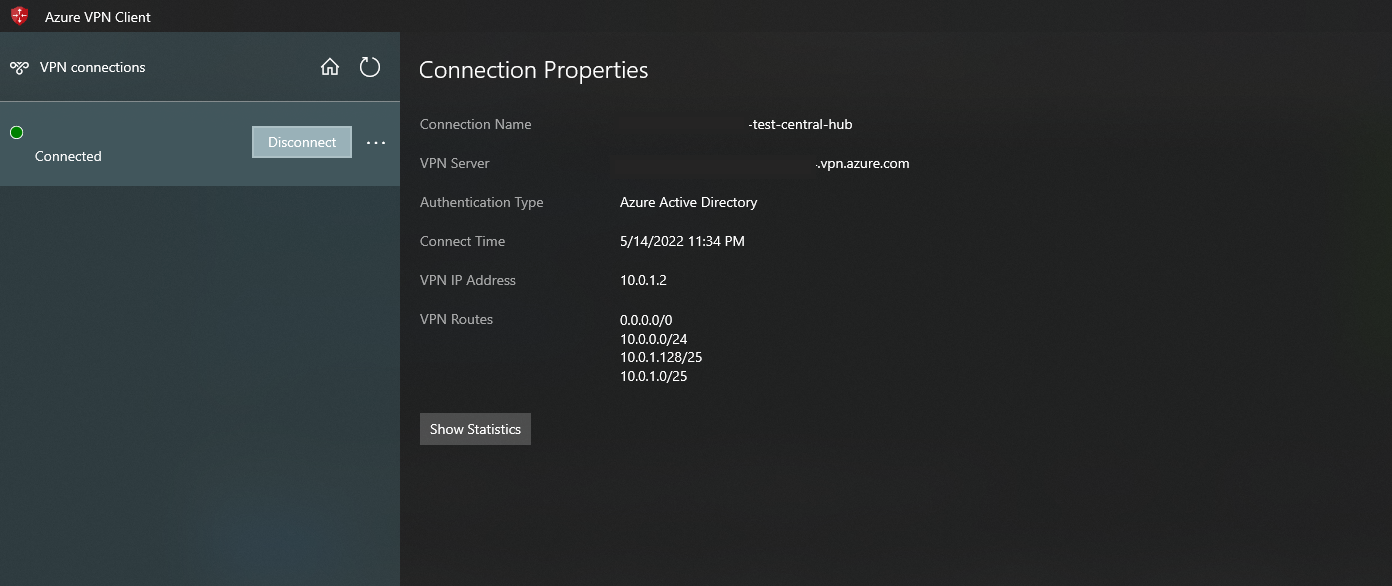
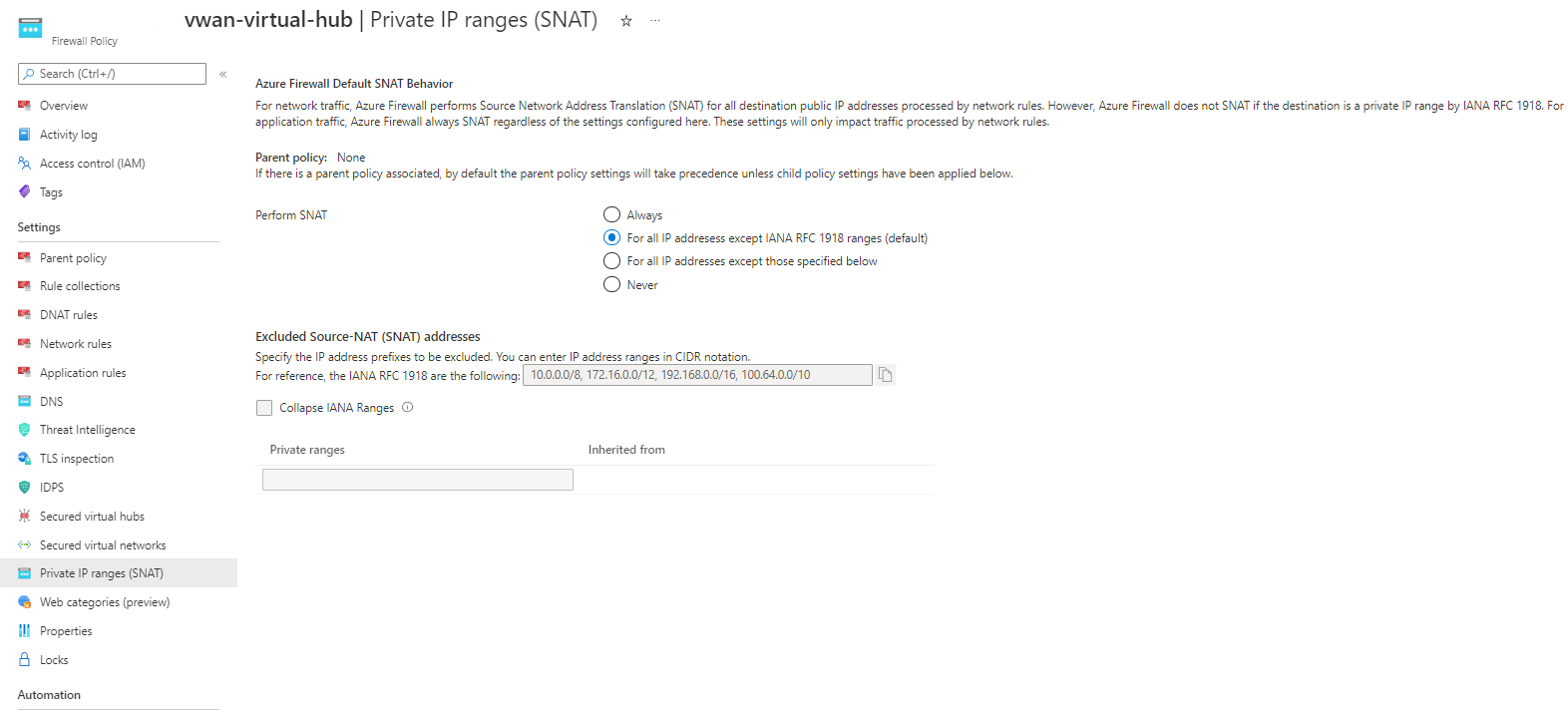
Hello @NSimpraga
Thank you for your patience on this.
I want to give my own observation for this set up.
For instance, I would like to provide this great and basic statement below:
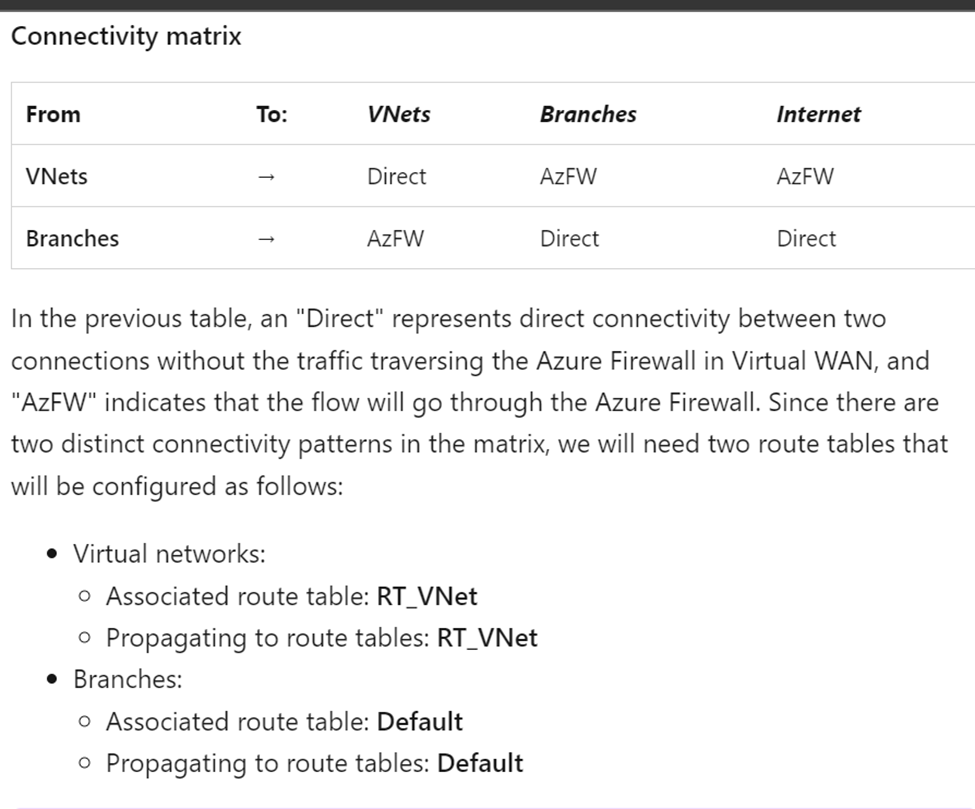
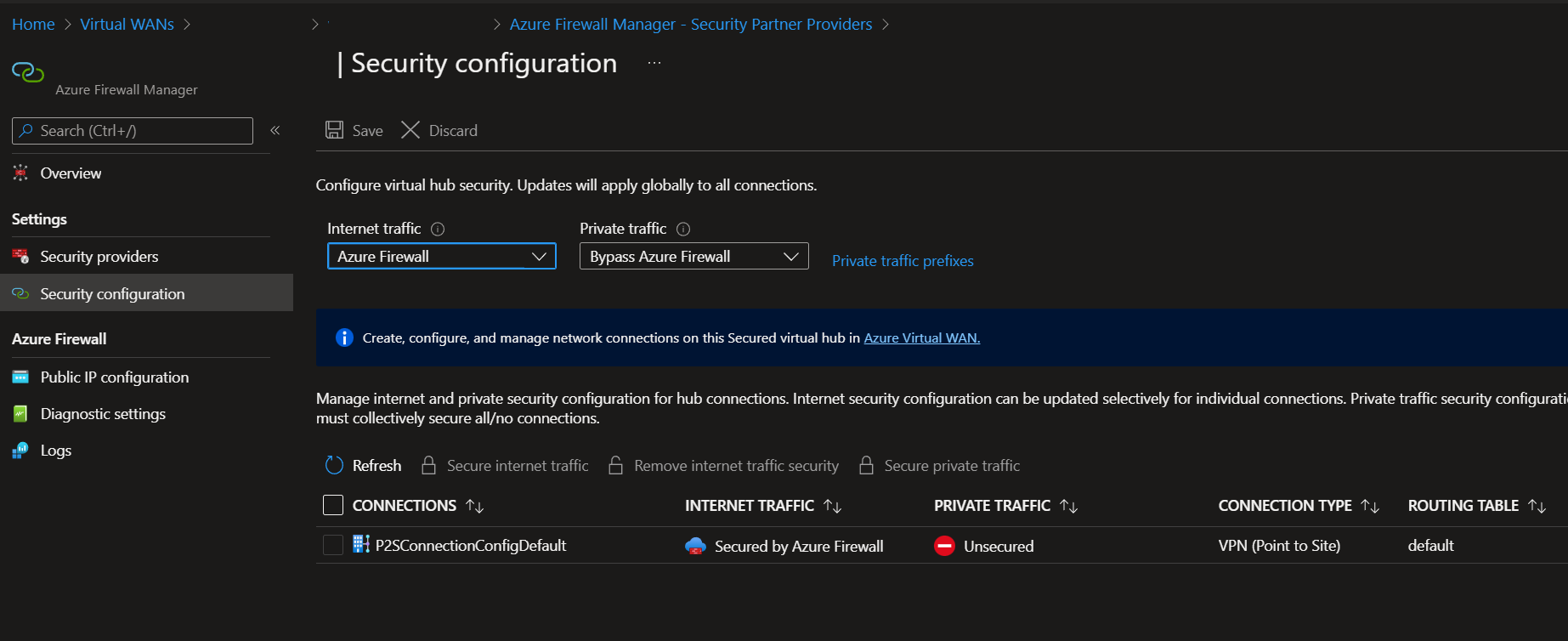
This is a great detail to keep in mind when forcing traffic being inspected from Azure Firewall.
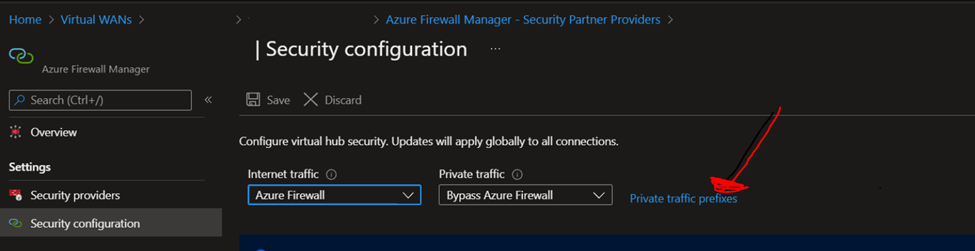
Private traffic prefixes can be also an IP Public address within your Azure environment.
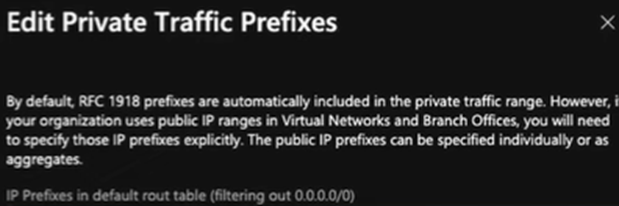
Once it is read, lets try to understand how to get this going as the way you intent or was planned.
For instance, I have the next observations below:
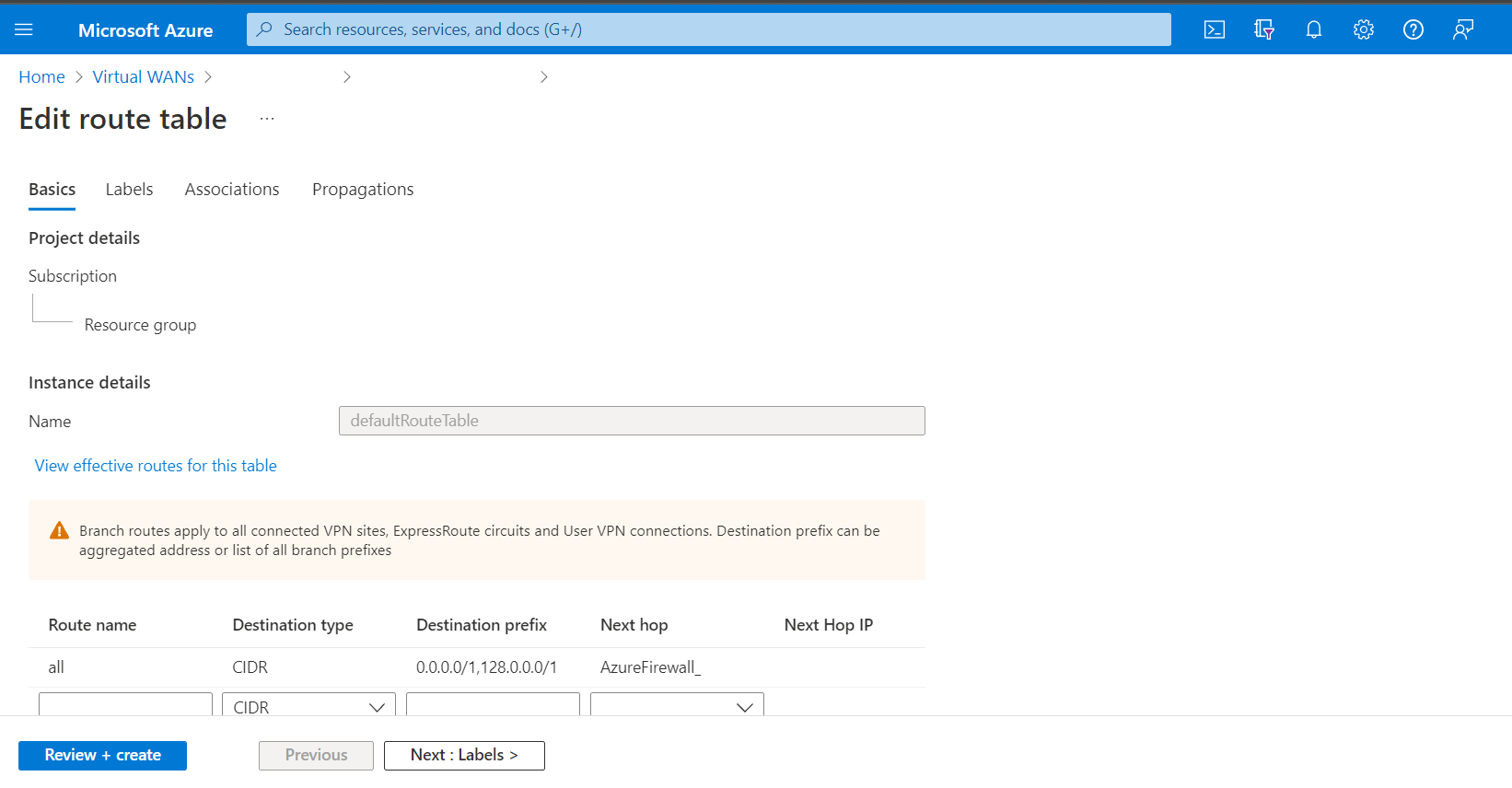
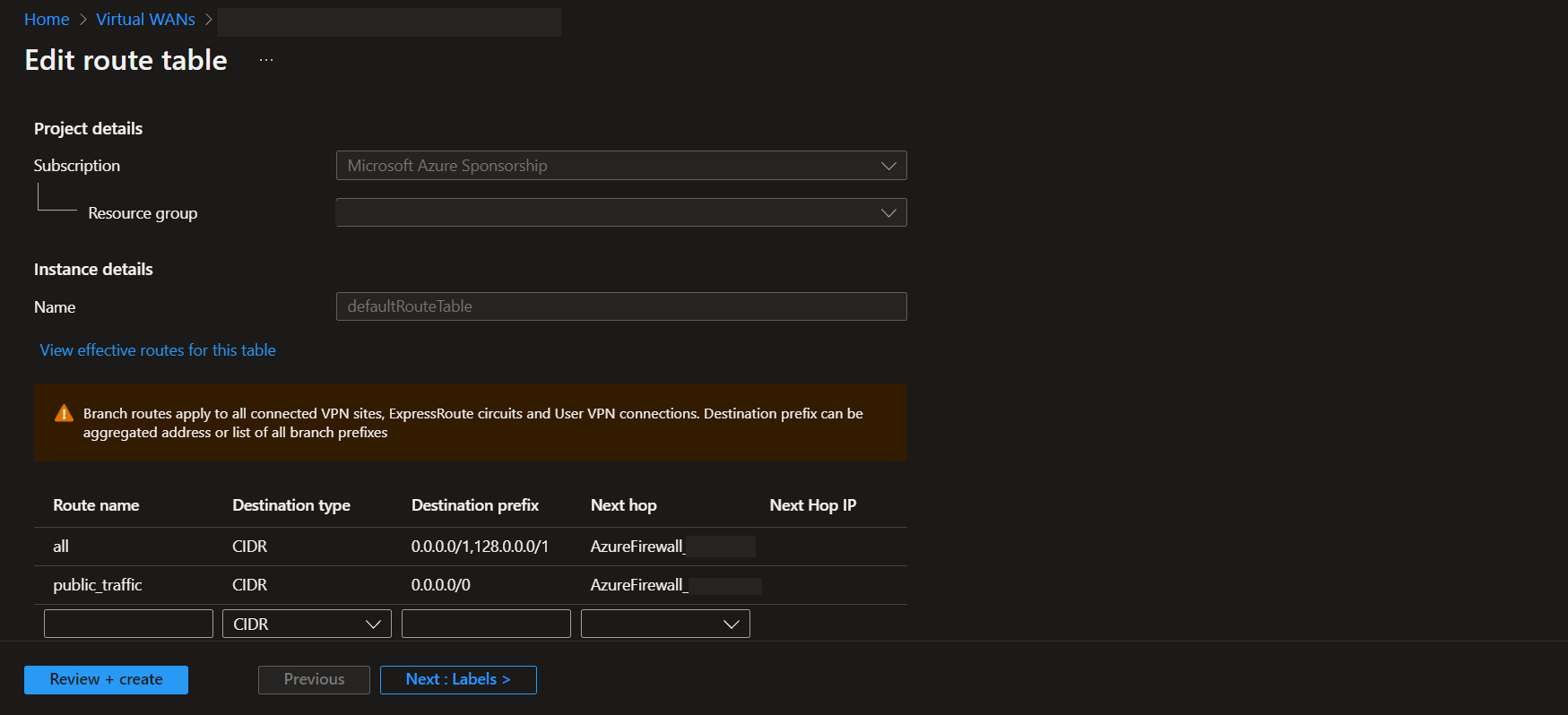
-Route propagation on PS2 tunnel can be applied to VNET-VNET peering using the BGP protocol(Also remember that if it is more than one VNET Peering so, you might be using allow transit and so on).
- Route propagation on PS2 tunnel can be applied to Local Gateway networks
- Route propagation on PS2 tunnel can be applied to virtual network address prefixes
-
- Routes learned from other BGP peering sessions connected to the Azure VPN gateway, except for the default route or routes that overlap with any virtual network prefix.
- Routes learned from other BGP peering sessions connected via ExpressRoute.
- Routes learned when propagation is enabled from custom route tables
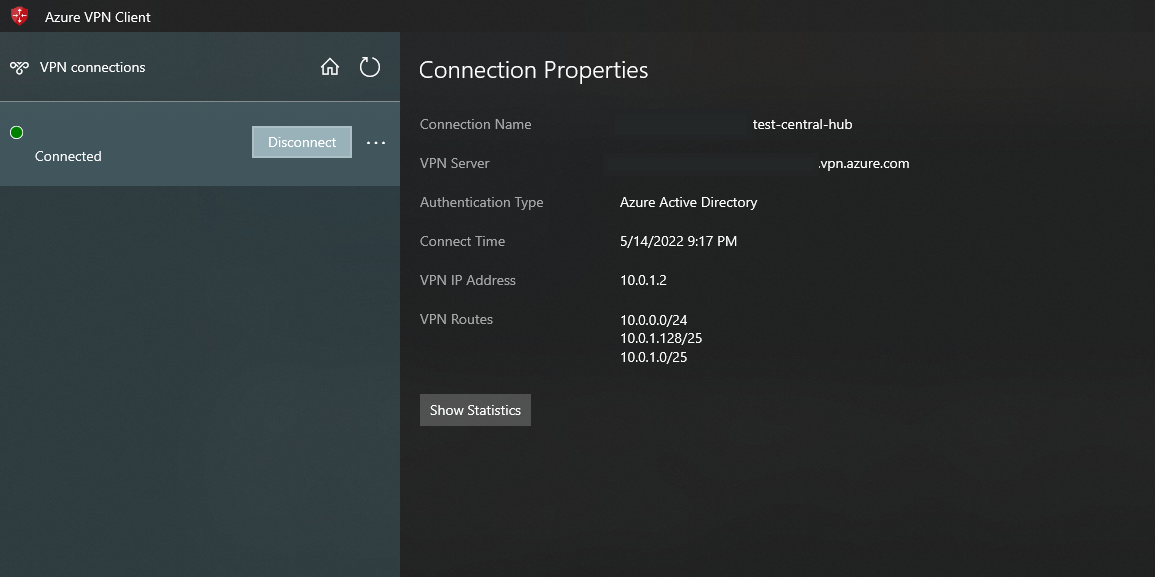
Having said that, I know that you are using a VIRTUAL WAN set up but the same expected behavior is happening as it is explained on the next page.
https://video2.skills-academy.com/en-us/azure/vpn-gateway/vpn-gateway-about-point-to-site-routing
Finally, I would say that the remaining option might be the one you implemented which is Manually on the VPN client configuration file, use an NVA or BGP route propagation from on-premises.
I hope this time the information provided before was useful as well as a good guidance to understand the behavior observed.
Best Regards,