Microsoft Entra Connect and Microsoft Entra Connect Health installation roadmap
Install Microsoft Entra Connect
Important
Microsoft doesn't support modifying or operating Microsoft Entra Connect Sync outside of the actions that are formally documented. Any of these actions might result in an inconsistent or unsupported state of Microsoft Entra Connect Sync. As a result, Microsoft can't provide technical support for such deployments.
You can find the download for Microsoft Entra Connect on Microsoft Download Center.
| Solution | Scenario |
|---|---|
| Before you start - Hardware and prerequisites | |
| Express settings | |
| Customized settings | |
| Upgrade from DirSync | |
| Upgrade from Azure AD Sync or Microsoft Entra Connect |
After installation, you should verify it's working as expected and assign licenses to the users.
Next steps to Install Microsoft Entra Connect
| Topic | Link |
|---|---|
| Download Microsoft Entra Connect | Download Microsoft Entra Connect |
| Install using Express settings | Express installation of Microsoft Entra Connect |
| Install using Customized settings | Custom installation of Microsoft Entra Connect |
| Upgrade from DirSync | Upgrade from Azure AD Sync tool (DirSync) |
| After installation | Verify the installation and assign licenses |
Learn more about Install Microsoft Entra Connect
You also want to prepare for operational concerns. You might want to have a stand-by server so you easily can fail over if there's a disaster. If you plan to make frequent configuration changes, you should plan for a staging mode server.
| Topic | Link |
|---|---|
| Supported topologies | Topologies for Microsoft Entra Connect |
| Design concepts | Microsoft Entra Connect design concepts |
| Accounts used for installation | More about Microsoft Entra Connect credentials and permissions |
| Operational planning | Microsoft Entra Connect Sync: Operational tasks and considerations |
| User sign-in options | Microsoft Entra Connect User sign-in options |
Configure sync features
Microsoft Entra Connect comes with several features you can optionally turn on or are enabled by default. Some features might sometimes require more configuration in certain scenarios and topologies.
Filtering is used when you want to limit which objects are synchronized to Microsoft Entra ID. By default all users, contacts, groups, and Windows 10 computers are synchronized. You can change the filtering based on domains, OUs, or attributes.
Password hash synchronization synchronizes the password hash in Active Directory to Microsoft Entra ID. The end-user can use the same password on-premises and in the cloud but only manage it in one location. Since it uses your on-premises Active Directory as the authority, you can also use your own password policy.
Password writeback allows your users to change and reset their passwords in the cloud and have your on-premises password policy applied.
Device writeback allows a device registered in Microsoft Entra ID to be written back to on-premises Active Directory so it can be used for Conditional Access.
The prevent accidental deletes feature is turned on by default and protects your cloud directory from numerous deletes at the same time. By default it allows 500 deletes per run. You can change this setting depending on your organization size.
Automatic upgrade is enabled by default for express settings installations and ensures your Microsoft Entra Connect is always up to date with the latest release.
Next steps to configure sync features
| Topic | Link |
|---|---|
| Configure filtering | Microsoft Entra Connect Sync: Configure filtering |
| Password hash synchronization | Password hash synchronization |
| Pass-through Authentication | Pass-through authentication |
| Password writeback | Getting started with password management |
| Device writeback | Enabling device writeback in Microsoft Entra Connect |
| Prevent accidental deletes | Microsoft Entra Connect Sync: Prevent accidental deletes |
| Automatic upgrade | Microsoft Entra Connect: Automatic upgrade |
Customize Microsoft Entra Connect Sync
Microsoft Entra Connect Sync comes with a default configuration that is intended to work for most customers and topologies. But there are always situations where the default configuration doesn't work and must be adjusted. It's supported to make changes as documented in this section and linked topics.
If you haven't worked with a synchronization topology before you want to start to understand the basics and the terms used as described in the technical concepts. Even if some things are similar, a lot has changed as well.
The default configuration assumes there might be more than one forest in the configuration. In those topologies, a user object might be represented as a contact in another forest. The user might also have a linked mailbox in another resource forest. The behavior of the default configuration is described in users and contacts.
The configuration model in sync is called declarative provisioning. The advanced attribute flows are using functions to express attribute transformations. You can see and examine the entire configuration using tools which comes with Microsoft Entra Connect. If you need to make configuration changes, make sure you follow the best practices so it's easier to adopt new releases.
Next steps to customize Microsoft Entra Connect Sync
| Topic | Link |
|---|---|
| All Microsoft Entra Connect Sync articles | Microsoft Entra Connect Sync |
| Technical concepts | Microsoft Entra Connect Sync: Technical Concepts |
| Understanding the default configuration | Microsoft Entra Connect Sync: Understanding the default configuration |
| Understanding users and contacts | Microsoft Entra Connect Sync: Understanding Users and Contacts |
| Declarative provisioning | Microsoft Entra Connect Sync: Understanding Declarative Provisioning Expressions |
| Change the default configuration | Best practices for changing the default configuration |
Configure federation features
Microsoft Entra Connect provides several features that simplify federating with Microsoft Entra ID using AD FS and managing your federation trust. Microsoft Entra Connect supports AD FS on Windows Server 2012R2 or later.
Update TLS/SSL certificate of AD FS farm even if you are not using Microsoft Entra Connect to manage your federation trust.
Add an AD FS server to your farm to expand the farm as required.
Repair the trust with Microsoft Entra ID in a few simple clicks.
ADFS can be configured to support multiple domains. For example, you might have multiple top domains you need to use for federation.
If your ADFS server isn't configured to update certificates from Microsoft Entra ID automatically, or if you use a non-ADFS solution, then you'll be notified when you have to update certificates.
Next steps to configure federation features
| Topic | Link |
|---|---|
| All AD FS articles | Microsoft Entra Connect and federation |
| Configure ADFS with subdomains | Multiple Domain Support for Federating with Microsoft Entra ID |
| Manage AD FS farm | AD FS management and customization with Microsoft Entra Connect |
| Manually updating federation certificates | Renewing Federation Certificates for Microsoft 365 and Microsoft Entra ID |
Get started with Microsoft Entra Connect Health
To get started with Microsoft Entra Connect Health, use the following steps:
- Get Microsoft Entra ID P1 or P2 or start a trial.
- Download and install Microsoft Entra Connect Health Agents on your identity servers.
- View the Microsoft Entra Connect Health dashboard at https://aka.ms/aadconnecthealth.
Note
Remember that before you see data in your Microsoft Entra Connect Health dashboard, you need to install the Microsoft Entra Connect Health Agents on your targeted servers.
Download and install Microsoft Entra Connect Health Agent
- Make sure that you satisfy the requirements for Microsoft Entra Connect Health.
- Get started using Microsoft Entra Connect Health for AD FS
- Get started using Microsoft Entra Connect Health for sync
- Download and install the latest version of Microsoft Entra Connect. The Health Agent for sync is installed as part of the Microsoft Entra Connect installation (version 1.0.9125.0 or higher).
- Get started using Microsoft Entra Connect Health for AD DS
Microsoft Entra Connect Health portal
The Microsoft Entra Connect Health portal shows views of alerts, performance monitoring, and usage analytics. The https://aka.ms/aadconnecthealth URL takes you to the main blade of Microsoft Entra Connect Health. You can think of a blade as a window. On The main blade, you see Quick Start, services within Microsoft Entra Connect Health, and additional configuration options. See the following screenshot and brief explanations that follow the screenshot. After you deploy the agents, the health service automatically identifies the services that Microsoft Entra Connect Health is monitoring.
Note
For licensing information, see the Microsoft Entra Connect Health FAQ or the Microsoft Entra pricing page.
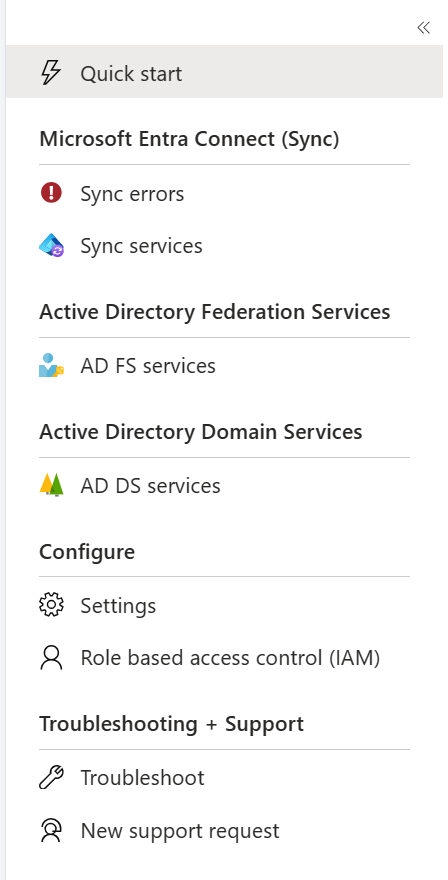
- Quick Start: When you select this option, the Quick Start blade opens. You can download the Microsoft Entra Connect Health Agent by selecting Get Tools. You can also access documentation and provide feedback.
- Microsoft Entra Connect (sync): This option shows your Microsoft Entra Connect servers that Microsoft Entra Connect Health is currently monitoring. Sync errors entry shows basic sync errors of your first onboarded sync service by categories. When you select the Sync services entry, the blade that opens shows information about your Microsoft Entra Connect servers. Read more about the capabilities at Using Microsoft Entra Connect Health for sync.
- Active Directory Federation Services: This option shows all the AD FS services that Microsoft Entra Connect Health is currently monitoring. When you select an instance, the blade that opens shows information about that service instance. This information includes an overview, properties, alerts, monitoring, and usage analytics. Read more about the capabilities at Using Microsoft Entra Connect Health with AD FS.
- Active Directory Domain Services: This option shows all the AD DS forests that Microsoft Entra Connect Health is currently monitoring. When you select a forest, the blade that opens shows information about that forest. This information includes an overview of essential information, the Domain Controllers dashboard, the Replication Status dashboard, alerts, and monitoring. Read more about the capabilities at Using Microsoft Entra Connect Health with AD DS.
- Configure: This section includes options to turn the following on or off:
- Access to data from the Microsoft Entra directory integrity by Microsoft only for troubleshooting purposes: if this option is enabled, Microsoft can access the same data viewed by the user. This information can be useful for troubleshooting and to provide the necessary assistance. This option is disabled by default
- Role based access control (IAM) is the section to manage the access to Connect Health data in role base.