@Allan J. Dela Pena
It sounds like you're using a PIM role when you mentioned activating an AzureAD Role. When using PIM, you can enable MFA by going to the actual role within PIM and enabling MFA on activation.
1.AzureAD Privileged Identity Management -> AzureAD Roles -> Role settings -> Select the specific role -> Settings -> Edit
2.From here you can require MFA "on activation"
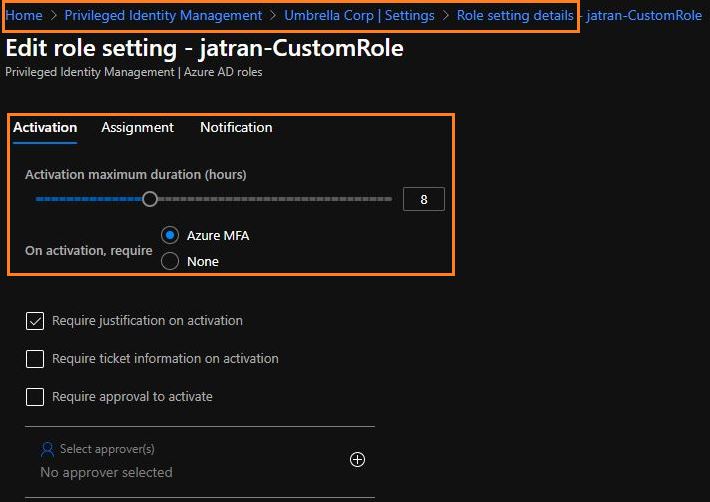
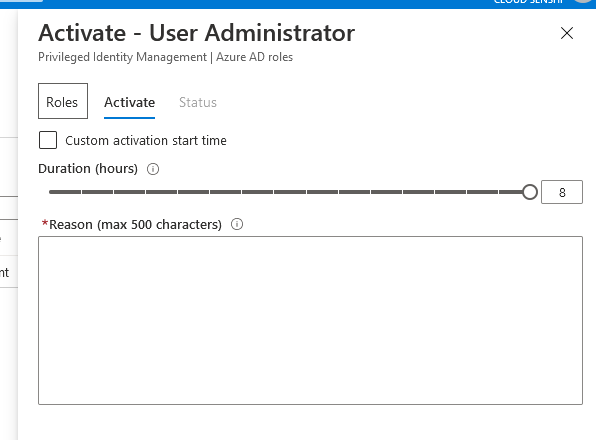
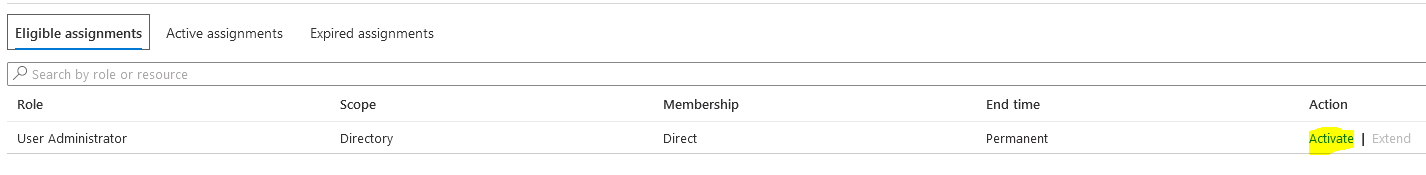
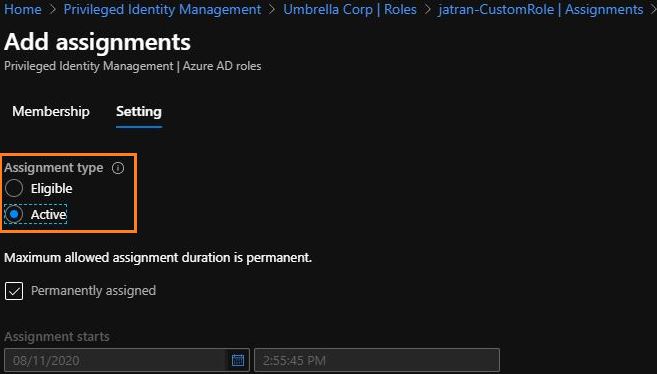
3.You can also activate roles "on active assignment", which doesn't require MFA.
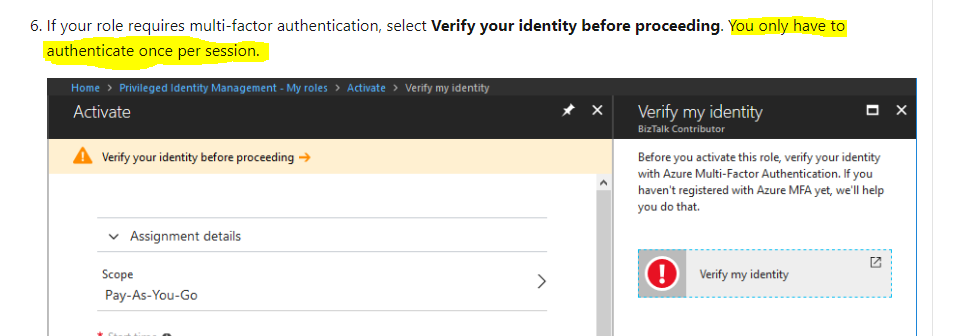
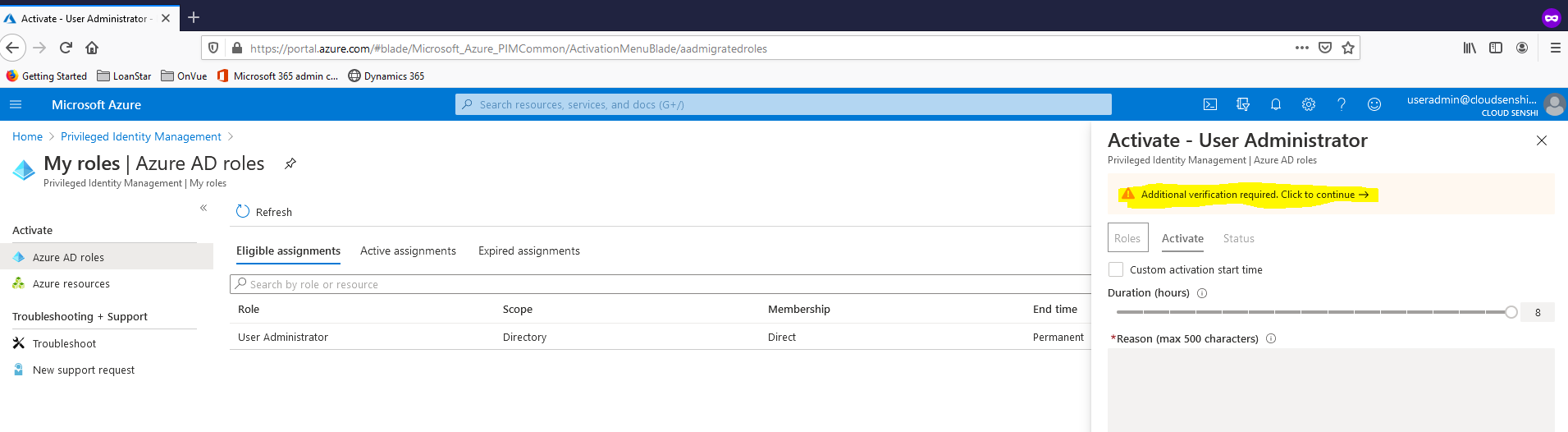
4.When activating a role within PIM, you will see a dialogue box on the Azure Portal prompting for additional verification/MFA.
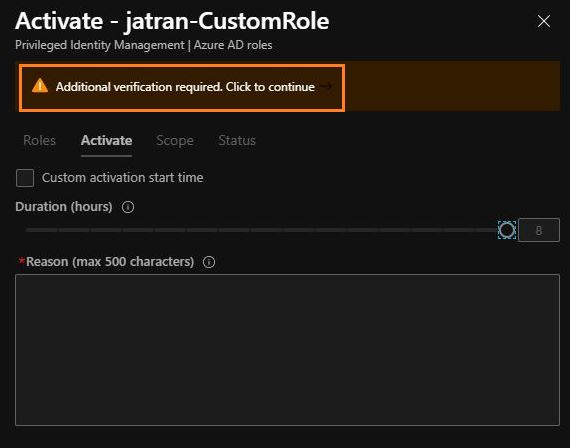
I hope this helps. Please let me know if you have any other questions.
Thank you for your time!