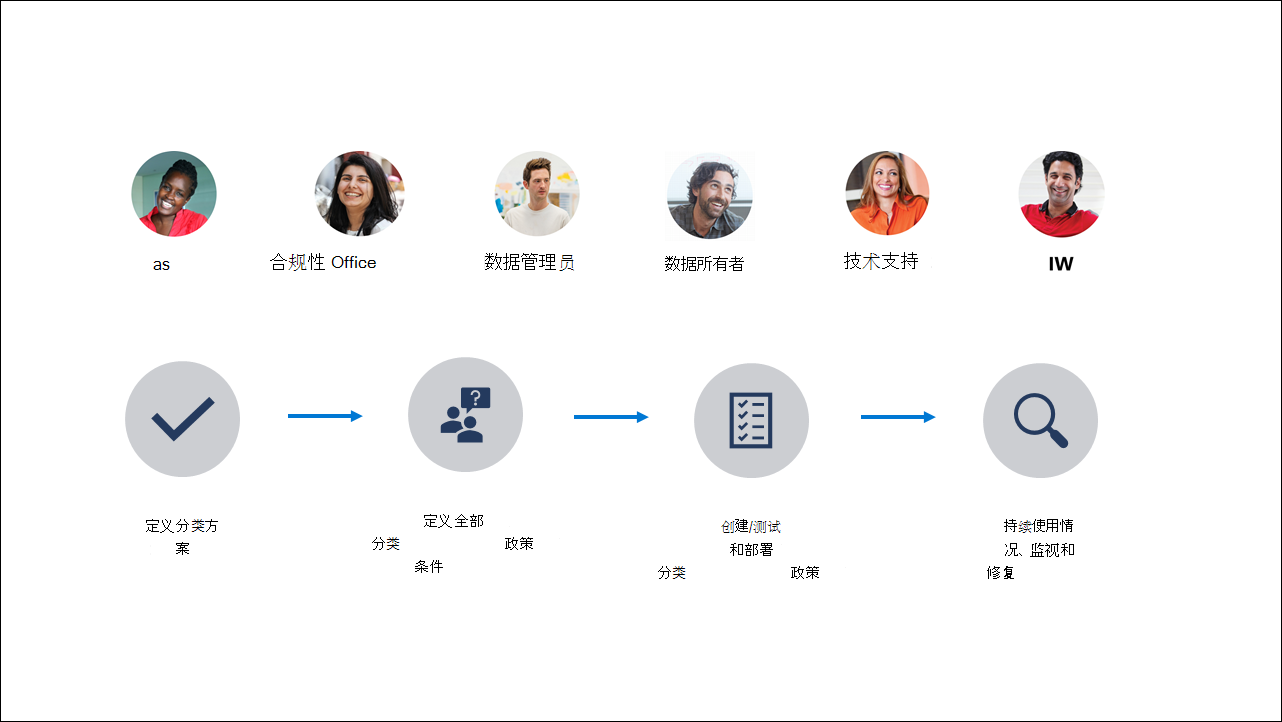
Implementing effective information protection involves three key areas: people, processes, and technology.
People
The information protection lifecycle involves several key roles. Your organization might not use these exact titles, but each role should be represented:
- Chief Information Security Officer (CISO): Oversees data security policies and procedures.
- Compliance Officer: Ensures regulatory compliance and defines controls.
- Data Admin: Implements classification policies per governance guidelines.
- Data Owner: Responsible for the data or process within the organization.
- Help Desk: Provides support for access and security issues.
- Information Worker: Creates and handles content, applying classification policies as needed.
Process
The process typically includes these phases:
- Define the data classification scheme: Establish a structure using sensitivity labels, trainable classifiers, and sensitive information types. Sensitivity labels can be applied manually or automatically based on content characteristics.
- Define classification policy conditions: Set rules for identifying and classifying data based on the defined scheme.
- Create, test, and deploy the classification policy: Configure and thoroughly test labels and policies before deployment.
- Ongoing usage, monitoring and remediation: Continuously review and adjust policies to ensure effectiveness and compliance.
Technology
Finally, using the right technology is crucial. Microsoft offers robust tools to help organizations meet their data classification, information protection, and lifecycle management requirements.
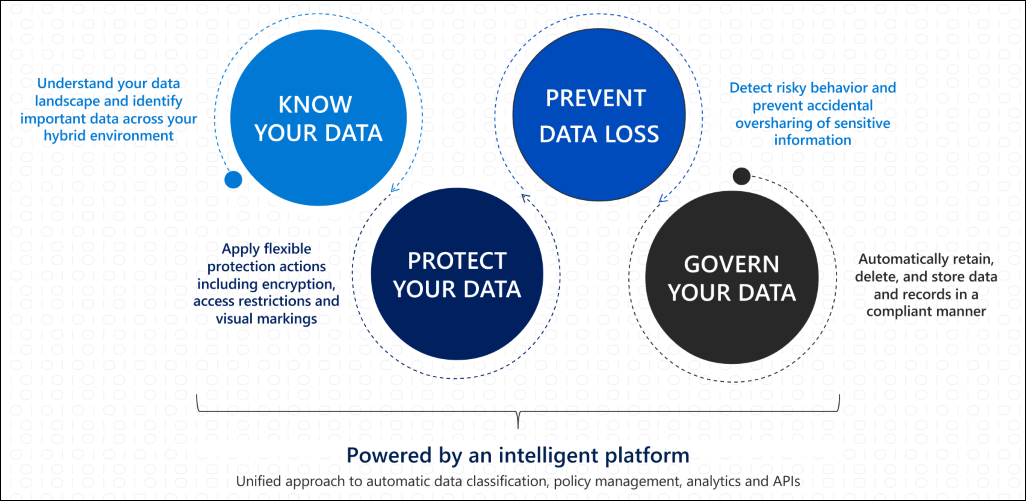
Know your data, protect your data, prevent data loss, and govern your data
Microsoft's approach to information protection and governance is centered around four principles:
- Know your data: Identify critical data across your environments.
- Protect your data: Apply encryption, access controls, and visual markings.
- Prevent data loss: Detect and prevent oversharing of sensitive information.
- Govern your data: Retain, delete, or archive data based on compliance rules.
These outcomes are powered by an intelligent platform that provides:
- A unified classification framework across environments.
- Centralized management for IT teams.
- Real-time analytics for monitoring and continuous improvement.
- APIs for extending governance capabilities into non-Microsoft apps.
As shown in the image, information protection is a continuous process, evolving as new data challenges arise.