Set up an identity management server: Windows Server 2016 or later versions
Note
Windows Server 2019 setup procedure does not differ from Windows Server 2016 setup procedure.
Note
This walkthrough uses sample names and values from a company called Contoso. Replace these with your own. For example:
- Domain controller name - corpdc
- Domain name - contoso
- MIM Service Server name - corpservice
- MIM Sync Server name - corpsync
- SQL Server name - corpsql
- Password - Pass@word1
Join Windows Server 2016 to your domain
Start with a Windows Server 2016 machine, with a minimum of 8-12GB of RAM. When installing specify "Windows Server 2016 Standard/Datacenter (Server with a GUI) x64" edition.
Log into the new computer as its administrator.
Using the Control Panel, give the computer a static IP address on the network. Configure that network interface to send DNS queries to the IP address of the domain controller in the previous step, and set the computer name to CORPSERVICE. This operation will require a server restart.
Open the Control Panel and join the computer to the domain that you configured in the last step, contoso.com. This operation includes providing the username and credentials of a domain administrator such as Contoso\Administrator. After the welcome message appears, close the dialog box and restart this server again.
Sign in to the computer CORPSERVICE as a domain account with local machine administrator such as Contoso\MIMINSTALL.
Launch a PowerShell window as administrator and type the following command to update the computer with the group policy settings.
gpupdate /force /target:computerAfter no more than a minute, it will complete with the message "Computer Policy update has completed successfully."
Add the Web Server (IIS) and Application Server roles, the .NET Framework 3.5, 4.0, and 4.5 features, and the Active Directory module for Windows PowerShell.
In PowerShell, type the following commands. Note that it may be necessary to specify a different location for the source files for .NET Framework 3.5 features. These features are typically not present when Windows Server installs, but are available in the side-by-side (SxS) folder on the OS install disk sources folder, e.g., “*d:\Sources\SxS*”.
import-module ServerManager Install-WindowsFeature Web-WebServer, Net-Framework-Features,rsat-ad-powershell,Web-Mgmt-Tools,Application-Server,Windows-Identity-Foundation,Server-Media-Foundation,Xps-Viewer –includeallsubfeature -restart -source d:\sources\SxS
Configure the server security policy
Set up the server security policy to allow the newly-created accounts to run as services.
Note
Depending on your configuration, single server(all-in-one) or distributed servers you only need to add, based on role of the member machine, like synchronization server.
Launch the Local Security Policy program
Navigate to Local Policies > User Rights Assignment.
On the details pane, right-click on Log on as a service, and select Properties.
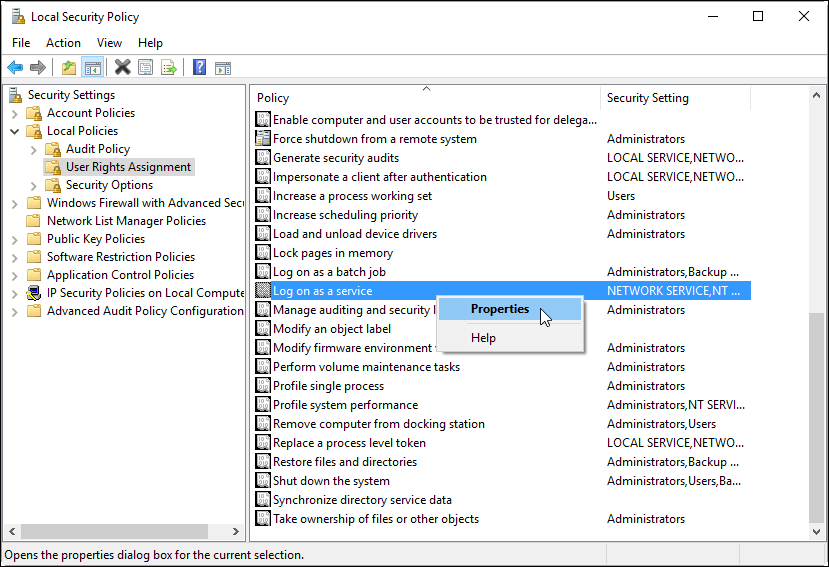
Click Add User or Group, and in the text box type following based on role
contoso\MIMSync; contoso\MIMMA; contoso\MIMService; contoso\SharePoint; contoso\SqlServer; contoso\MIMSSPR, click Check Names, and click OK.Click OK to close the Log on as a service Properties window.
On the details pane, right-click on Deny access to this computer from the network, and select Properties.>
Click Add User or Group, and in the text box type
contoso\MIMSync; contoso\MIMServiceand click OK.Click OK to close the Deny access to this computer from the network Properties window.
On the details pane, right-click on Deny log on locally, and select Properties.
Click Add User or Group, and in the text box type
contoso\MIMSync; contoso\MIMServiceand click OK.Click OK to close the Deny log on locally Properties window.
Close the Local Security Policy window.
Software prerequisites
Before installing MIM 2016 SP2 components please make sure you install all software prerequisites:
Install .NET Framework 4.6.
On the server that will host MIM Synchronization Service, MIM Synchronization Service requires SQL Server Native Client.
On the server that will host MIM Service, MIM Service requires .NET Framework 3.5.
Optionally, if using TLS 1.2 or FIPS mode, see MIM 2016 SP2 in "TLS 1.2 only" or FIPS-mode environments.
Change the IIS Windows Authentication mode if needed
Open a PowerShell window.
Stop IIS with the command iisreset /STOP
iisreset /STOP C:\Windows\System32\inetsrv\appcmd.exe unlock config /section:windowsAuthentication -commit:apphost iisreset /START